Managing Security Issues¶
Security issues (vulnerabilities) are security flaws in an infrastructure that may be exploited by attackers to perform unauthorized malicious actions with your system. Wallarm employs various techniques to discover security issues. This article describes how to analyze and manage security in Wallarm Console.
Exploring security issues¶
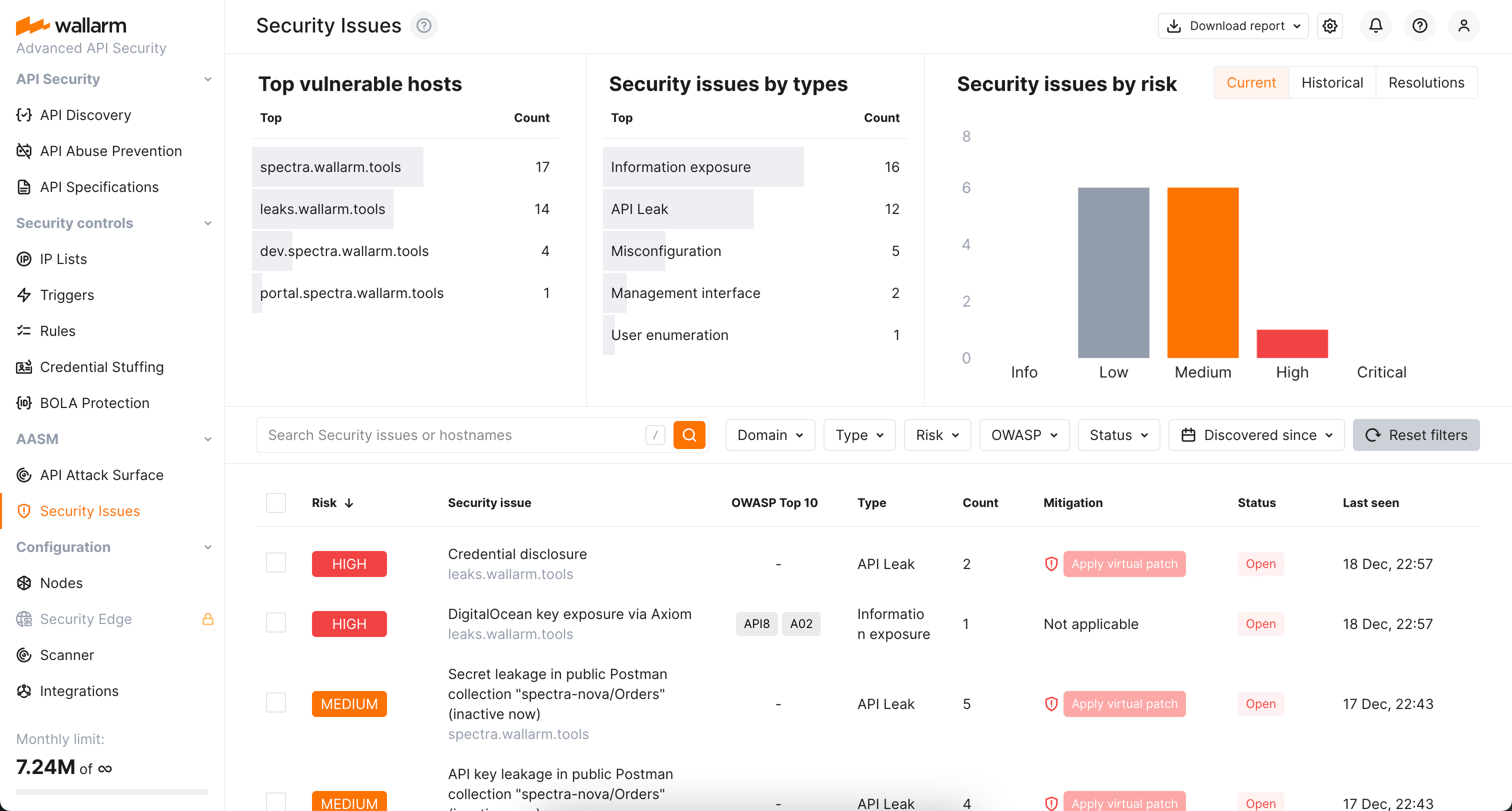
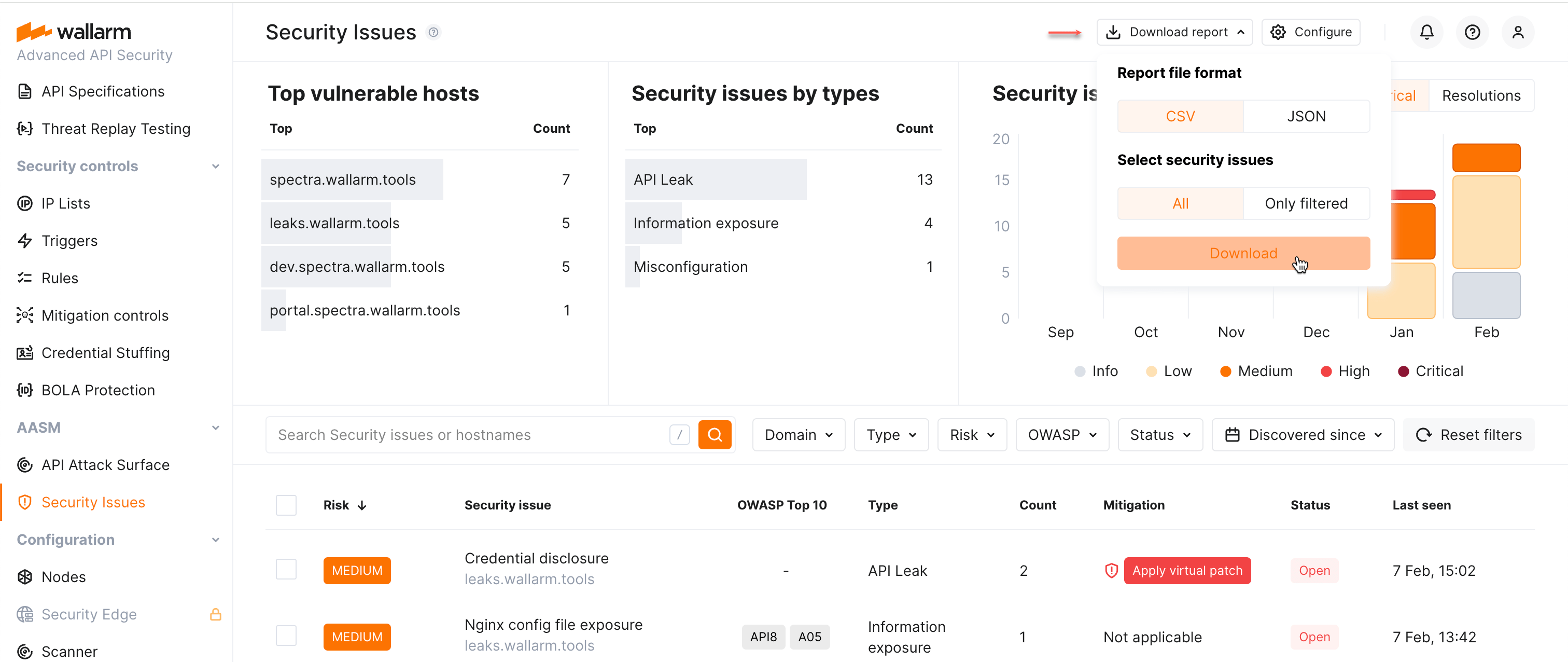
To explore and manage the found security issues, in Wallarm Console, go to the Security Issues section.
Here, the detailed information on found issues is presented, including:
-
Full filterable list of issues with brief and detailed description of each
-
Top vulnerable hosts list
-
Distribution of security issues by type
-
Risk level evaluation and distribution of security issues by these levels
-
Monthly historical information on detected and resolved issues for the last 6 month
Issue details and lifecycle¶
Wallarm provides detailed information on each detected security issues to allow clear understanding of what is happening and what can be done.
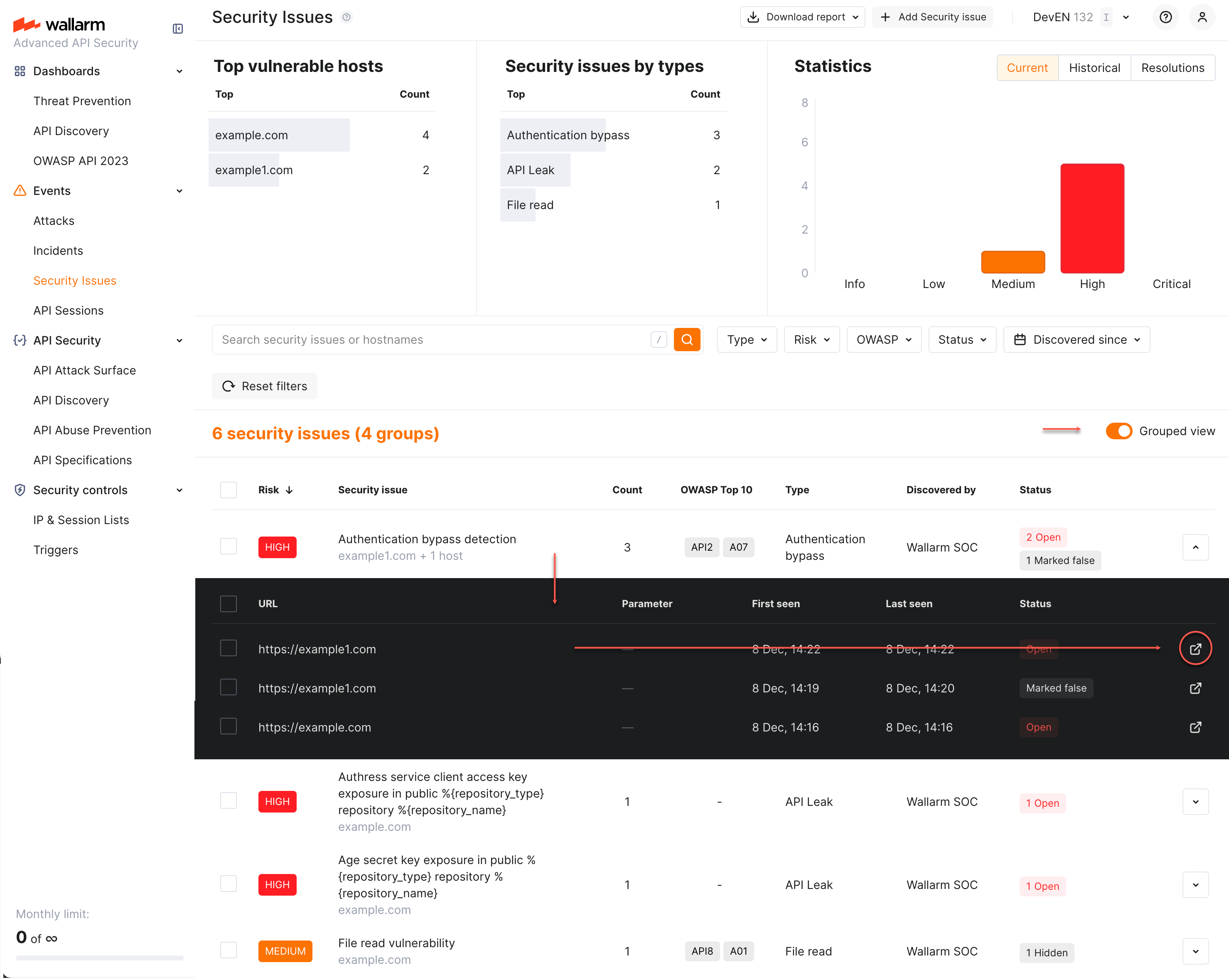
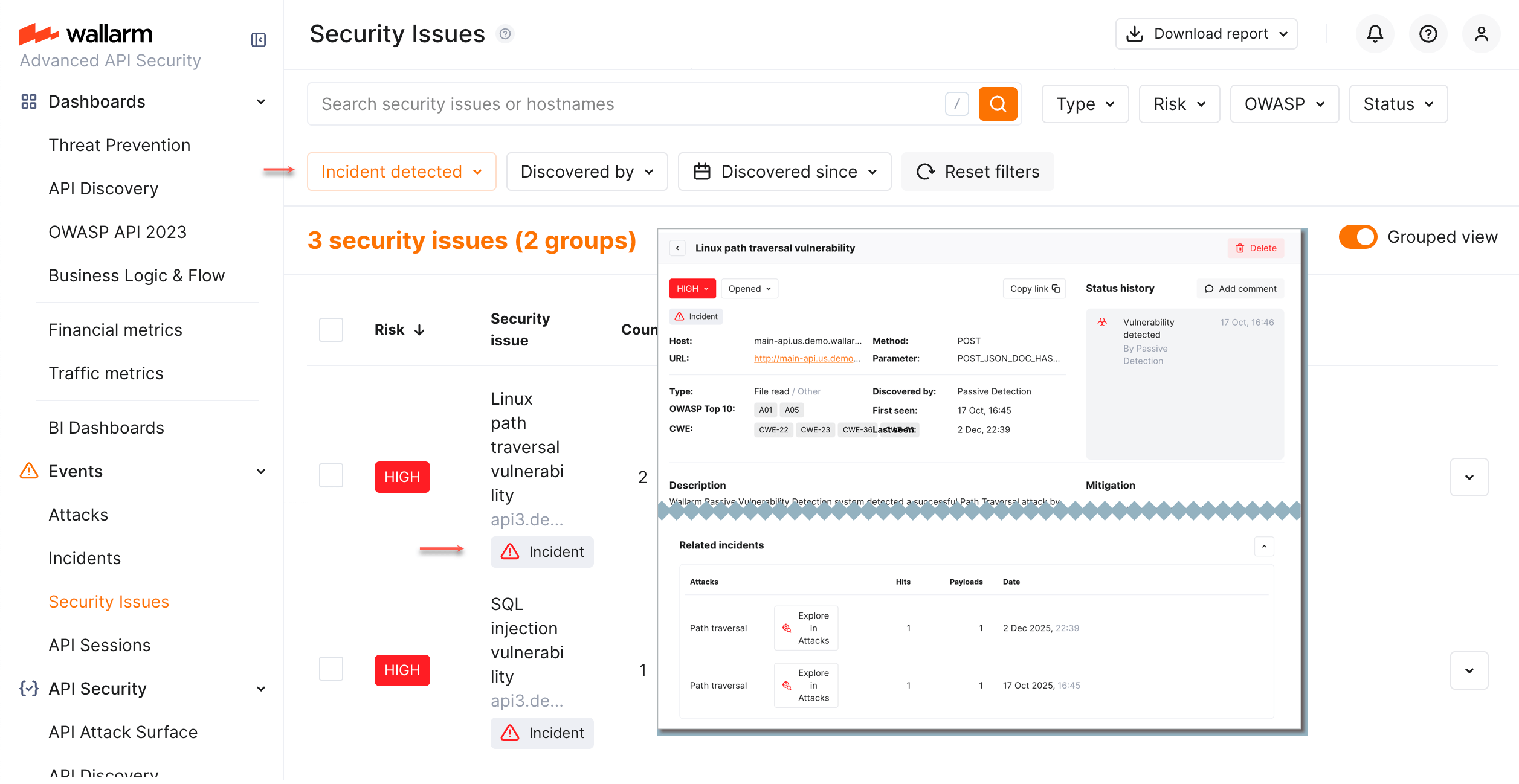
Grouped view¶
By default, alike security issues are grouped (Grouped view), if they:
-
Have the same title (Security issue column)
-
Have the same risk level (Risk column)
-
Discovered by the same tool (Discovered by column)
You can:
-
See the number of issues in the group (Count column)
-
See all statuses within the group
-
Click group to expand
-
Open each issue in a new window
-
Disable/re-enable grouped view with Grouped view switcher
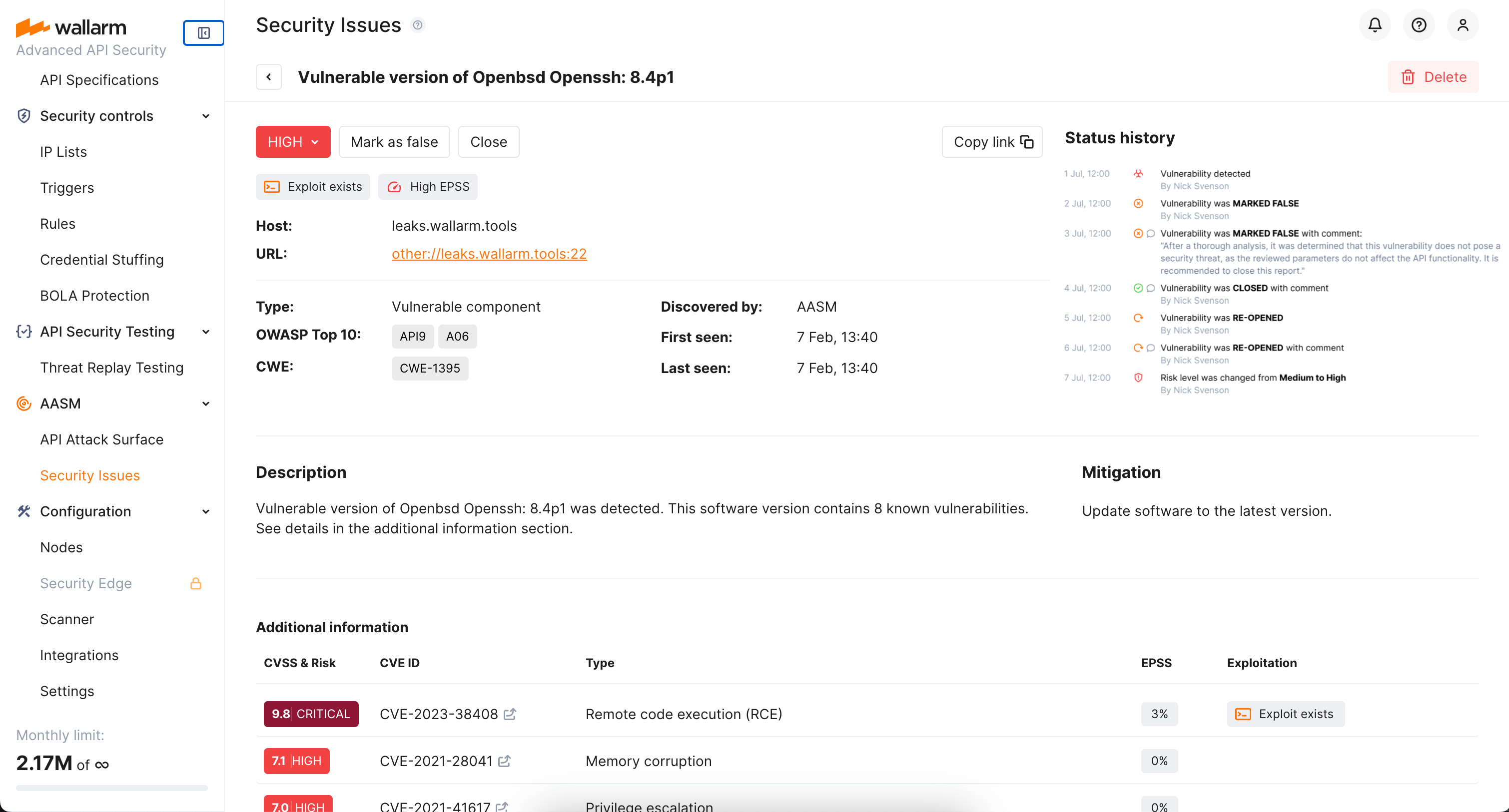
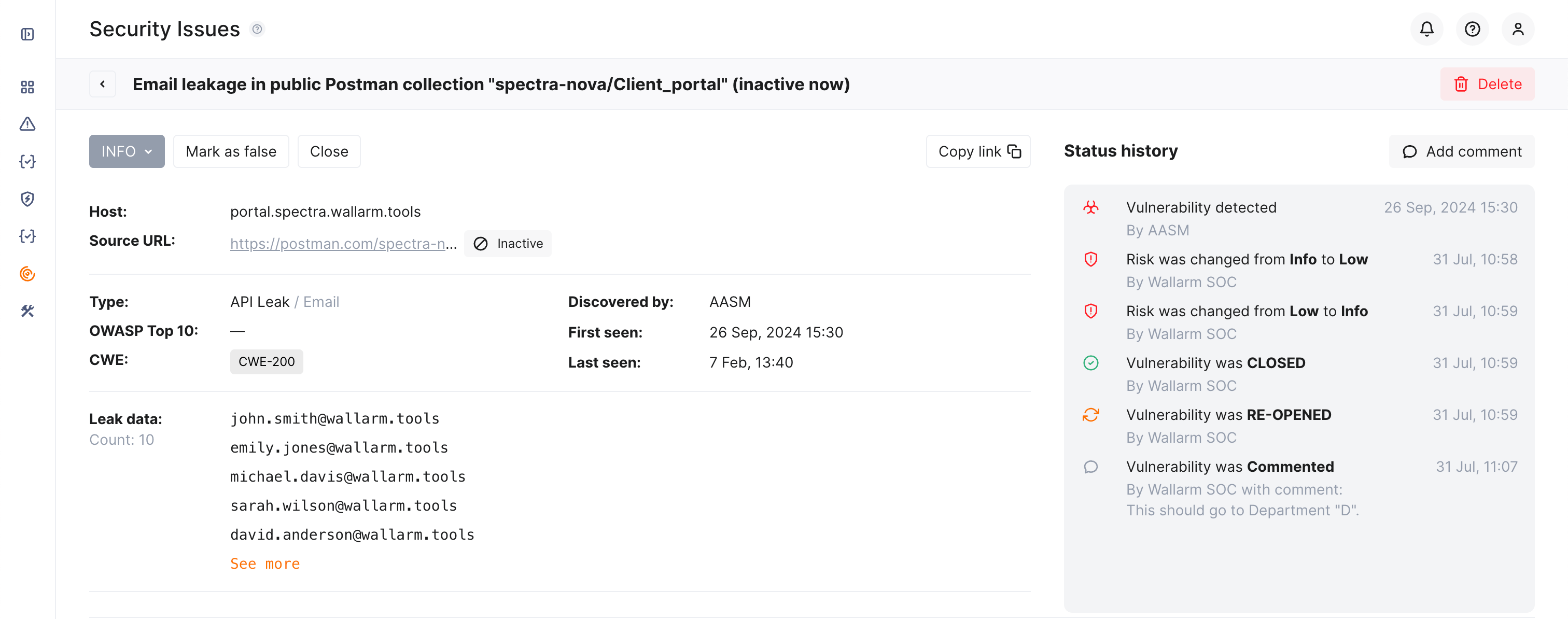
Issue details¶
Open issue to see its details, such as:
- Basic info (type, host and url, first and last seen time)
- Detailed Description
- Measures for Mitigation
- Information on linked CVEs ranked by risk as Additional information
Issue lifecycle¶
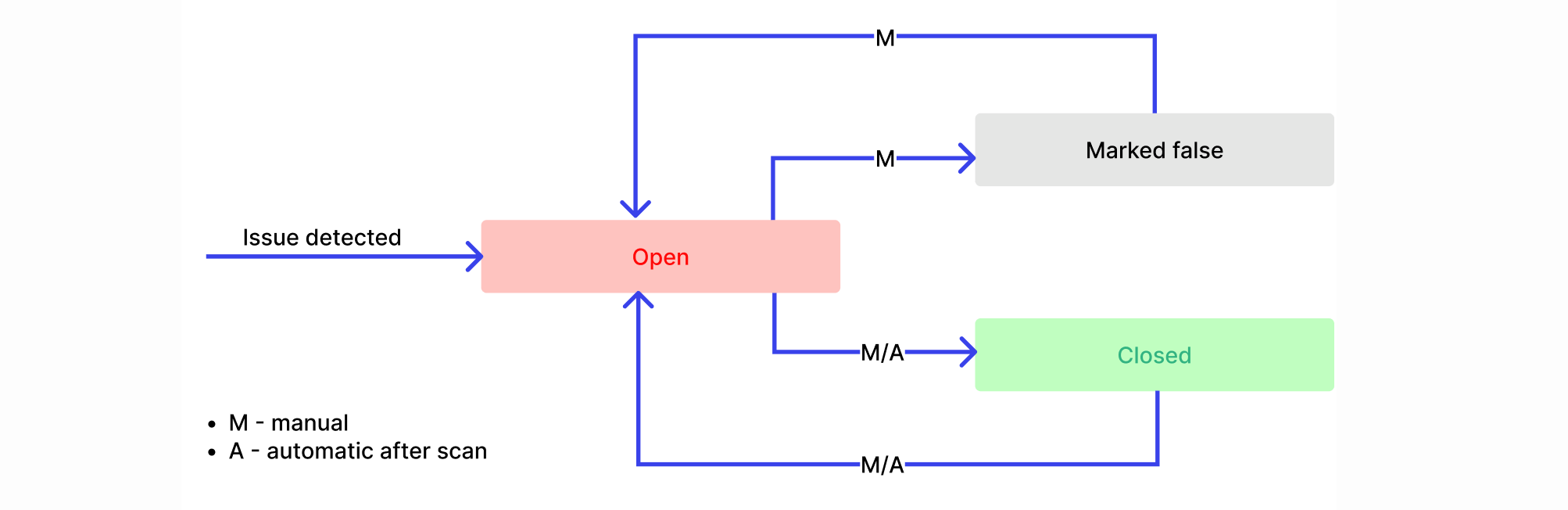
Once a security issue is detected, it obtains the Open status meaning some measures are required to mitigate it. In the issue details, you can close it (means it was resolved) or mark as false.
It is useful to provide comment on each status change, giving others the full view of what is the reason of change. Author and time of change are tracked automatically.
Security issues can be closed by Wallarm automatically after next automatic or manual rescan in the following cases:
-
Port not found during last scan
-
Network service has changed
-
New version of the product detected
-
Vulnerable version no longer present
-
Vulnerability not detected during last scan
Issues can be re-opened automatically after next rescan or manually. Note that issues marked as false are never re-opened automatically.
Changing risk level¶
If you re-evaluate the risk level of the issue, go to its details and select new risk level from the list.
Adding comments¶
While it is always useful to provide comment on status change (closing, re-opening), you can add any comments to the issue at any moment without changing anything else. To do so, use the Add comment button: your comment will become the part of Status history.
Status history¶
For you to be on track, the full history of changes and comments is displayed in the Status history section of the security issue.
Issue risk level¶
Risk level¶
Each discovered security issue is automatically assessed by how much risk it poses as described in the table.
| Risk | Description | Examples |
|---|---|---|
| Critical | The vulnerability's presence may lead to a system compromise, allowing an attacker to remotely execute code or cause a denial of service (DoS) or service degradation. Immediate reaction is required. |
|
| High | The presence of the vulnerability may lead to partial system compromise, such as database access or limited access to the filesystem. In specific circumstances (e.g., if special requirements are met or if chained with other vulnerabilities), the vulnerability may lead to system compromise (e.g., remote code execution). |
|
| Medium | The vulnerability may lead to bypassing security controls, limited exposure or access, but without full compromise. It can allow access to sensitive data or configurations and potentially be leveraged in a more complex attack chain. |
|
| Low | The vulnerability has minimal impact and does not directly lead to significant damage or exploitation as requirements/conditions are too complex. However, it can be combined with other vulnerabilities to escalate an attack. |
|
| Info | The issue does not pose an immediate security risk but should still be reviewed for potential manual validation. It often involves exposure of non-critical data or violation of best practices. |
|
* If the software version contains multiple CVEs, including critical ones, the overall risk level is assessed as high. The risk level is reduced by one level because the presence of a vulnerable version does not explicitly indicate the existence of the vulnerability. For example, the vulnerability may occur only in a specific, non-default configuration or require certain conditions to be met.
You can re-evaluate and manually adjust the risk level at any moment.
Presence of incidents¶
Incidents are attacks that successfully exploited the security issue (vulnerability). These attacks were detected, but not blocked by Wallarm due to the current settings (monitoring filtration mode or others).
Presence of incidents indicates jump from a theoretical risk to a live threat and requires prioritizing fixes of these security issues:
-
Once a vulnerability is successfully exploited, it often becomes public knowledge in the hacker community.
-
If one attacker succeeds, others will use the same method. An incident indicates that your system is now a confirmed target.
-
Incidents are the subject of investigation to find out data losses or other damages.
Analyze incidents presence and impact:
-
Pay attention to the issues having
Incidenttag in the Security issue column. -
Set the Incident filter to
Incident detectedto see all issues with incidents. Go to issue details, view the Related incidents section. From here, you can go to every incident details.
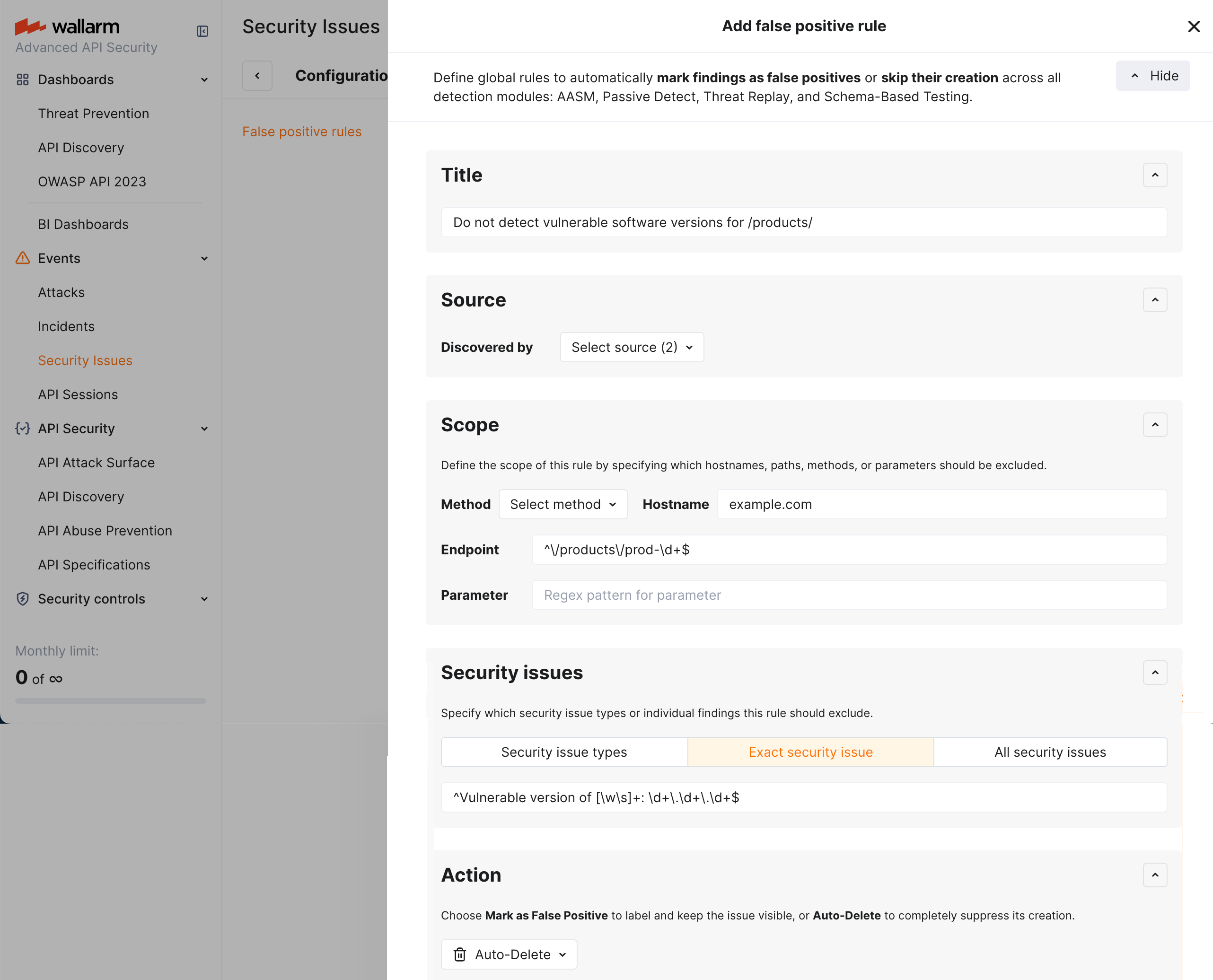
False positive rules¶
Define global rules to automatically mark findings as false positives or skip their creation across all detection methods: passive detection, AASM, Threat Replay, and Schema-Based Testing. For an overview of false positives and manual marking, see False positives in Detecting Security Issues.
To manage rules, go to Security Issues → Configure → False positive rules. Use the search field to find rules by title.
Creating a rule¶
You can create a false positive rule in two ways:
-
From scratch: Click Add false positive rule and configure all rule parameters in the drawer
-
From a security issue: Open the issue details and use Ignore similar issues—the rule fields will be pre-filled from the selected issue
Rule configuration¶
The rule allows you:
-
To specify, for security issues found for the selected hosts, endpoints, or parameters (Scope), whether to mark some or all of them (Security issues) as false positives or completely suppress their creation (Action).
-
You can also select whether this applies to issues found by any detection method or only by specific ones (Source).
-
When you want only specific issues to be treated this way, you can specify which by type(s) or by title matching a regex pattern (Security issues).
| Section | Description |
|---|---|
| Title | Set a custom title for the rule to identify it in the rules list. |
| Source | Decide whether to apply the rule to security issues found by any method or only by specific ones. If left blank, the rule is applied to security issues found by any method. |
| Scope | Define which hosts, endpoints, and parameters this rule should be applied to. Only findings from there will be affected by the rule. If left blank, the rule is applied to all hosts, endpoints, and parameters. Use Hostname, Endpoint, and Parameter fields to enter regex patterns for each. |
| Security issues | Specify to what findings for Scope the rule's Action should be applied. Use SI with specific title(s) tab to enter regex pattern for security issue titles, or SI of specific type(s) tab to select security issue types. |
| Action | Choose Mark as false positive to label and keep the issue visible, or Auto-delete to completely suppress its creation. |
Click Add to save the rule.
Note that:
-
If a vulnerability is automatically marked as false by a rule, the status change is logged in the issue's Status history
-
False positive rules work for all detection methods: AASM, Threat Replay Testing, Passive detection, Schema-Based Testing
-
False positive rules act as a pre-creation filter—they are evaluated before security issues are created
Previously detected issues
When you create a new false positive rule, it does not retroactively mark previously detected security issues that match the rule as false—only new detections are affected. If an issue was detected before the rule was created, and you then add the rule and the same security issue is detected again later, the rule will be applied to that new detection.
Example¶
To suppress vulnerable software version findings for product endpoints:
| Section | Parameter | Value |
|---|---|---|
| Title | — | Do not detect vulnerable software versions for /products/ |
| Source | — | AASM, TRT |
| Scope | Hostname | example.com |
| Scope | Endpoint | ^\/products\/prod-\d+$ |
| Security issues | SI with specific title(s) | ^Vulnerable version of [\w\s]+: \d+\.\d+\.\d+$ |
| Action | — | Auto-delete |
As a result:
-
When AASM or TRT find something for
example.com/products/prod-01orexample.com/products/prod-02with a title starting with "Vulnerable version of…" (e.g. "Vulnerable version of WordPress: 4.6.26"), these findings will be auto-deleted and will not appear in the Security Issues section. -
If the same issues are found by passive detection, the rule will not apply and the issues will be created.
Security issue reports¶
You can get report on all or filtered security issues in CSV or JSON format using the Download report button.
Notifications¶
Email¶
You automatically receive notifications to your personal email (the one you use to log in) about discovered hosts and security issues, including:
-
Daily critical security issues (new only) - all critical security issues opened for the day, sent once a day with a detailed description of each issue and instructions on how to mitigate it.
-
Daily security issues (new only) - statistics for security issues opened for the day, sent once a day with information on how many issues of every risk level were found and general action items for mitigation.
Additionally, information about security issues found specifically by API Attack Surface Management (AASM) are sent within additional AASM-specific report:
- Weekly AASM statistics - information about hosts, APIs, and statistics for security issues discovered for your configured domains within last week.
The notifications are enabled by default. You can unsubscribe at any moment and configure any additional emails to get all or some of these notifications in Wallarm Console → Configuration → Integrations → Email and messengers → Personal email (you email) or Email report (extra emails) as described here.
Instant notification¶
You can configure instant notification for the new and re-opened security issues. Select all or only some risk levels that should trigger notification. Separate message will be sent for each security issue.
Example:
[Wallarm System] New security issue detected
Notification type: security_issue
New security issue was detected in your system.
ID: 106279
Title: Vulnerable version of Nginx: 1.14.2
Host: <HOST_WITH_ISSUE>
Path:
Port: 443
URL: <URL_WITH_ISSUE>
Method:
Discovered by: AASM
Parameter:
Type: Vulnerable component
Risk: Medium
More details:
Client: <YOUR_COMPANY_NAME>
Cloud: US
You can configure instant notification for the security issues in Wallarm Console → Configuration → Integrations → YOUR_INTEGRATION as described in your integration documentation.