File Upload Restriction Policy¶
Unrestricted resource consumption, en ciddi API güvenlik risklerinin yer aldığı OWASP API Top 10 2023 listesine dahildir. Kendi başına bir tehdit olmakla birlikte (hizmetin yavaşlaması veya aşırı yüklenme nedeniyle tamamen çökmesi), farklı saldırı türlerine de zemin hazırlar; örneğin, enumeration saldırıları. Çok büyük dosya yüklemeye izin verilmesi bu risklerin nedenlerinden biridir. Bu makale, Wallarm’da dosya yükleme kısıtlamalarının nasıl yapılandırılacağını açıklar.
Dosya yükleme kısıtlamasını kullanarak mitigation controls ile yapılandırırsanız, kontrolün doğrudan amacına (yüklenen dosyaların azami boyutunu sınırlama) ek olarak, belirli istek parametrelerinin boyutunu sınırlayarak saldırı yüzeyini de azaltabilirsiniz. Örneğin, rastgele bir header’ın azami boyutunu sınırlayan kurallar ayarlayabilirsiniz. Bu durumda saldırganın payload’ını içeri itme veya BufferOverflow’dan yararlanma imkanları azalır.
Wallarm’ın, sınırsız kaynak tüketimini engellemek için sağladığı tek önlem dosya boyutu yükleme kısıtlamaları değildir.
Configuration method¶
Abonelik planınıza bağlı olarak, dosya yükleme kısıtlaması için aşağıdaki yapılandırma yöntemlerinden biri kullanılabilir:
-
Mitigation controls (Advanced API Security aboneliği) - bir mitigation control kullanarak yalnızca isteğin toplam boyutuna değil, belirli bir parametreye de limit koyabilirsiniz (kurala göre daha hassas ayarlar).
-
Rules (Cloud Native WAAP aboneliği)
Mitigation control-based protection  ¶
¶
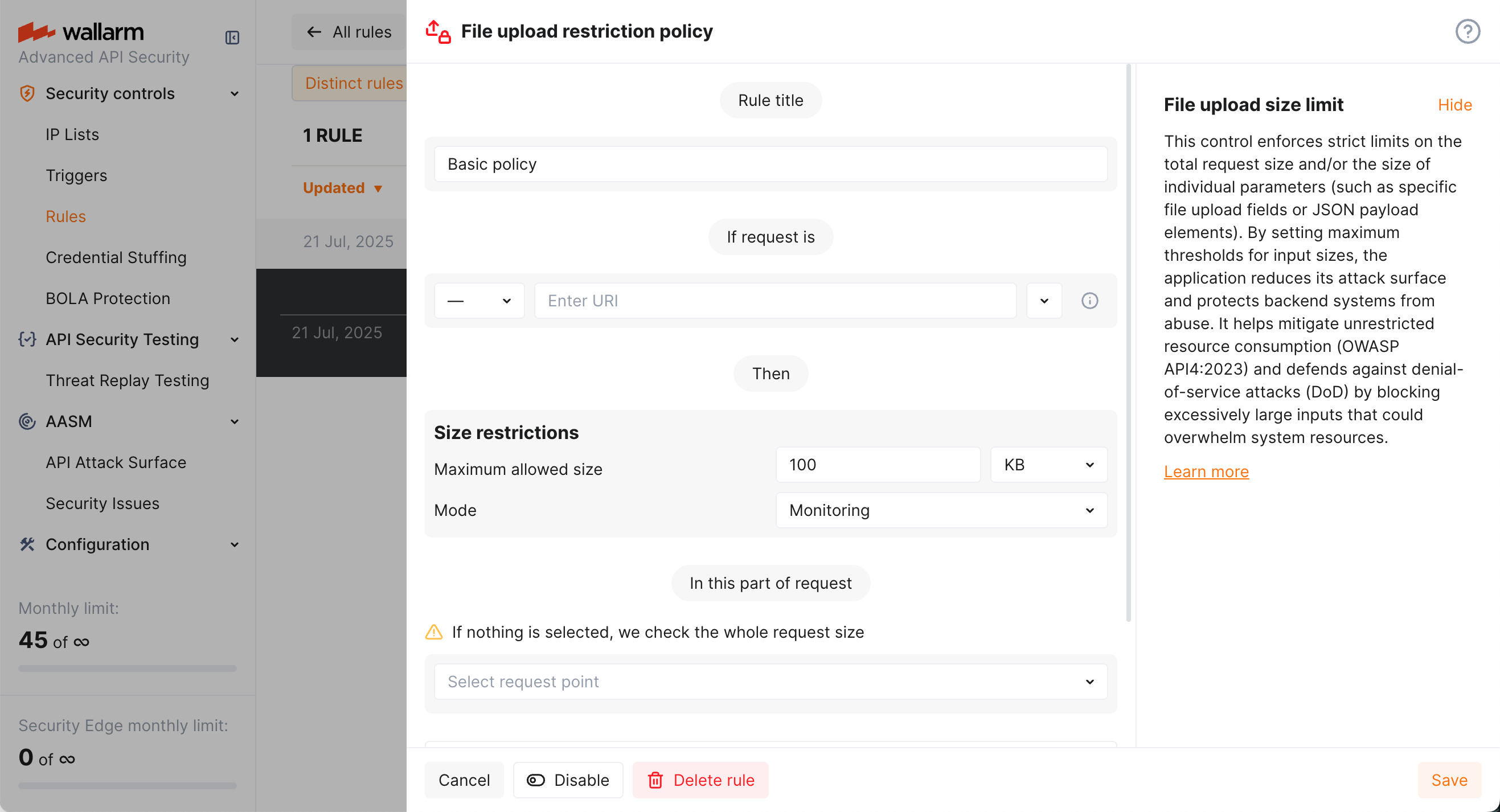
Advanced API Security aboneliğinin bir parçası olarak Wallarm, File upload restriction policy mitigation control sağlar.
NGINX Node 6.3.0 veya üzeri gerektirir ve şu an için Native Node tarafından desteklenmemektedir.
Bu mitigation control ile belirli bir parametrenin boyutuna limit koyabilir (daha hassas ayarlar), ya da basitlik için limiti tüm istek üzerinde tanımlayabilirsiniz.
Belirli istek parametrelerinin boyutunu sınırlamak, kontrolün doğrudan amacına (yüklenen dosyaların azami boyutunu sınırlama) ek olarak saldırı yüzeyini azaltmaya da olanak tanır. Örneğin, rastgele bir header’ın azami boyutunu sınırlayan kurallar ayarlayabilirsiniz. Bu durumda saldırganın payload’ını içeri itme veya BufferOverflow’dan yararlanma imkanları azalır.
Mitigation control oluşturma ve uygulama¶
Azaltma kontrollerine ilişkin genel bilgiler
Devam etmeden önce: Herhangi bir mitigation control için Scope ve Mitigation mode ayarlarının nasıl yapıldığını öğrenmek üzere Mitigation Controls makalesini kullanın.
Dosya yükleme kısıtlama politikasını yapılandırmak için:
-
Wallarm Console → Mitigation Controls bölümüne gidin.
-
Add control → File upload restriction policy seçin.
-
Mitigation control’ün uygulanacağı Scope’u tanımlayın.
-
Tüm istek için veya seçili nokta için Size restrictions ayarlayın.
-
Mitigation mode bölümünde gerçekleştirilecek eylemi ayarlayın.
-
Add’a tıklayın.
Mitigation control örnekleri¶
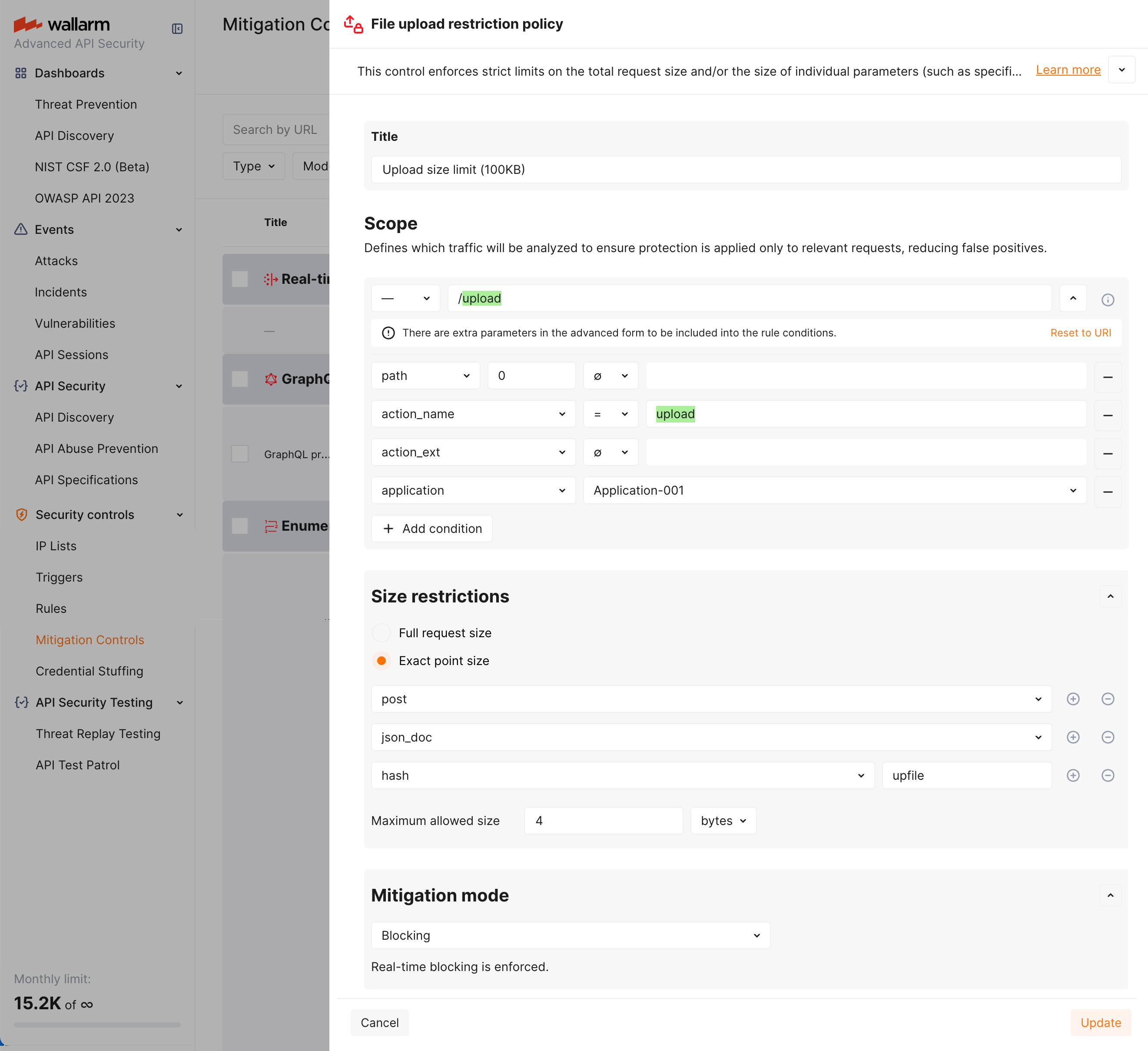
Belirli bir istek alanı üzerinden yüklenen dosyanın boyutunu sınırlama¶
Diyelim ki application-001 uygulamanızın /upload adresine, upfile POST istek parametresi üzerinden yüklenen dosyaların boyutunu sınırlamak istiyorsunuz. Limit 100KB olmalı. Limiti aşan her şey engellenmelidir.
Bunu yapmak için, File upload restriction policy mitigation control’ü ekran görüntüsünde gösterildiği gibi ayarlayın:
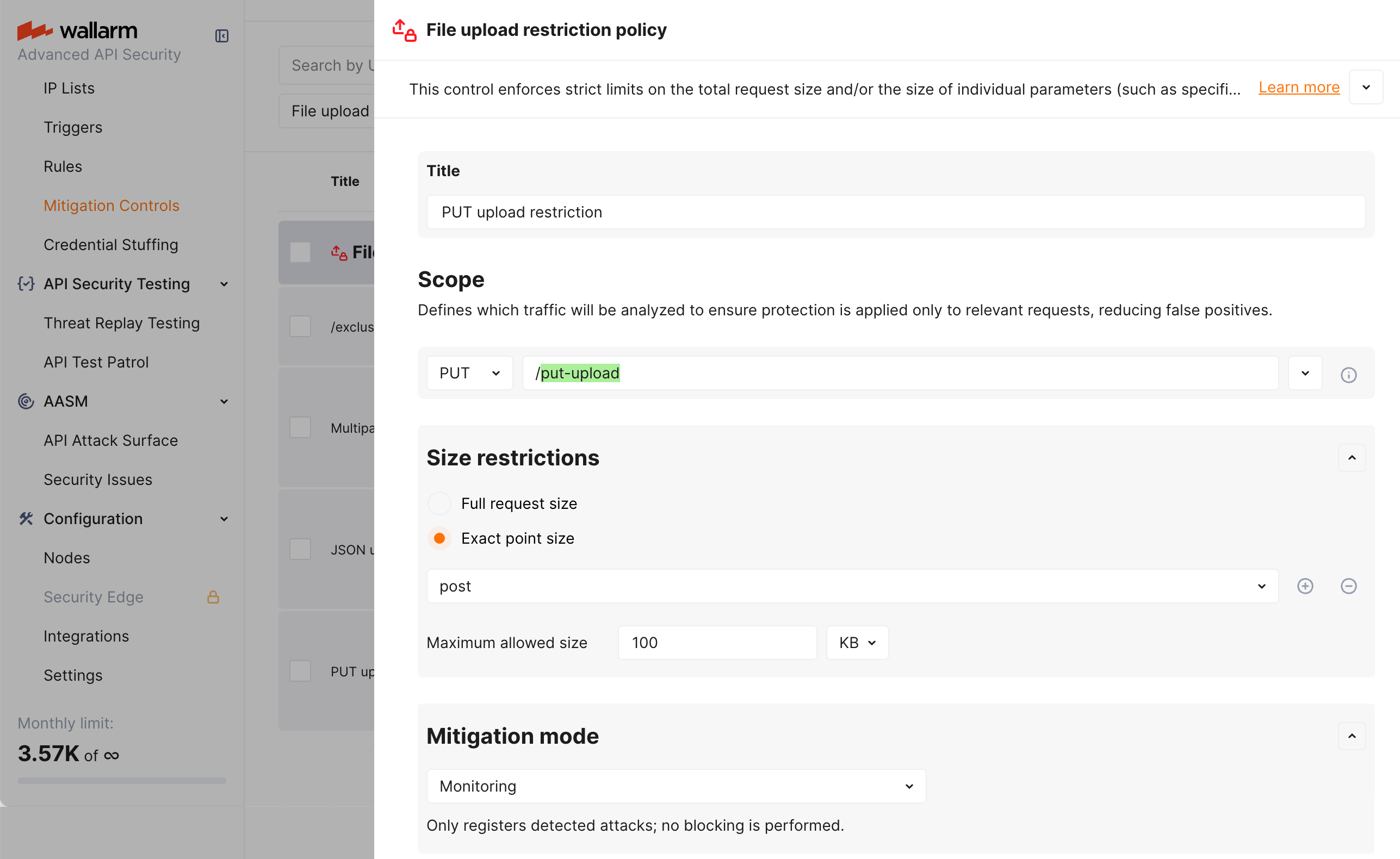
Exact point size ile PUT yüklemesini kısıtlama¶
Diyelim ki uygulamanızın /put-upload adresine, PUT yöntemiyle istek gövdesinde 100KB’den büyük dosya yükleme girişimlerini (engellemeden) saldırı olarak kaydetmek istiyorsunuz.
Bunu yapmak için, File upload restriction policy mitigation control’ü ekran görüntüsünde gösterildiği gibi ayarlayın:
Yukarıdaki örnekte, istek noktası tanımında post, Wallarm’ın etiketi olup “istek gövdesinde” anlamına gelir.
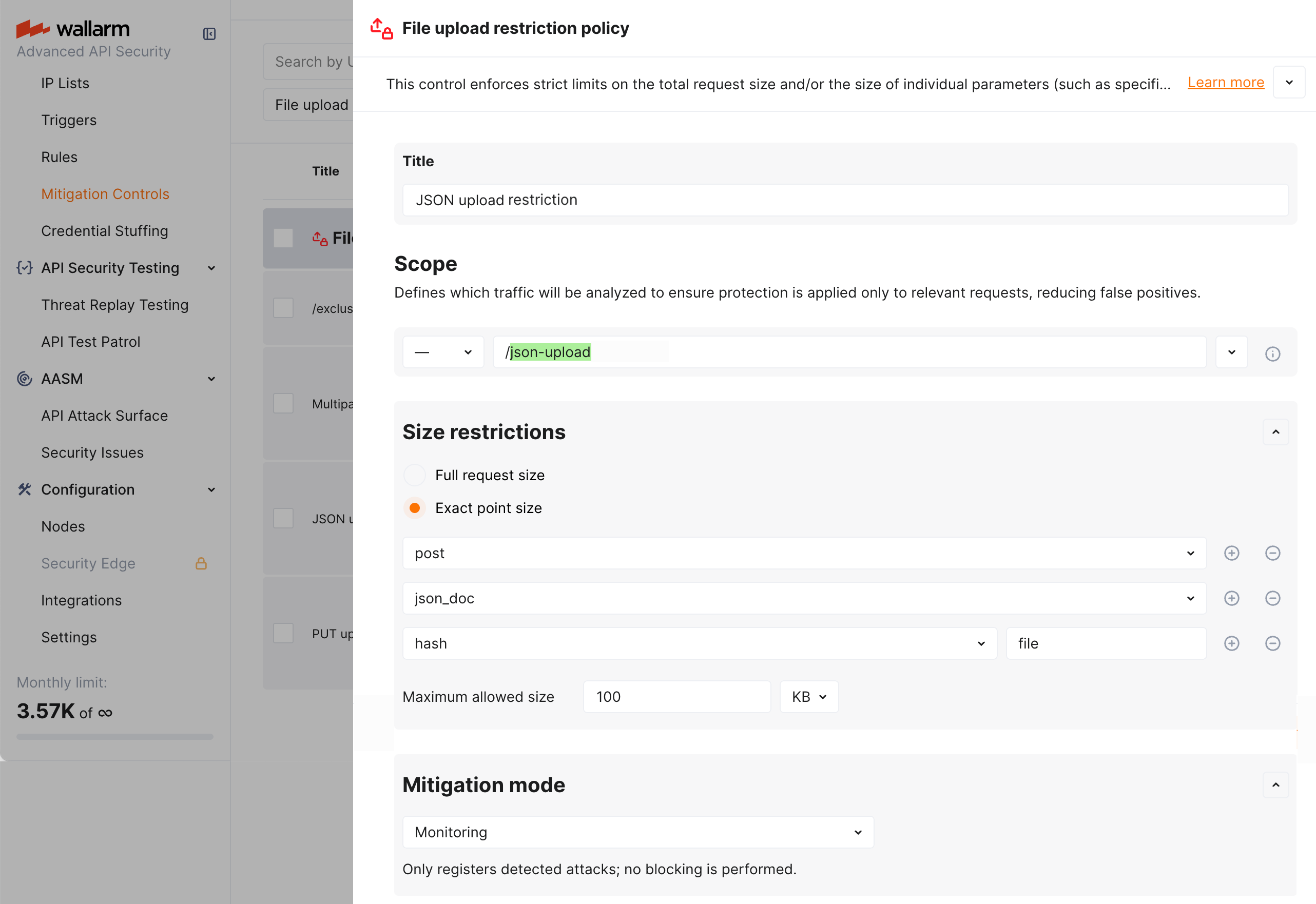
JSON Base64 yükleme kısıtlaması¶
Diyelim ki istek gövdesindeki bir JSON nesnesi içinde (yalnızca bu eylem uygulamanızın /json-upload adresini hedefliyorsa) dosyanın Base64 kodlu 100K+ karakterlik bir dizgesini yükleme girişimlerini (engellemeden) saldırı olarak kaydetmek istiyorsunuz.
Bunu yapmak için, File upload restriction policy mitigation control’ü ekran görüntüsünde gösterildiği gibi ayarlayın:
Yukarıdaki örnekte istek noktası tanımı, Wallarm’ın etiketlerinin bir dizisiyle şu anlama gelecek şekilde yapılmıştır:
-
post- istek gövdesinde -
json_doc- veriler JSON formatında -
hash- ilişkisel dizinin anahtarı için -
file- bu anahtarın değeri
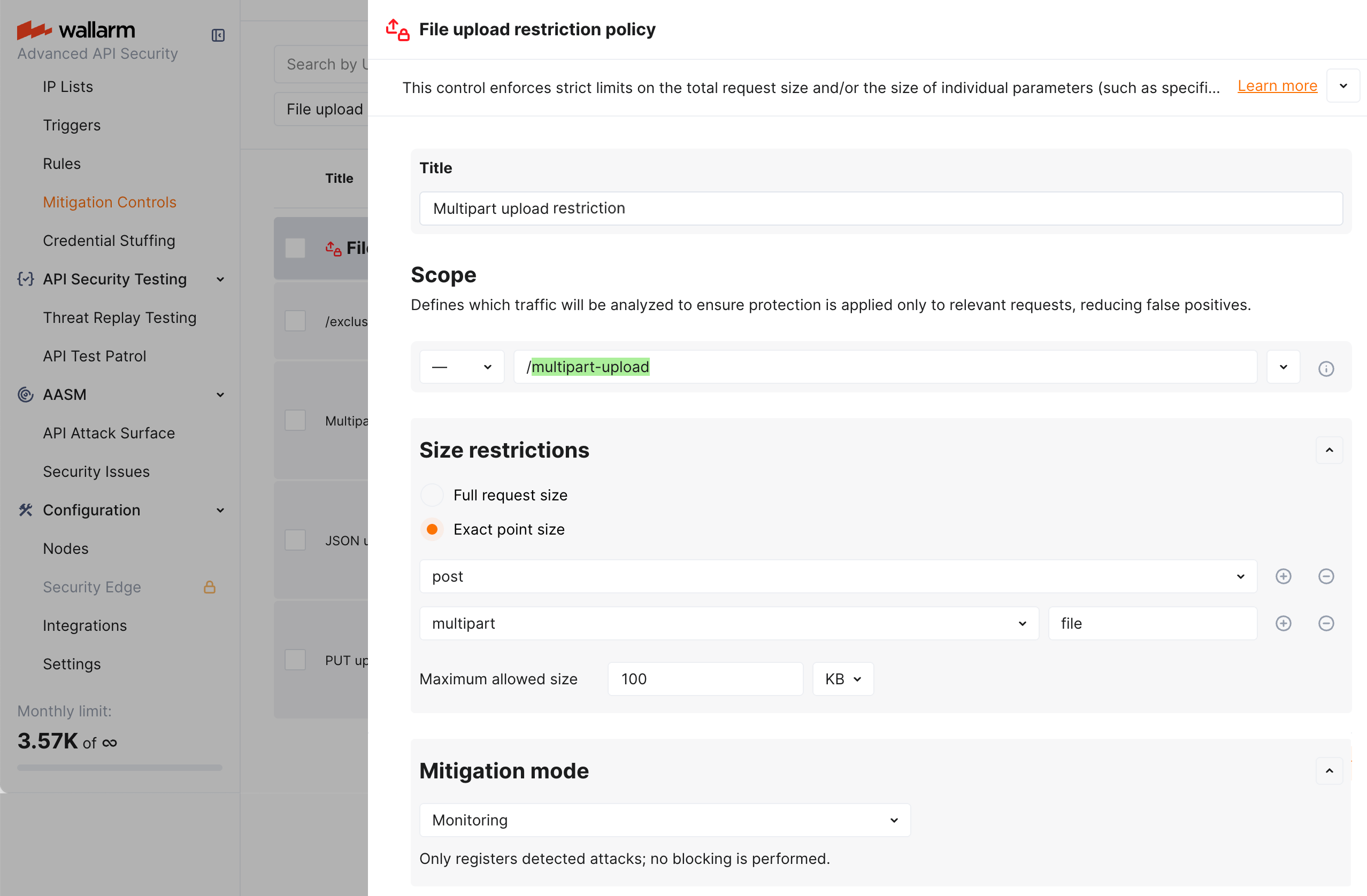
Multipart form data yükleme kısıtlaması¶
Diyelim ki bir dosya yükleme alanı içeren HTML formu aracılığıyla (genelde multipart/form-data içerik türü oluşur) 100K+ dosyalar gönderme girişimlerini (yalnızca bu eylem uygulamanızın /multipart-upload adresini hedefliyorsa) saldırı olarak kaydetmek istiyorsunuz.
Bu sınırlamayı uygulamak için, File upload restriction policy mitigation control’ü ekran görüntüsünde gösterildiği gibi ayarlayın:
Yukarıdaki örnekte istek noktası tanımı, Wallarm’ın etiketlerinin bir dizisiyle şu anlama gelecek şekilde yapılmıştır:
-
post- istek gövdesinde -
multipart-multipart/form-dataiçerik türündeki veriler -
file- formun ürettiği karma içeriğin “dosya parçası”
Rule-based protection¶
Cloud Native WAAP aboneliğinin bir parçası olarak Wallarm, File upload restriction policy rule sağlar.
NGINX Node 6.3.0 veya üzeri gerektirir ve şu an için Native Node tarafından desteklenmemektedir.
Kuralı oluşturma ve uygulama
-
Proceed to Wallarm Console:
- Rules → Add rule or your branch → Add rule.
- Attacks / Incidents → attack/incident → hit → Rule.
- API Discovery (if enabled) → your endpoint → Create rule.
-
Mitigation controls → File upload restriction policy seçin.
-
If request is içinde, kuralın uygulanacağı kapsamı tanımlayın.
-
Size restrictions içinde boyut kısıtlamasını ve Mode’u ayarlayın.
-
İsteğe bağlı olarak, kısıtlamanın uygulanacağı istek noktasını belirtin (ayarlanmazsa kısıtlama tüm istek boyutuna uygulanır).
-
Kuralın derlenmesini ve filtreleme node’una yüklenmesini bekleyin.
Tespit edilen saldırıları görüntüleme¶
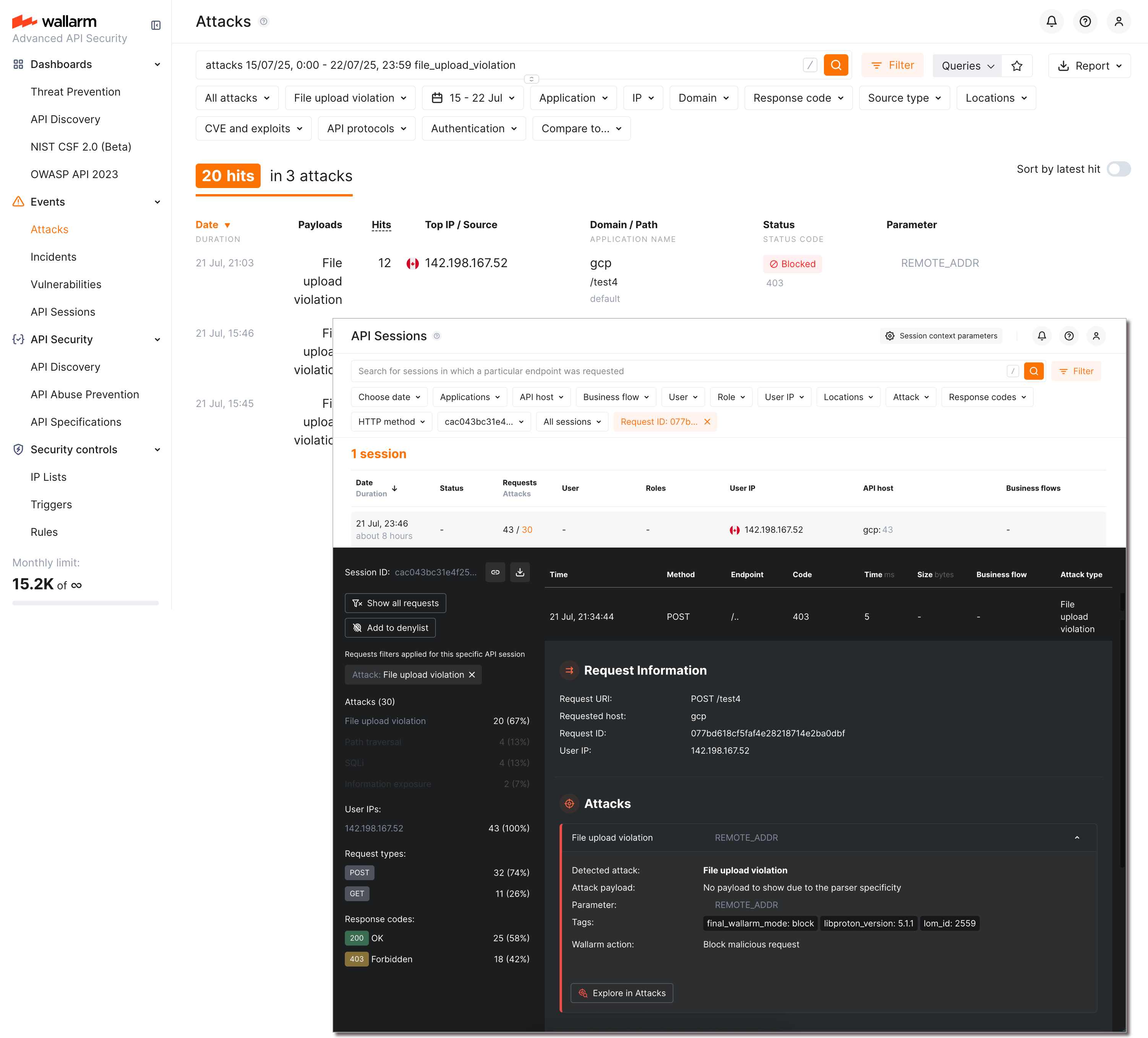
Dosya yükleme kısıtlama politikalarının ihlalleri, Attacks ve API Sessions bölümlerinde file upload violation saldırıları olarak görüntülenir:
İstek ayrıntılarındaki düğmeleri kullanarak Attacks ve API Sessions görünümleri arasında geçiş yapabilirsiniz. Bu saldırı türüne sahip tüm saldırılar/oturumlar, saldırı türü filtresi File upload violation olarak ayarlanarak bulunabilir (ayrıca, Attacks içinde file_upload_violation arama etiketi de kullanılabilir).
Comparison to other measures for preventing unrestricted resource consumption¶
Dosya yükleme kısıtlama politikalarını ayarlamaya ek olarak, Wallarm sınırsız kaynak tüketimini engellemek için başka mekanizmalar da sağlar. Bunlar:
-
Botlar tarafından gerçekleştirilen sınırsız kaynak tüketimini tespit etme ve engelleme (Wallarm'ın API Abuse Prevention özelliği, çalışması için yapılandırılmalıdır).
-
DoS protection mitigation control ( Advanced API Security aboneliği gerektirir).