Incident Analysis¶
In Wallarm Console, you can analyze detected incidents in the Incidents section. To find required data, please use the search field as described here or manually set required search filters.
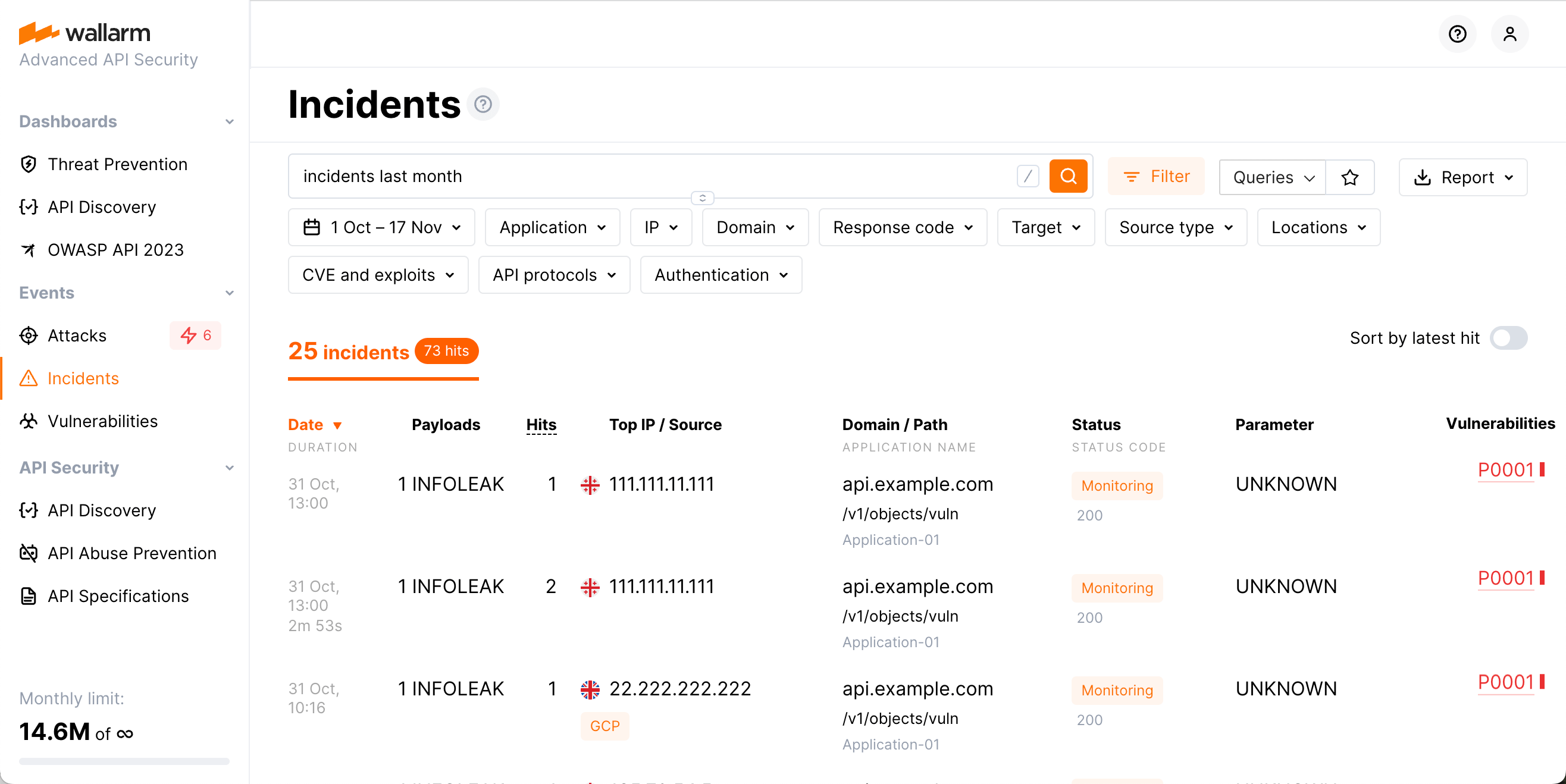
Checking incidents¶
-
Date: The date and time of the malicious request.
- If several requests of the same type were detected at short intervals, the attack duration appears under the date. Duration is the time period between the first request of a certain type and the last request of the same type in the specified timeframe.
- If the attack is happening at the current moment, an appropriate label is displayed.
-
Payloads: Attack type and the number of unique malicious payload.
-
Hits: The number of hits (requests) in the attack in the specified time frame.
-
Top IP / Source: The IP address from which the malicious requests originated. When the malicious requests originate from several IP addresses, the interface shows the IP address responsible for the most requests. There is also the following data displayed for the IP address:
- The total number of IP addresses from which the requests in the same attack originated during the specified timeframe.
- The country/region in which the IP address is registered (if it was found in the databases like IP2Location or others)
- The source type, like Public proxy, Web proxy, Tor or the cloud platform the IP registered in, etc (if it was found in the databases like IP2Location or others)
- The Malicious IPs label will appear if the IP address is known for malicious activities. This is based on public records and expert validations
-
Domain / Path: The domain, path and the application ID that the request targeted.
-
Status: The attack blocking status (depends on the traffic filtration mode):
- Blocked: all hits of the attack were blocked by the filtering node.
- Partially blocked: some hits of the attack were blocked and others were only registered.
- Monitoring: all hits of the attack were registered but not blocked.
-
Parameter: The malicious request's parameters and tags of parsers applied to the request
-
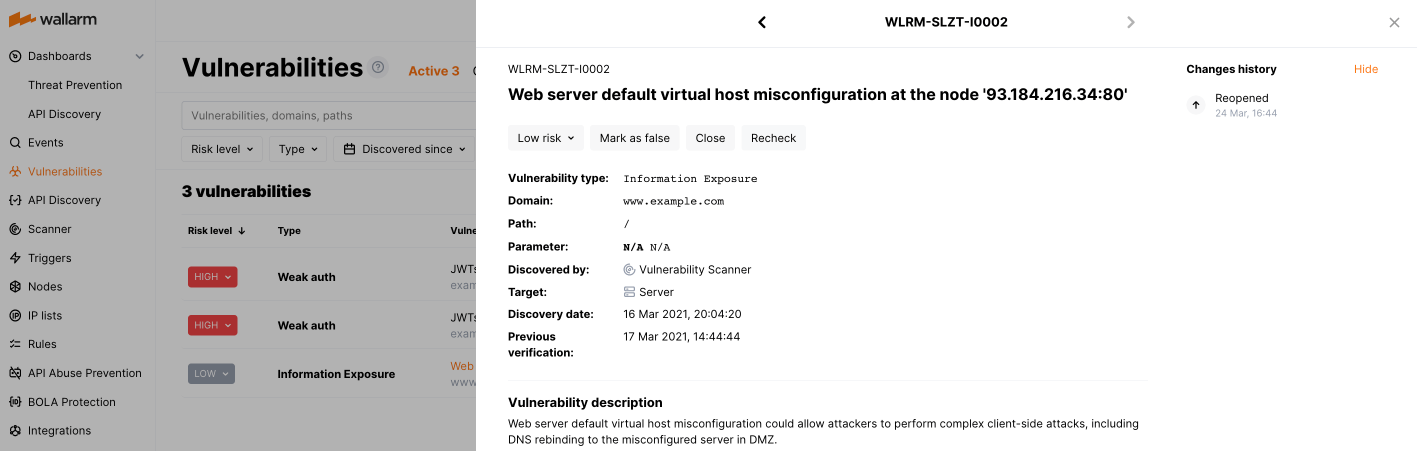
Vulnerabilities: The vulnerability, that the incident exploits. Clicking the vulnerability brings you to its detailed description and instructions on how to fix it.
To sort incidents by the time of the last request, you can use the Sort by latest hit switch.
Full context of threat actor activities¶
Once the malicious request is detected by Wallarm and displayed in the Attacks or Incidents section as the part of some attack, you have an ability to know the full context of this request: to which user session it belongs and what the full sequence of requests in this session is. This allows investigating all activity of the threat actor to understand attack vectors and what resources can be compromised.
To perform this analysis, in Wallarm Console → Attacks or Incidents, access the attack, and then specific request details. In request details, click Explore in API Sessions. Wallarm will open the API Session section filtered: the session, the initial request belongs to is displayed, only the initial request is displayed within this session.
Remove the filter by request ID to see all other requests in the session: now you have the full picture of what was going on within the session the malicious request belongs to.
Responding to incidents¶
The incidents are the attacks targeted at a confirmed vulnerability.
Once incident appeared in the Incidents section:
-
Optionally (recommended), investigate the full context of the incident's malicious requests: to which user session they belong and what the full sequence of requests in this session is.
This allows seeing all activity and logic of the threat actor and understanding attack vectors and what resources can be compromised.
-
Follow the link in the Vulnerabilities column to get detailed vulnerability information including instructions on how to fix this vulnerability and the list of related incidents.
Fix the vulnerability and then mark it closed in Wallarm. For detailed information, refer to Managing Vulnerabilities article.
-
Go back to the incident in the list, investigate what mechanism caused the system reaction (note the
Blocked,Partially blockedandMonitoringstatuses of the attacks), how the system will behave in future to alike requests and how to adjust (if necessary) this future behavior.For incidents, this investigation and adjusting is performed in the same way as for all other attacks.
API calls to get incidents¶
To get the incident details, you can call the Wallarm API directly besides using the Wallarm Console UI. Below is the example of the API call for getting the first 50 incidents detected in the last 24 hours.
The request is similar to the one used for a list of attacks; the "!vulnid": null term is added to request for incidents. This term instructs the API to ignore all attacks without specified vulnerability ID, and this is how the system distinguishes between attacks and incidents.
Please replace TIMESTAMP with the date 24 hours ago converted to the Unix Timestamp format.
curl -v -X POST "https://us1.api.wallarm.com/v1/objects/attack" -H "X-WallarmApi-Token: <YOUR_TOKEN>" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"filter\": { \"clientid\": [YOUR_CLIENT_ID], \"\!vulnid\": null, \"time\": [[TIMESTAMP, null]] }, \"offset\": 0, \"limit\": 50, \"order_by\": \"last_time\", \"order_desc\": true}"
curl -v -X POST "https://api.wallarm.com/v1/objects/attack" -H "X-WallarmApi-Token: <YOUR_TOKEN>" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"filter\": { \"clientid\": [YOUR_CLIENT_ID], \"\!vulnid\": null, \"time\": [[TIMESTAMP, null]] }, \"offset\": 0, \"limit\": 50, \"order_by\": \"last_time\", \"order_desc\": true}"