Automatic BOLA Protection for Endpoints Found by API Discovery  ¶
¶
This article describes automatic BOLA protection for endpoints discovered by API Discovery (APID).
Other BOLA protection measures
Alternatively or additionally, you can configure BOLA protection with triggers.
Overview¶
Behavioral attacks such as Broken Object Level Authorization (BOLA) exploit the vulnerability of the same name. This vulnerability allows an attacker to access an object by its identifier via an API request and either read or modify its data bypassing an authorization mechanism. This article instructs you on protecting your applications against BOLA attacks.
By default, Wallarm automatically discovers only vulnerabilities of the BOLA type (also known as IDOR) but does not detect its exploitation attempts.
BOLA protection restrictions
Only Wallarm node 4.2 and above supports BOLA attack detection.
Wallarm node 4.2 and above analyzes only the following requests for BOLA attack signs:
- Requests sent via the HTTP protocol.
-
Requests that do not contain signs of other attack types, e.g. requests are not considered to be a BOLA attack if:
- These requests contain signs of input validation attacks.
- These requests match the regular expression specified in the rule Create regexp-based attack indicator.
Requirements¶
To protect resources from BOLA attacks, make sure your environment meets the following requirements:
- If the filtering node is deployed behind a proxy server or load balancer, configure displaying real clients' IP addresses.
Protection logic¶
Once BOLA protection is enabled, Wallarm:
-
Identifies API endpoints that are most likely to be the target of BOLA attacks, e.g. those with variability in path parameters:
domain.com/path1/path2/path3/{variative_path4}.This stage takes a period of time
Identification of vulnerable API endpoints takes a period of time required for deep observation of discovered API inventory and incoming traffic trends.
Only API endpoints explored by the API Discovery module are protected against BOLA attacks in the automated way. Protected endpoints are highlighted with the corresponding icon.
-
Protects vulnerable API endpoints against BOLA attacks. The default protection logic is the following:
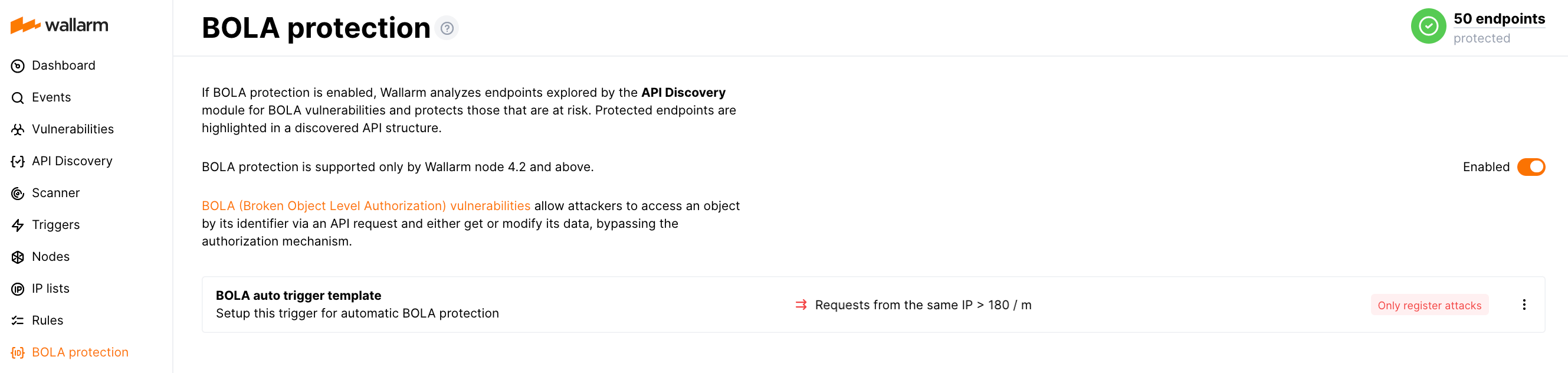
- Requests to a vulnerable endpoint exceeding the 180 requests threshold from the same IP per minute are considered BOLA attacks.
-
Only register BOLA attacks in the event list when the threshold of requests from the same IP is reached. Wallarm does not block BOLA attacks. Requests will keep going to your applications.
The corresponding reaction in the autoprotection template is Only register attacks.
-
Reacts to changes in API by protecting new vulnerable endpoints and disabling protection for removed endpoints.
Configuring¶
API Discovery required
Automatic BOLA protection is available if you use the API Discovery module.
To enable auto protection, proceed to Wallarm Console → BOLA protection and turn the switch to the enabled state:
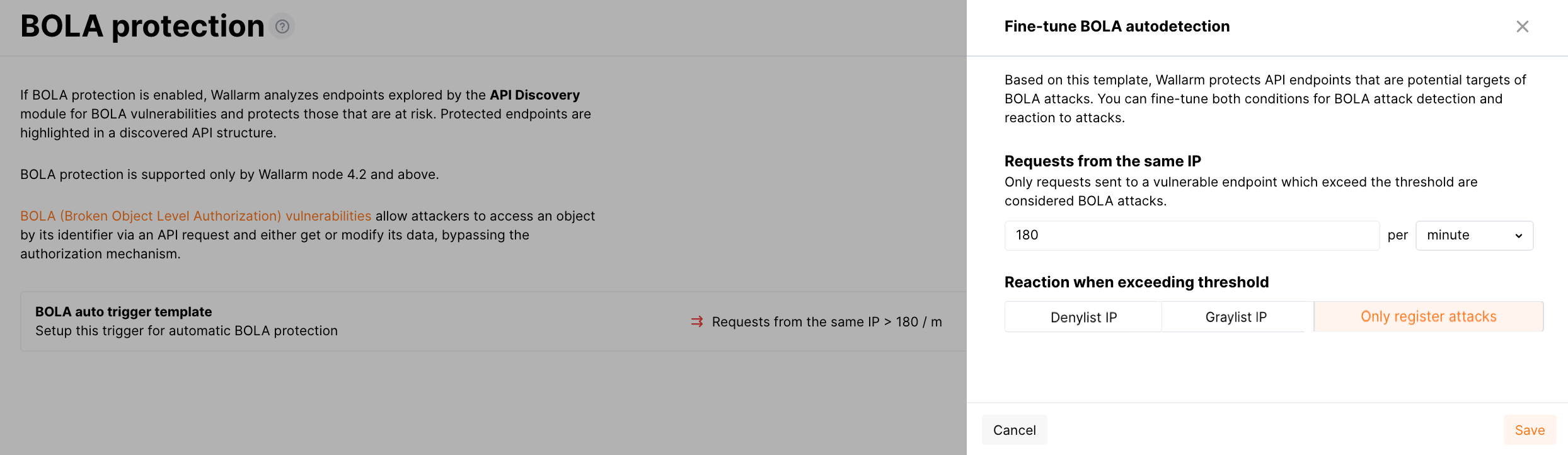
Then you can fine-tune the default Wallarm behavior by editing the BOLA autodetection template as follows:
-
Change the threshold for requests from the same IP to be marked as the BOLA attacks.
-
Change the reaction when exceeding threshold:
- Denylist IP - Wallarm will denylist the IPs of the BOLA attack source and thus block all traffic these IPs produce.
- Graylist IP - Wallarm will graylist the IPs of the BOLA attack source and thus block only malicious requests from these IPs and only if the filtering node is in the safe blocking mode.
Disabling¶
To disable automated BOLA protection, turn the switch to the disabled state in the BOLA protection section.
Once your API Discovery subscription is expired, automated BOLA protection is disabled automatically.