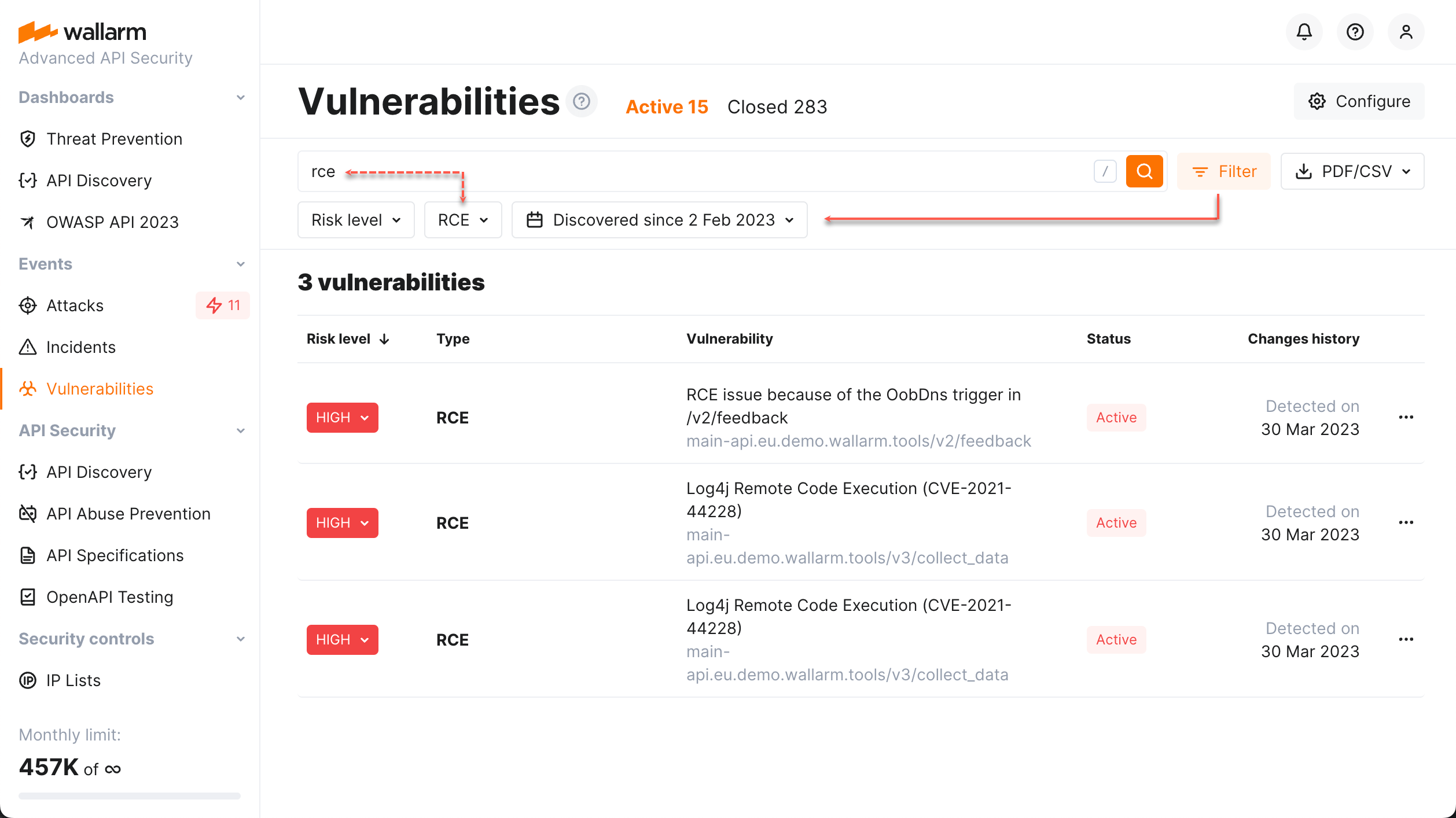
Vulnerability Search and Filters¶
In the Vulnerabilities section, Wallarm provides convenient methods for searching among detected vulnerabilities.
You can use:
-
Filters to select filtering criteria
-
Search field to input search queries with attributes and modifiers similar to human language
The values set in the filters are automatically duplicated in the search field, and vice versa.
Filters¶
Available filters are presented in Wallarm Console on the filters panel that is expanded and collapsed using the Filter button.
When values of different filters are selected, the results will meet all those conditions. When different values for the same filter are specified, the results will meet any of those conditions.
Search field¶
The search field accepts queries with attributes and modifiers similar to human language which makes submitting queries intuitive. For example:
-
rce high: to search for all RCE vulnerabilities with high risk level -
ptrav medium: to search for all path traversal vulnerabilities with high risk level
When values of different parameters are specified, the results will meet all those conditions. When different values for the same parameter are specified, the results will meet any of those conditions.
Setting the attribute value to NOT
To negate the attribute value, please use ! before the attribute or modifier name. For example: rce !low to show all RCE vulnerabilities except the ones with the low risk level.
Below you will find the list of attributes and modifiers available for use in search queries.
Search by vulnerability type¶
Specify in the search string:
-
sqli: to search for SQL injection vulnerabilities. -
xss: to search for cross site scripting vulnerabilities. -
rce: to search for OS commanding vulnerabilities. -
ptrav: to search for path traversal vulnerabilities. -
crlf: to search for CRLF injection vulnerabilities. -
nosqli: to search for NoSQL injection vulnerabilities. -
xxe: to search for XML external entity vulnerabilities. -
ldapi: to search for LDAP injection vulnerabilities. -
ssti: to search for server‑side template injections. -
infoleak: to search for vulnerabilities of information disclosure type. -
vuln_component: to search for vulnerabilities related to the components of your applications that are outdated or contain security affecting errors. -
redir: to search for open redirect vulnerabilities. -
idor: to search for broken object level authorization (BOLA) vulnerabilities. -
ssrf: to search for server‑side request forgery (SSRF) vulnerabilities. -
csrf: to search for cross-site request forgery (CSRF) vulnerabilities. -
weak_auth: to search for weak JWT vulnerabilities.
A vulnerability name can be specified in both uppercase and lowercase letters: SQLI, sqli, and SQLi are equally correct.
Search by risk level¶
Specify the risk level in the search string:
-
low: low risk level. -
medium: medium risk level. -
high: high risk level.