Splunk¶
Splunk is a platform designed for searching, monitoring, and analyzing machine-generated data, including logs, events, and other forms of operational and business data. You can set up Wallarm to send alerts to Splunk.
Setting up integration¶
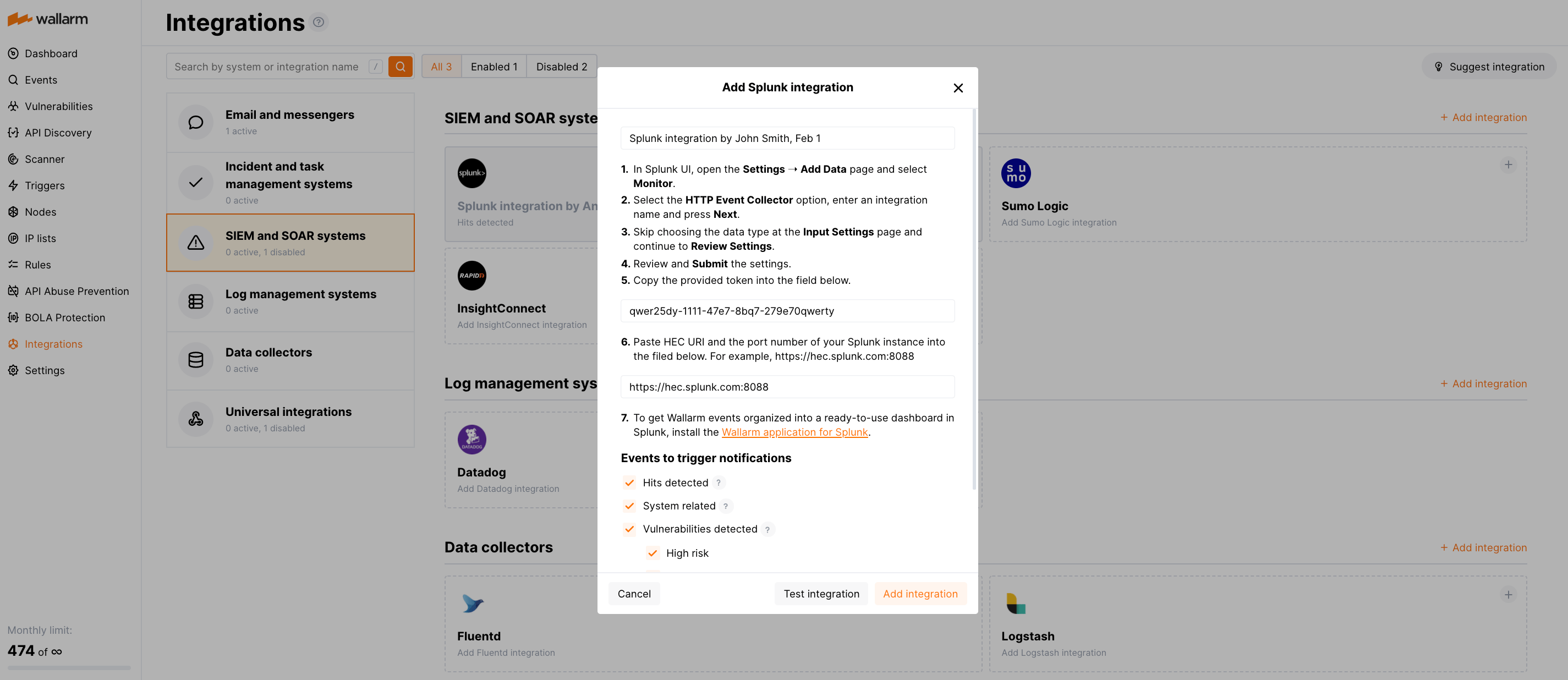
In Splunk UI:
-
Open Settings ➝ Add Data ➝ Monitor.
-
Select the HTTP Event Collector option, enter an integration name and click Next.
-
Skip choosing the data type at the Input Settings page and continue to Review Settings.
-
Review and Submit the settings.
-
Copy the provided token.
In Wallarm UI:
-
Open the Integrations section.
-
Click the Splunk block or click the Add integration button and choose Splunk.
-
Enter an integration name.
-
Paste the copied token into the HEC token field.
-
Paste HEC URI and the port number of your Splunk instance into the HEC URI:PORT field. For example:
https://hec.splunk.com:8088. -
Choose event types to trigger notifications.
Details on available events:
-
Hits detected except for:
- Experimental hits detected based on the custom regular expression. Non-experimental hits trigger notifications.
- Hits not saved in the sample.
-
System related:
- User changes (newly created, deleted, role change)
- Integration changes (disabled, deleted)
- Application changes (newly created, deleted, name change)
- Errors during regular update of specifications used for rogue API detection or API specification enforcement
- Vulnerabilities detected, all by default or only for the selected risk level(s) - high, medium or low.
- Rules and triggers changed (creating, updating, or deleting the rule or trigger)
- (Requires AASM Enterprise) Security issues detected, all or only for the selected risk level(s):
- Critical risk
- High risk
- Medium risk
- Low risk
- Info risk
- On an hourly basis, you can get a notification with the number of requests processed during the previous hour
-
-
Click Test integration to check configuration correctness, availability of the Wallarm Cloud, and the notification format.
Test Splunk notification in the JSON format:
{ summary:"[Test message] [Test partner(US)] New vulnerability detected", description:"Notification type: vuln New vulnerability was detected in your system. ID: Title: Test Domain: example.com Path: Method: Discovered by: Parameter: Type: Info Threat: Medium More details: https://us1.my.wallarm.com/object/555 Client: TestCompany Cloud: US ", details:{ client_name:"TestCompany", cloud:"US", notification_type:"vuln", vuln_link:"https://us1.my.wallarm.com/object/555", vuln:{ domain:"example.com", id:null, method:null, parameter:null, path:null, title:"Test", discovered_by:null, threat:"Medium", type:"Info" } } } -
Click Add integration.
Wallarm Cloud IP addresses
To provide Wallarm Cloud access to your system, you may need a list of its public IP addresses:
Setting up additional alerts¶
Besides the notifications you have already set up through the integration card, Wallarm triggers allow you to select additional events for notifications:
-
Number of attacks, hits or incidents per time interval (day, hour, etc.) exceeds the set number
What is not counted
- For attacks:
- The experimental attacks based on the custom regular expressions.
- For hits:
- The experimental hits based on the custom regular expressions.
- Hits not saved in the sample.
- For attacks:
-
Changes in API took place
-
IP address was denylisted
-
New rogue API (shadow, orphan, zombie) was detected
-
New user was added to the company account
For condition detailing, you can add one or more filters. As soon, as condition and filters are set, select the integration through which the selected alert should be sent. You can select several integrations simultaneously.
Getting events organized into a dashboard¶
To get Wallarm events organized into a ready-to-use dashboard in Splunk 9.0 or later, you can install the Wallarm application for Splunk.
This application provides you with a pre-configured dashboard that is automatically filled with the events received from Wallarm. In addition to that, the application enables you to proceed to detailed logs on each event and export the data from the dashboard.
To install the Wallarm application for Splunk:
-
In the Splunk UI ➝ Apps find the
Wallarm API Securityapplication. -
Click Install and input the Splunkbase credentials.
If some Wallarm events are already logged in Splunk, they will be displayed on the dashboard, as well as further events Wallarm will discover.
In addition, you can fully customize the ready-to-use dashboard, e.g. its view or search strings used to extract data from all Splunk records.
Disabling and deleting an integration¶
You can delete or temporarily disable the integration. While deleting stops sending notificatioins and completely deletes all configuration, disabling just stops sending notifications which you can at any moment re-enable with the same settings.
If for the integration the System related events are selected to trigger notifications, Wallarm will notify about both of these actions.
System unavailability and incorrect integration parameters¶
Notifications to the system are sent via requests. If the system is unavailable or integration parameters are configured incorrectly, the error code is returned in the response to the request.
If the system responds to Wallarm request with any code other than 2xx, Wallarm resends the request with the interval until the 2xx code is received:
-
The first cycle intervals: 1, 3, 5, 10, 10 seconds
-
The second cycle intervals: 0, 1, 3, 5, 30 seconds
-
The third cycle intervals: 1, 1, 3, 5, 10, 30 minutes
If the percentage of unsuccessful requests reaches 60% in 12 hours, the integration is automatically disabled. If you receive system notifications, you will get a message about automatically disabled integration.