Webhook¶
HTTPSプロトコルでWebhookを受信できる任意のシステムに、Wallarmから即時通知を送信するよう設定できます。
通知形式¶
通知は、連携の設定時に選択した内容に応じて、JSON配列または改行区切りJSON(NDJSON)形式で送信されます。通知に含まれるJSONオブジェクトの集合は、送信対象のイベントによって異なります。例:
-
ヒットの検出
[ { "summary": "[Wallarm] New hit detected", "details": { "client_name": "Test Company", "cloud": "EU", "notification_type": "new_hits", "hit": { "domain": "example.com", "heur_distance": 20.714285714285715, "method": "GET", "path": "/", "payloads": [ "1' select version();" ], "point": [ "get", "id" ], "probability": 20.714285714285715, "remote_country": null, "remote_port": 41253, "remote_addr4": "8.8.8.8", "remote_addr6": null, "datacenter": "unknown", "tor": "none", "request_time": 1703519823, "create_time": 1703519826, "response_len": 345, "response_status": 404, "response_time": 359, "stamps": [ 7965 ], "regex": [], "stamps_hash": 271168947, "regex_hash": -2147483648, "type": "sqli", "block_status": "monitored", "brute_counter": "b:1111:xxxxxxxxxxxxxxxx", "final_wallarm_mode": "monitoring", "libproton_version": "4.8.0", "lom_id": 932, "protocol": "rest", "proxy_type": null, "request_id": "xxxxxxxxxxxxxxxx", "wallarm_mode": null, "id": [ "hits_production_1111_202312_v_1", "xxxxxxxxxxxxxxxx" ], "object_type": "hit", "anomaly": 1.0357142857142858, "parameter": "GET_id_value", "applications": [ "default" ] } } }, { "summary": "[Wallarm] New hit detected", "details": { "client_name": "Test Company", "cloud": "EU", "notification_type": "new_hits", "hit": { "domain": "example.com", "heur_distance": 2.5, "method": "GET", "path": "/etc/passwd", "payloads": [ "/etc/passwd" ], "point": [ "uri" ], "probability": 2.5, "remote_country": null, "remote_port": 41254, "remote_addr4": "8.8.8.8", "remote_addr6": null, "datacenter": "unknown", "tor": "none", "request_time": 1703519826, "create_time": 1703519829, "response_len": 345, "response_status": 404, "response_time": 339, "stamps": [ 2907 ], "regex": [], "stamps_hash": -1063984326, "regex_hash": -2147483648, "type": "ptrav", "block_status": "monitored", "brute_counter": "b:1111:xxxxxxxxxxxxxxxx", "final_wallarm_mode": "monitoring", "libproton_version": "4.8.0", "lom_id": 932, "protocol": "none", "proxy_type": null, "request_id": "xxxxxxxxxxxxxxxx", "wallarm_mode": null, "id": [ "hits_production_1111_202312_v_1", "xxxxxxxxxxxxxxxx" ], "object_type": "hit", "anomaly": 0.22727272727272727, "parameter": "URI_value", "applications": [ "default" ] } } } ]{"summary":"[Wallarm] New hit detected","details":{"client_name":"Test Company","cloud":"EU","notification_type":"new_hits","hit":{"domain":"example.com","heur_distance":20.714285714285715,"method":"GET","path":"/","payloads":["1' select version();"],"point":["get","id"],"probability":20.714285714285715,"remote_country":null,"remote_port":41253,"remote_addr4":"8.8.8.8","remote_addr6":null,"datacenter":"unknown","tor":"none","request_time":1703519823,"create_time":1703519826,"response_len":345,"response_status":404,"response_time":359,"stamps":[7965],"regex":[],"stamps_hash":271168947,"regex_hash":-2147483648,"type":"sqli","block_status":"monitored","brute_counter":"b:1111:xxxxxxxxxxxxxxxx","final_wallarm_mode":"monitoring","libproton_version":"4.8.0","lom_id":932,"protocol":"rest","proxy_type":null,"request_id":"xxxxxxxxxxxxxxxx","wallarm_mode":null,"id":["hits_production_1111_202312_v_1","xxxxxxxxxxxxxxxx"],"object_type":"hit","anomaly":1.0357142857142858,"parameter":"GET_id_value","applications":["default"]}} {"summary":"[Wallarm] New hit detected","details":{"client_name":"Test Company","cloud":"EU","notification_type":"new_hits","hit":{"domain":"example.com","heur_distance":2.5,"method":"GET","path":"/etc/passwd","payloads":["/etc/passwd"],"point":["uri"],"probability":2.5,"remote_country":null,"remote_port":41254,"remote_addr4":"8.8.8.8","remote_addr6":null,"datacenter":"unknown","tor":"none","request_time":1703519826,"create_time":1703519829,"response_len":345,"response_status":404,"response_time":339,"stamps":[2907],"regex":[],"stamps_hash":-1063984326,"regex_hash":-2147483648,"type":"ptrav","block_status":"monitored","brute_counter":"b:1111:xxxxxxxxxxxxxxxx","final_wallarm_mode":"monitoring","libproton_version":"4.8.0","lom_id":932,"protocol":"none","proxy_type":null,"request_id":"xxxxxxxxxxxxxxxx","wallarm_mode":null,"id":["hits_production_1111_202312_v_1","xxxxxxxxxxxxxxxx"],"object_type":"hit","anomaly":0.22727272727272727,"parameter":"URI_value","applications":["default"]}} -
脆弱性の検出
[ { summary:"[Wallarm] New vulnerability detected", description:"Notification type: vuln New vulnerability was detected in your system. ID: Title: Test Domain: example.com Path: Method: Discovered by: Parameter: Type: Info Threat: Medium More details: https://us1.my.wallarm.com/object/555 Client: TestCompany Cloud: US ", details:{ client_name:"TestCompany", cloud:"US", notification_type:"vuln", vuln_link:"https://us1.my.wallarm.com/object/555", vuln:{ domain:"example.com", id:null, method:null, parameter:null, path:null, title:"Test", discovered_by:null, threat:"Medium", type:"Info" } } } ]{"summary":"[Wallarm] New vulnerability detected","description":"Notification type: vuln\nNew vulnerability was detected in your system.\nID: \nTitle: Test\nDomain: example.com\nPath: \nMethod: \nDiscovered by: \nParameter: \nType: Info\nThreat: Medium\nMore details: https://us1.my.wallarm.com/object/555\nClient: TestCompany\nCloud: US","details":{"client_name":"TestCompany","cloud":"US","notification_type":"vuln","vuln_link":"https://us1.my.wallarm.com/object/555","vuln":{"domain":"example.com","id":null,"method":null,"parameter":null,"path":null,"title":"Test","discovered_by":null,"threat":"Medium","type":"Info"}}}
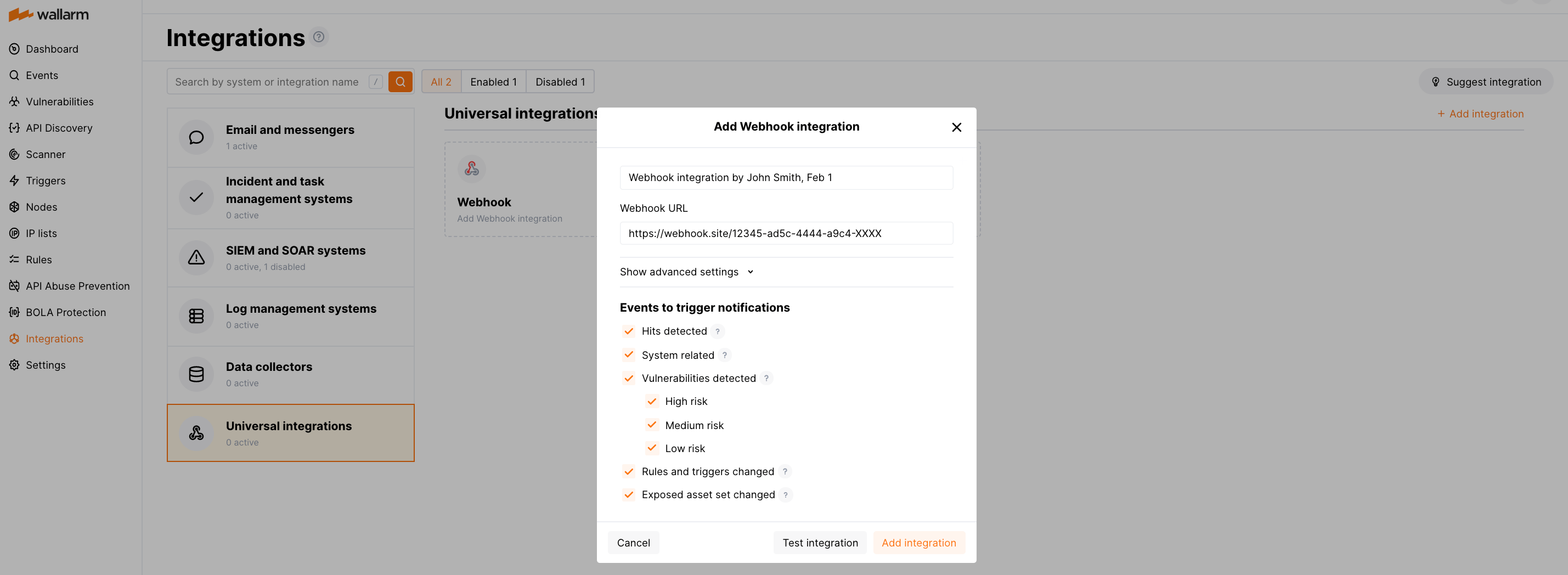
連携の設定¶
-
Wallarm UI → Integrationsを開きます。
-
Webhookブロックをクリックするか、Add integrationボタンをクリックしてWebhookを選択します。
-
連携名を入力します。
-
送信先のWebhook URLを入力します。
-
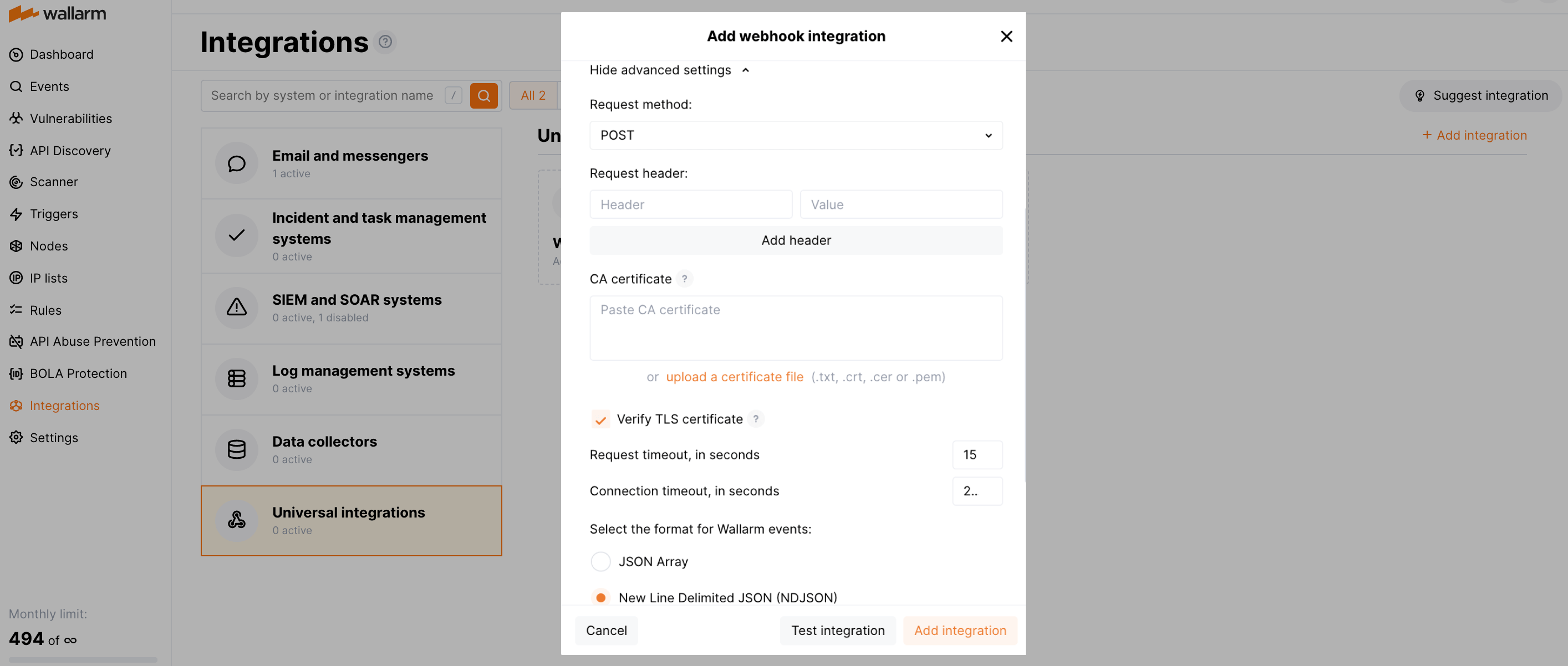
必要に応じて詳細設定を構成します:
- Request method:
POSTorPUT. By default, POST requests are sent. - Request header and its value if the server requires a non-standard header to execute the request. The number of headers is not limited.
- CA certificate: certificate of CA that signed a server certificate. If CA is publicly trusted, this field is optional. If a server certificate is self-signed, this field is required and must contain a certificate of your own CA that signed a server certificate.
- Verify TLS certificate: this setting allows to disable verification of the specified server certificate. By default, Wallarm verifies whether a server certificate is signed by a publicly trusted CA. We do not recommend disabling the verification of production server certificates. If your server uses a self-signed TLS certificate, you can add a self-signed CA certificate to allow sending requests to this server.
- Request timeout, in seconds: if the server does not respond to the request within the specified time, the request fails. By default: 15 seconds.
- Connection timeout, in seconds: if the connection to the server cannot be established during the specified time, the request fails. By default: 20 seconds.
- Wallarm data format: either a JSON Array (default) or a New Line Delimited JSON (NDJSON).
- Request method:
-
通知をトリガーするイベントタイプを選択します。
利用可能なイベントの詳細:
-
Hits detected except for:
- Experimental hits detected based on the custom regular expression. Non-experimental hits trigger notifications.
- Hits not saved in the sample.
Optionally include the
headersobject with hit headers in hit logs. If disabled, headers are not included in the logs. -
System related:
- User changes (newly created, deleted, role change)
- Integration changes (disabled, deleted)
- Application changes (newly created, deleted, name change)
- Errors during regular update of specifications used for rogue API detection or API specification enforcement
- Rules and triggers changed (creating, updating, or deleting the rule or trigger)
- Security issues detected by all methods, all or only for the selected risk levels:
- Critical risk
- High risk
- Medium risk
- Low risk
- Info risk
- On an hourly basis, you can get a notification with the number of requests processed during the previous hour
-
-
Test integrationをクリックして、設定の正しさ、Wallarm Cloudの可用性、および通知形式を確認します。テスト通知は、改行区切りJSON (NDJSON)を選択している場合でも、常にJSON配列形式で送信されます。
-
Add integrationをクリックします。
Wallarm Cloud IP addresses
To provide Wallarm Cloud access to your system, you may need a list of its public IP addresses:
追加アラートの設定¶
Besides the notifications you have already set up through the integration card, Wallarm triggers allow you to select additional events for notifications:
-
Number of attacks, hits or incidents per time interval (day, hour, etc.) exceeds the set number
What is not counted
- For attacks:
- The experimental attacks based on the custom regular expressions.
- For hits:
- The experimental hits based on the custom regular expressions.
- Hits not saved in the sample.
- For attacks:
-
Changes in API took place
-
IP address was denylisted
-
New rogue API (shadow, orphan, zombie) was detected
-
New user was added to the company account
For condition detailing, you can add one or more filters. As soon, as condition and filters are set, select the integration through which the selected alert should be sent. You can select several integrations simultaneously.
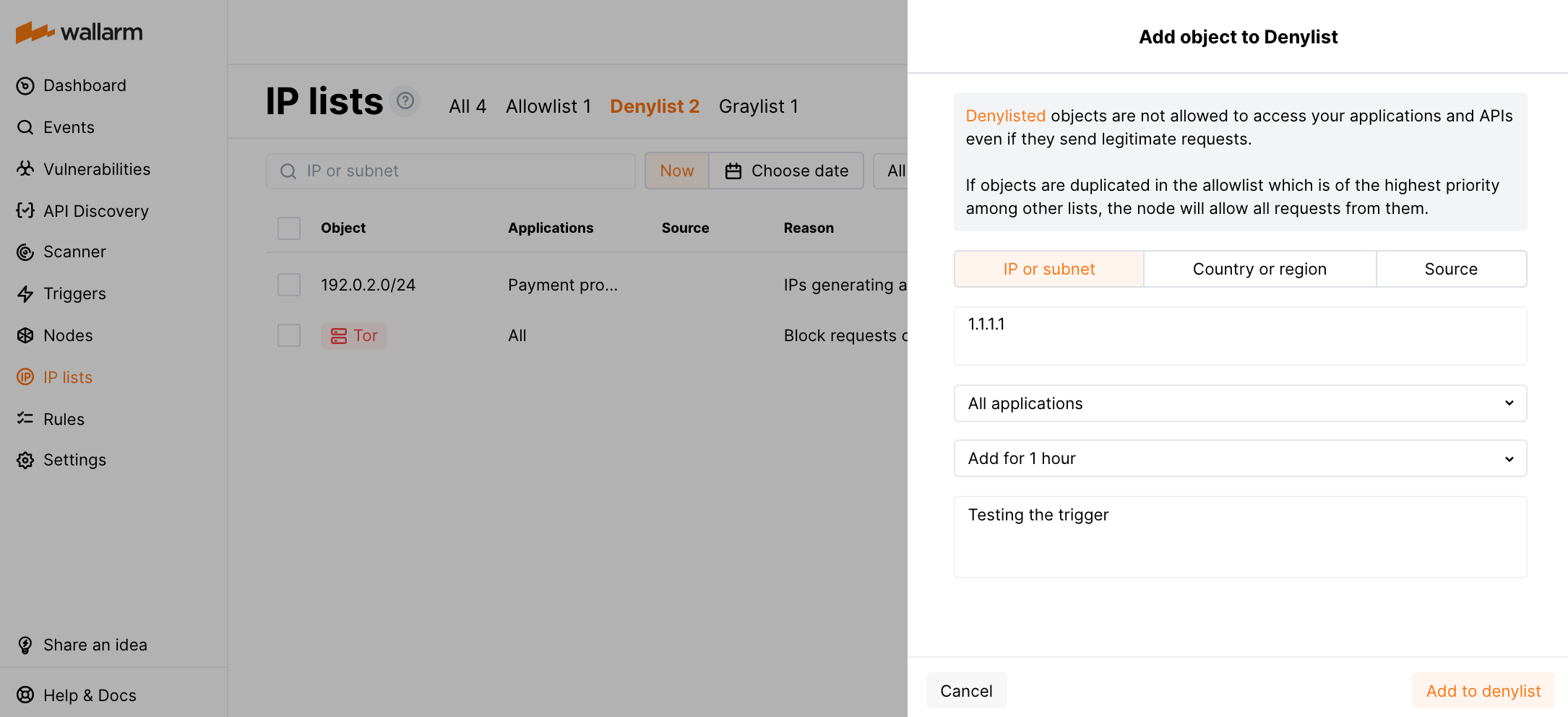
例: IPアドレスがdenylistに追加された場合にWebhook URLへ通知¶
IPアドレスがdenylistに追加されると、このイベントに関するWebhookがWebhook URLに送信されます。
トリガーをテストするには:
-
Wallarm Console → IP lists → Denylistを開き、IPアドレスをdenylistに追加します。例えば:
-
次のWebhookがWebhook URLに送信されたことを確認します:
[ { "summary": "[Wallarm] Trigger: New IP address was denylisted", "description": "Notification type: ip_blocked\n\nIP address 1.1.1.1 was denylisted until 2021-06-10 02:27:15 +0300 for the reason Produces many attacks. You can review blocked IP addresses in the \"Denylist\" section of Wallarm Console.\nThis notification was triggered by the \"Notification about denylisted IP\" trigger. The IP is blocked for the application Application #8.\n\nClient: TestCompany\nCloud: EU\n", "details": { "client_name": "TestCompany", "cloud": "EU", "notification_type": "ip_blocked", "trigger_name": "Notification about denylisted IP", "application": "Application #8", "reason": "Produces many attacks", "expire_at": "2021-06-10 02:27:15 +0300", "ip": "1.1.1.1" } } ]Notification about denylisted IPはトリガー名ですTestCompanyはWallarm Consoleの貴社アカウント名ですEUは貴社アカウントが登録されているWallarm Cloudです
連携の無効化と削除¶
You can delete or temporarily disable the integration. While deleting stops sending notificatioins and completely deletes all configuration, disabling just stops sending notifications which you can at any moment re-enable with the same settings.
If for the integration the System related events are selected to trigger notifications, Wallarm will notify about both of these actions.
システムの利用不可および連携パラメータの誤り¶
Notifications to the system are sent via requests. If the system is unavailable or integration parameters are configured incorrectly, the error code is returned in the response to the request.
If the system responds to Wallarm request with any code other than 2xx, Wallarm resends the request with the interval until the 2xx code is received:
-
The first cycle intervals: 1, 3, 5, 10, 10 seconds
-
The second cycle intervals: 0, 1, 3, 5, 30 seconds
-
The third cycle intervals: 1, 1, 3, 5, 10, 30 minutes
If the percentage of unsuccessful requests reaches 60% in 12 hours, the integration is automatically disabled. If you receive system notifications, you will get a message about automatically disabled integration.