スキーマベースのテスト  ¶
¶
Wallarmのスキーマベースのテストは、アプリケーションやAPIに対する動的セキュリティテストを実行し、幅広い脆弱性を特定するために設計されています。これは、OWASP Top 10およびOWASP API Security Top 10で説明されているものを含め、網羅的な自動テストにより検出します。
スキーマベースのテストの機能:
-
APIエンドポイントを深く動的に分析します。
-
アプリケーションやAPI自体の脆弱性に加え、基盤となるインフラや環境のセキュリティ誤設定を検出します。
-
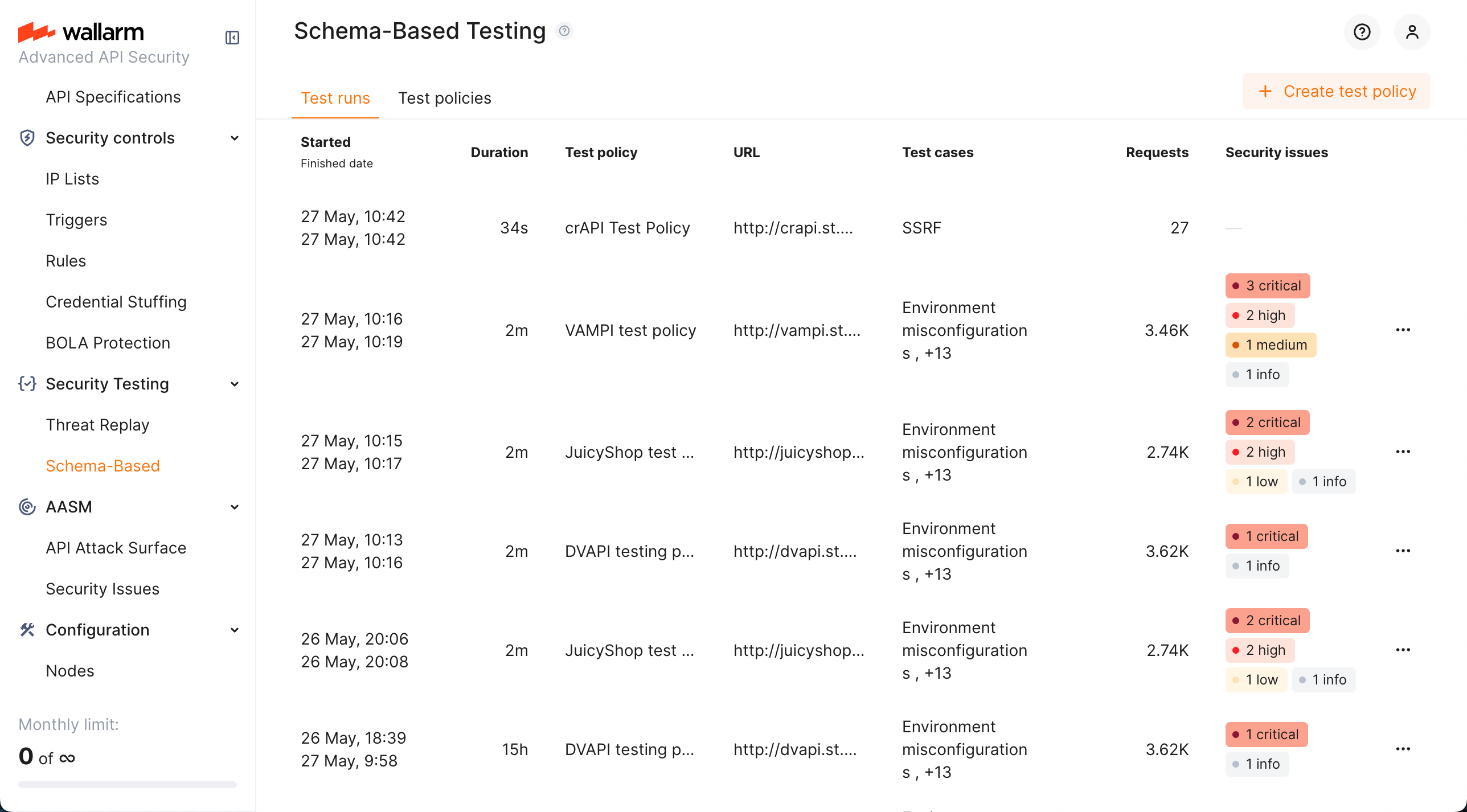
検出された問題はWallarm ConsoleのSecurity Issuesセクションで可視化されます。
-
Dockerコンテナで軽量に実行できます。
仕組み¶
スキーマベースのテストは、以下の手順で使用します。
-
テストポリシーを作成:対象アプリケーションを指定し、そのOpenAPI仕様またはPostmanコレクション、ベースURLを提供し、実行するテストを選択します。
-
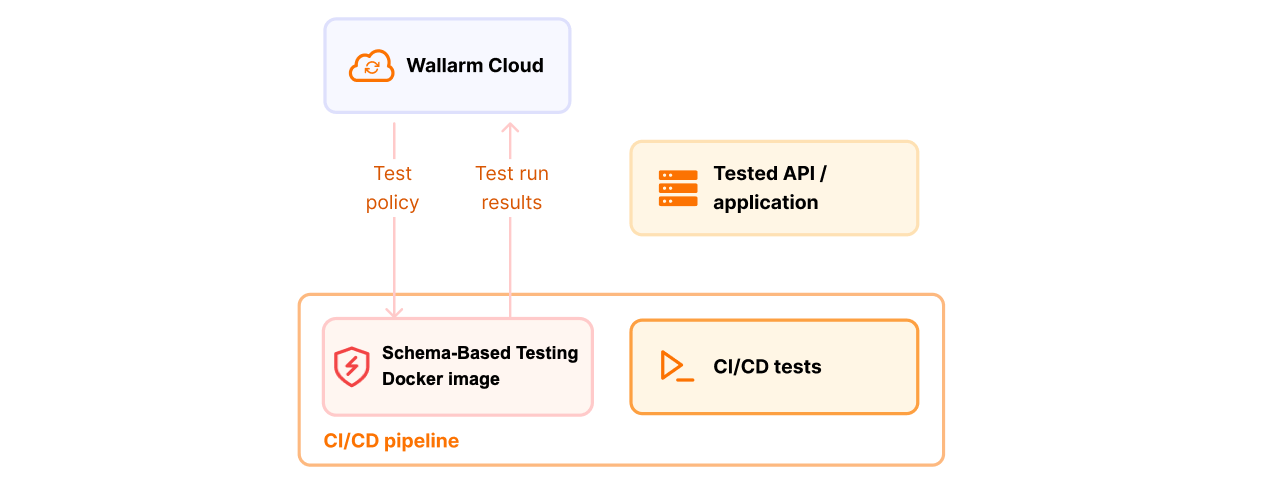
Dockerコマンドをコピー:Test policiesタブでテストポリシーを見つけてクリックし、表示されたDockerコマンドをコピーします。
-
実行と監視:そのコマンドでエージェントを起動します。進行状況の追跡と結果の確認はTest runsタブで行います。
テストの基盤¶
スキーマベースのテストは、次のいずれかを基礎としてテストを行います。
-
OpenAPI仕様(OAS) - APIの正確で機械可読な仕様により、アプリケーション向けの効率的で信頼性の高いテストスイートを構築できます。OASベースのテストは、入力検証、インジェクション、誤設定の検出に重点を置きます。
-
Postmanコレクション - PostmanのAPI設計プラットフォームを使用している場合、そのコレクションに含まれる機能テストを基に、併せてセキュリティテストを構築できます。詳細をご覧ください。Postmanコレクションベースのテストは、複雑なビジネスロジックやアクセス制御の脆弱性に焦点を当てます。
テストの種類¶
OpenAPI仕様に基づくテストでは、スキーマベースのテストはセキュリティ問題を検出するために次の3種類のテストを使用します。
-
環境の誤設定テストは、アプリケーションおよびAPIが動作する環境やインフラ(APIロジックそのものではありません)における脆弱性や誤設定を確認します。例:
- ソースコード、バックアップ、設定ファイルの露出
- アクセス可能な
.git、.env、システムファイル - 安全でないWebサーバー設定(例:ディレクトリリスティング、弱いTLS)
-
GraphQLの脆弱性検出は、GraphQLでよく見られる誤設定10種(API2, API4)を確認します。
-
入力パラメータのテストは、OpenAPI仕様で定義された各入力点(パラメータ、ヘッダーなど)について、アプリケーションレベルの脆弱性を確認します。対象の脆弱性:
- コマンドインジェクション
- CRLFインジェクション
- LFI / RFI
- NoSQLインジェクション
- オープンリダイレクト
- ディレクトリトラバーサル
- リモートコード実行(RCE)
- SQLインジェクション
- SSRF
- SSTI
- XSS
- XXE
- 情報漏えい
有効化とセットアップ¶
スキーマベースのテストを使い始めるには、スキーマベースのテストのセットアップに従って有効化と設定を行います。