Changing Server Response Headers¶
The Change server response headers rule allows adding, deleting server response headers and changing its values.
This rule type is most often used to configure the additional layer of the application security, for example:
-
To add the response header
Content-Security-Policycontrolling the resources the client is allowed to load for a given page. This helps guard against the XSS attacks.If your server does not return this header by default, it is recommended to add it by using the rule Change server response headers. In the MDN Web Docs, you can find descriptions of possible header values and header usage examples.
Similarly, this rule can be used to add the response headers
X-XSS-Protection,X-Frame-Options,X-Content-Type-Options. -
To change the NGINX header
Serveror any other header containing the data on installed module versions. This data can be potentially used by the attacker to discover vulnerabilities of installed module versions and as a result, to exploit discovered vulnerabilities.The NGINX header
Servercan be changed starting with Wallarm node 2.16.
The rule Change server response headers can also be used to address any of your business and technical issues.
Creating and applying the rule¶
To create and apply the rule:
-
Proceed to Wallarm Console:
- Rules → Add rule or your branch → Add rule.
- Attacks / Incidents → attack/incident → hit → Rule.
- API Discovery (if enabled) → your endpoint → Create rule.
-
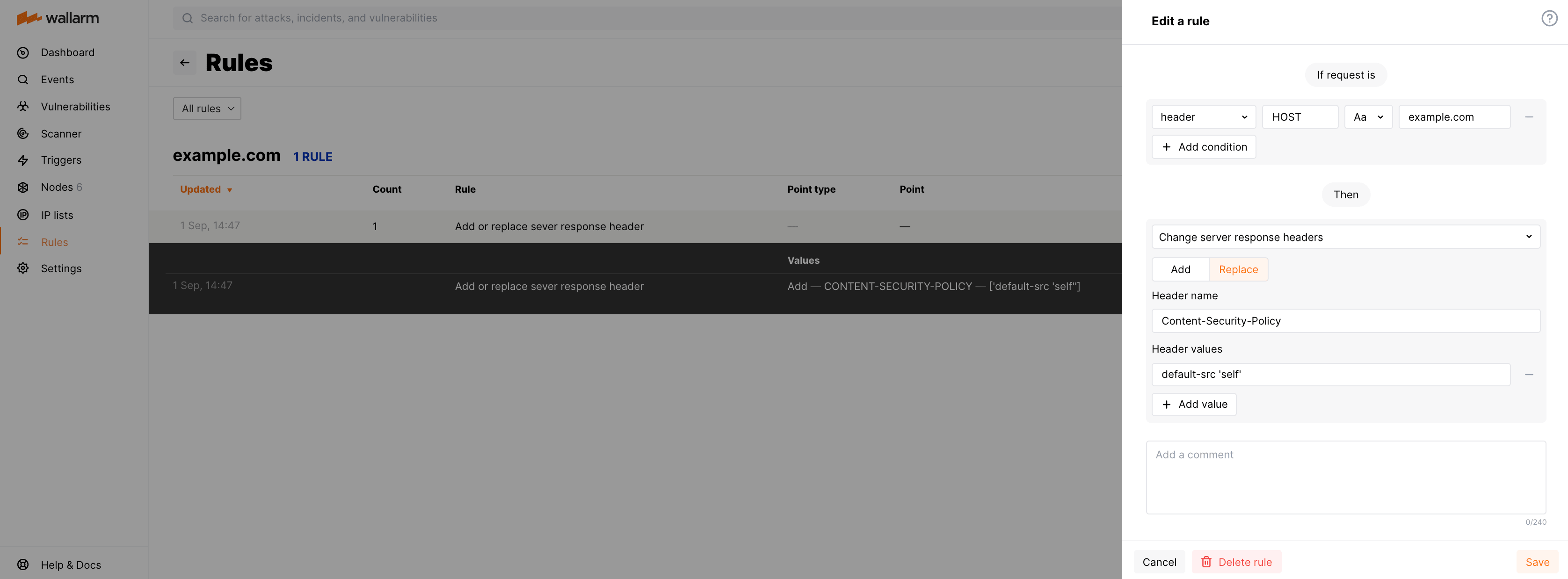
In If request is, describe the scope to apply the rule to.
-
In Then, choose Change server response headers and set:
- Name of the header to be added or to replace its value.
- New value(s) of the specified header.
- To delete an existing response header, leave its value on the Replace tab empty.
-
Wait for the rule compilation to complete.
Example: adding security policy header and its value¶
To allow all content of https://example.com/* to come only from the site's origin, you can add the response header Content-Security-Policy: default-src 'self' by using the rule Change server response headers as follows: