Masking Sensitive Data¶
In the hybrid Wallarm installations, when you manage the Wallarm filtering nodes in your infrastructure, and Wallarm manages the Wallarm Cloud component, it is crucial that sensitive data in your requests remains secure within your infrastructure and is not transmitted to any third-party service including Wallarm Cloud. This goal is achieved using the shared responsibility model: from its side, Wallarm transmits no data except the one about malicious requests, which makes exposure of sensitive data highly unlikely - from your side, masking of sensitive data is expected which additionally guarantees that protected information fields will never leave your security perimeter.
Other deployment forms
While in on-premise installations data never leaves your security perimeter, and in security edge all data is outside this security perimeter, you can still use masking rules to restrict access to the sensitive data by the users of Wallarm Console.
Wallarm provides the Mask sensitive data rule to configure data masking. The Wallarm node sends the following data to the Wallarm Cloud:
-
Serialized requests with attacks
-
Wallarm system counters
-
System statistics: CPU load, RAM usage, etc.
-
Wallarm system statistics: number of processed NGINX requests, wstore statistics, etc.
-
Information on the nature of the traffic that Wallarm needs to correctly detect application structure
The Mask sensitive data rule cuts the original value of the specified request point before sending the request to the postanalytics module and Wallarm Cloud. This method ensures that sensitive data cannot leak outside the trusted environment.
It can affect the display of attacks and the detection of brute force attacks.
Creating and applying rule¶
To set and apply data mask:
-
Proceed to Wallarm Console:
- Rules → Add rule or your branch → Add rule.
- Attacks / Incidents → attack/incident → hit → Rule.
- API Discovery (if enabled) → your endpoint → Create rule.
-
Choose Change requests/responses → Mask sensitive data.
-
In If request is, describe the scope to apply the rule to.
-
In In this part of request, specify request points for which its original value should be cut.
-
Wait for the rule compilation and uploading to the filtering node to complete.
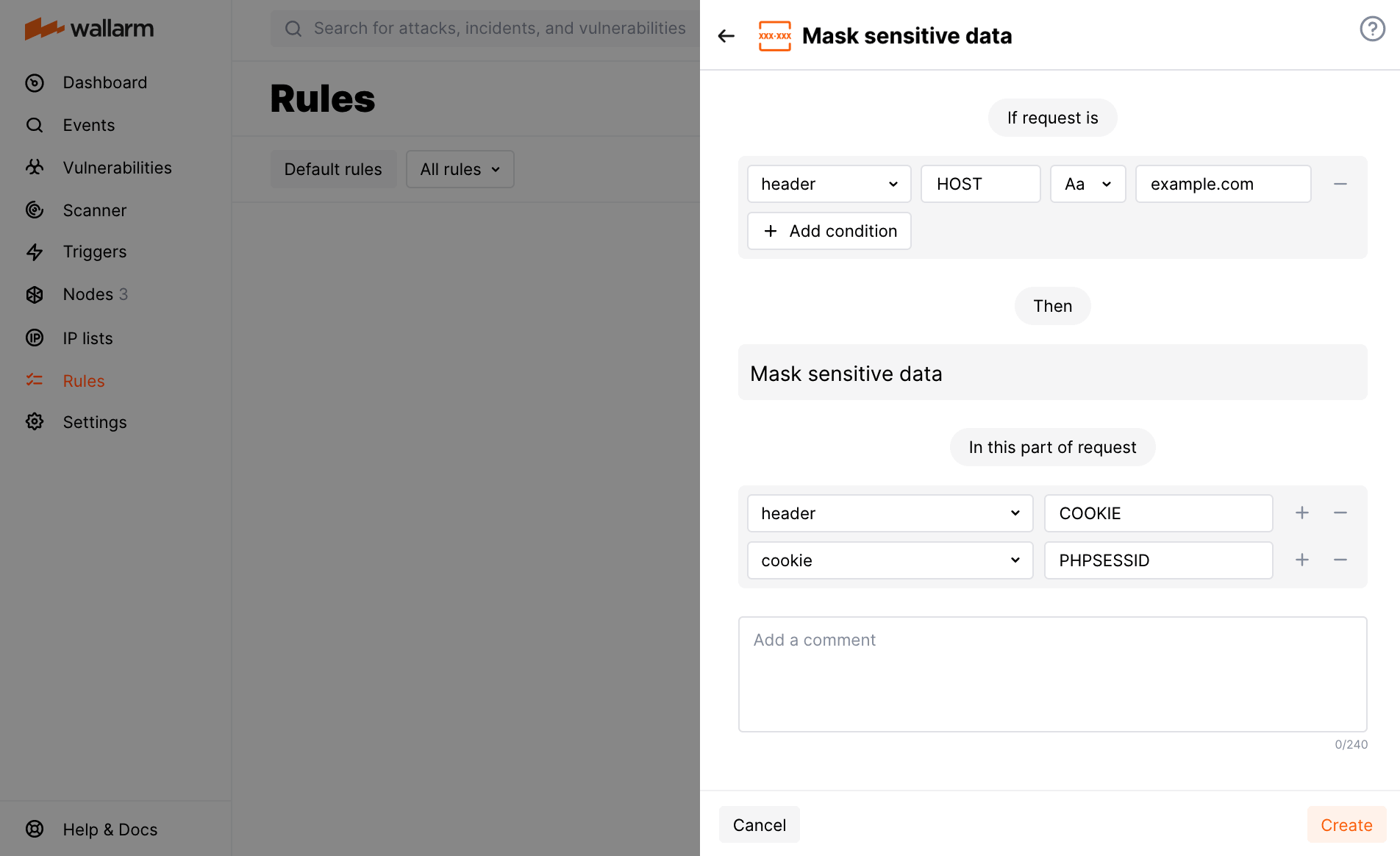
Example: masking of a cookie value¶
Let us say your application accessible at the example.com domain uses the PHPSESSID cookie for user authentication and you want to deny access to this information for employees using Wallarm.
To do so, set the Mask sensitive data rule as displayed on the screenshot.
Note that options you add to In this part of request should go in a particular order to reflect in which order Wallarm will apply parsers to read the required request element.