Virtual Patching¶
In cases when it is impossible to fix a critical vulnerability in the code of your application or install the necessary updates quickly, you can create a virtual patch to block all or specific requests to the endpoints that may allow exploiting these vulnerabilities. Virtual patch will block requests even in the monitoring and safe blocking modes, except the ones originating from the allowlisted IPs.
Wallarm provides the following rules to create virtual patch:
-
Create a virtual patch rule - allows creating virtual patch that blocks requests containing in its selected part one of the known attack signs, such as SQLi, SSTi, RCE etc. Also, you can select Any request to block specific requests without any attack signs.
-
Create regexp-based attack indicator rule with Virtual patch option selected - allows creating virtual patch that blocks requests containing your own attack signs or your own reason for blocking (see example) that are described with the regular expressions. Details on working with rule based on regular expression are described here.
Creating and applying the rule¶
-
Proceed to Wallarm Console:
- Rules → Add rule or your branch → Add rule.
- Attacks / Incidents → attack/incident → hit → Rule.
- API Discovery (if enabled) → your endpoint → Create rule.
-
Choose Mitigation controls →
- Virtual patch or
- Custom attack detector (with Virtual patch option - see details)
-
In If request is, describe the scope to apply the rule to.
-
For the common Create a virtual patch rule, set whether to block any request or only the ones containing specific attack signs (Any request vs. Selected).
-
In In this part of request, specify request points for which you wish to set the rule. Wallarm will restrict requests that have the same values for the selected request parameters.
All available points are described here, you can choose those matching your particular use case.
-
Wait for the rule compilation and uploading to the filtering node to complete.
Rule examples¶
Blocking specific requests for selected endpoint¶
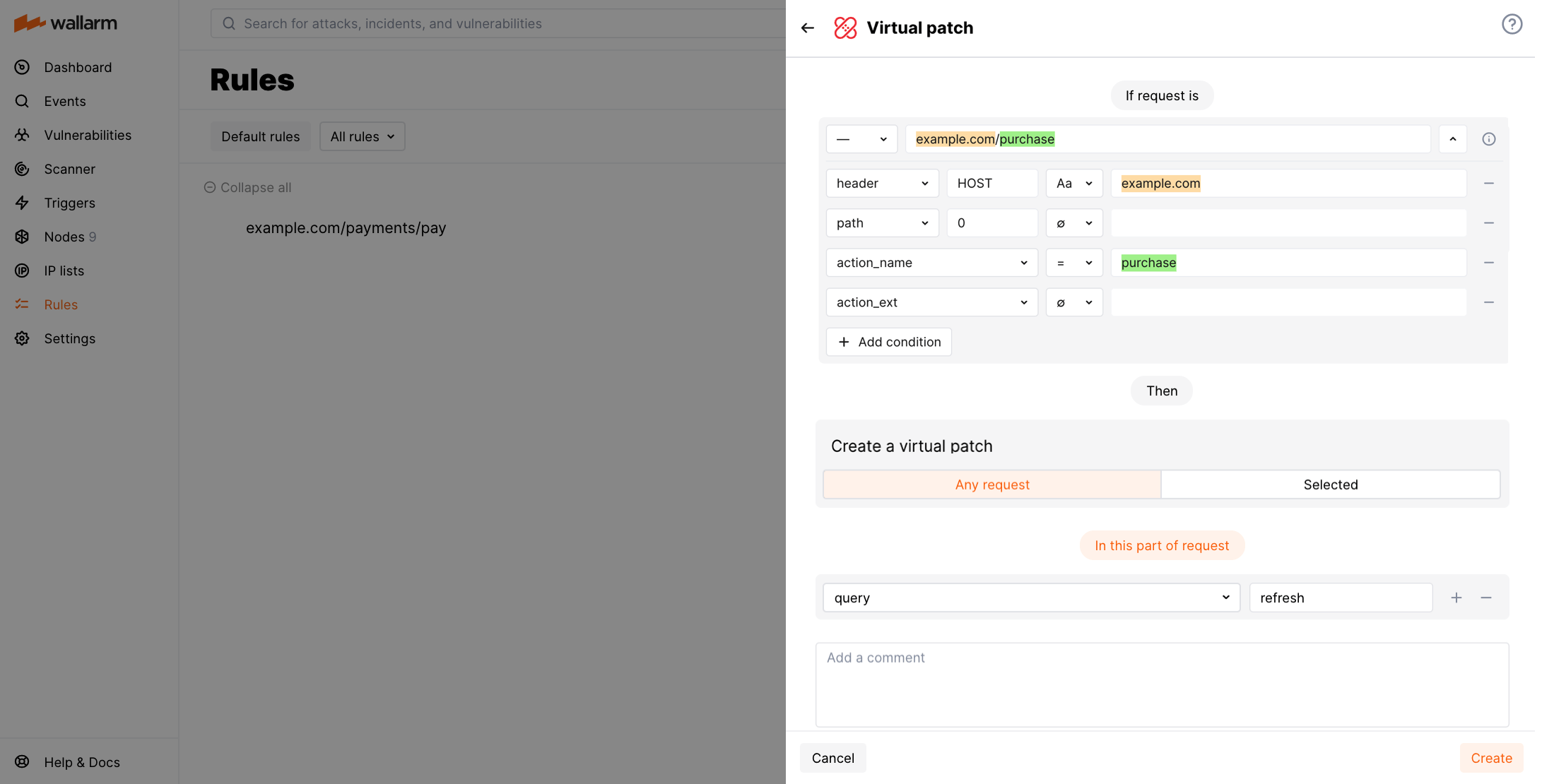
Let us say your application online purchase section accessible at the example.com/purchase endpoint crashes upon processing the refresh query string parameter. Before the bug is fixed, you need to block requests leading to the crash.
To do so, set the Create a virtual patch rule as displayed on the screenshot:
Blocking exploitation attempts for discovered but not yet fixed vulnerability¶
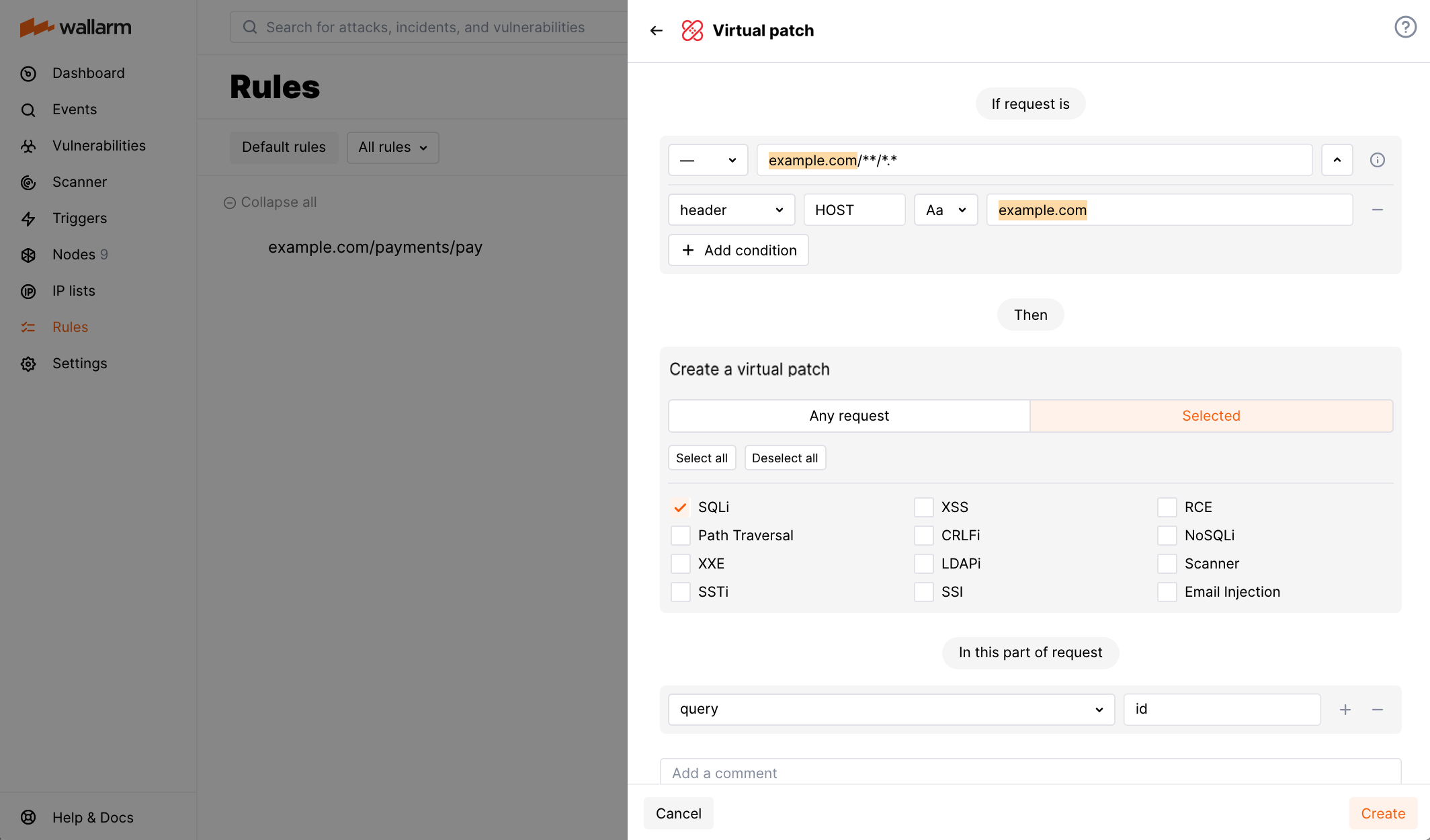
Let us say your application accessible at the example.com domain has discovered but not yet fixed vulnerability: the application's id parameter is vulnerable to SQL injection attacks. Meanwhile, Wallarm filtering node is set to monitoring mode and yet you need to immediately block the vulnerability exploitation attempts.
To do so, set the Create a virtual patch rule as displayed on the screenshot:
Blocking all requests with incorrect X-AUTHENTICATION header¶
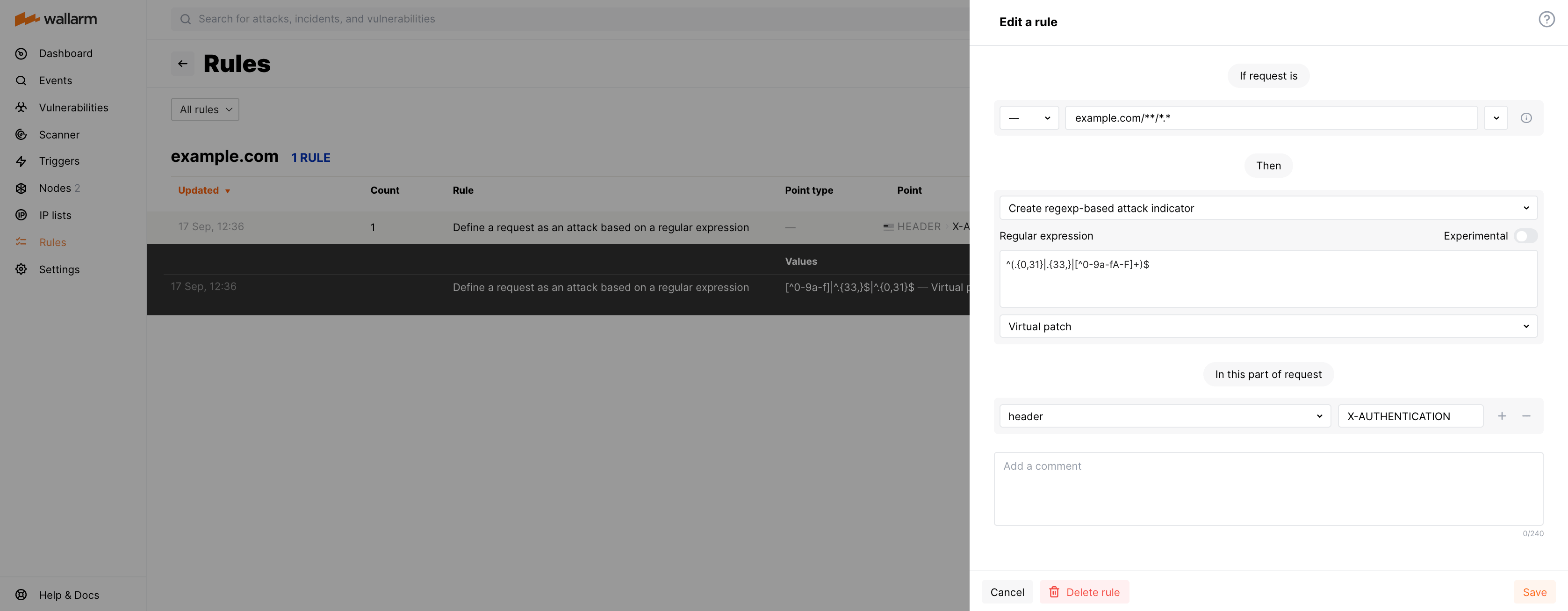
Let us say your application accessible at the example.com domain uses the X-AUTHENTICATION header in 32 hex symbols format for user authentication and you want to reject incorrect format tokens.
To do so, set the Create regexp-based attack indicator rule and set it to Virtual patch as displayed on the screenshot, including:
-
Regular expression:
^(.{0,31}|.{33,}|[^0-9a-fA-F]+)$ -
Request part:
header-X-AUTHENTICATION
API calls for virtual patches¶
To create virtual patches, you can call the Wallarm API directly. Consider the examples: