Multi-Cloud and Multi-Region Deployment of Security Edge Inline  ¶
¶
You can deploy the inline Edge Nodes across multiple regions and cloud providers to achieve geo‑redundancy and low latency.
When configuring Security Edge, you can select one or more regions across the supported cloud providers - AWS and Azure.
Multi-region deployment¶
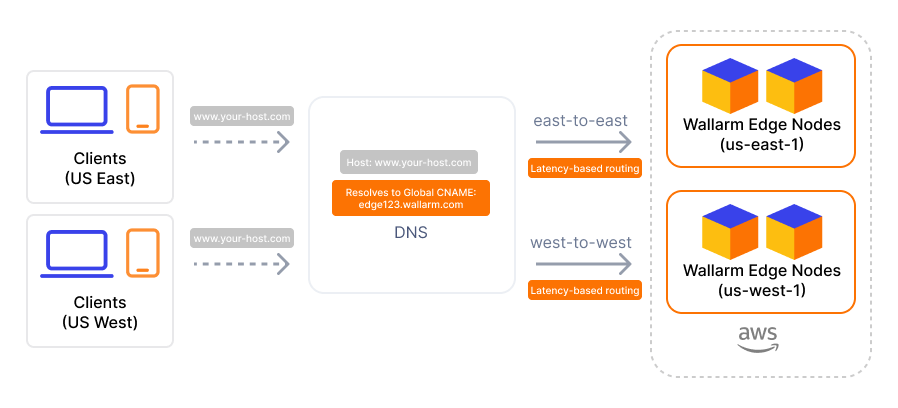
When selecting multiple regions within a single cloud provider, traffic is routed based on latency - each request goes to the nearest available region.
This is the most common setup, recommended when you serve requests from multiple locations.
Available regions depend on your Wallarm Cloud (US → US regions, EU → EU regions and UAE North).
Multi-cloud deployment¶
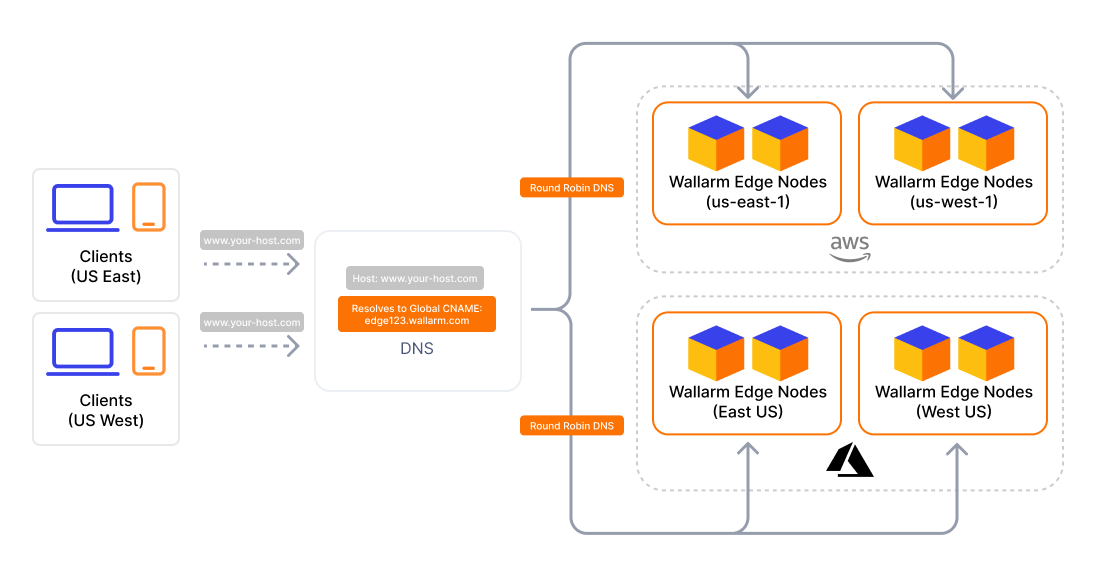
When multiple regions across different cloud providers are selected, all requests are distributed across the selected regions and providers using a round‑robin strategy, regardless of latency.
This setup is recommended in the following cases:
-
Cloud provider redundancy - traffic is distributed across all selected providers, ensuring that if one becomes unavailable (e.g., AWS), others (e.g., Azure) continue handling traffic without disruption.
-
Regional high availability - for example, selecting both
AWS US East 1andAzure East USensures traffic remains balanced across regions, and service continues even if one region or provider becomes unavailable.
Wallarm IP ranges for origin access¶
We recommend securing connections from Security Edge to your origins with mTLS. This avoids the need to update IP allowlists when Wallarm IPs change.
If mTLS cannot be used, allow incoming traffic from the Wallarm IP addresses of the selected regions:
-
AWS
-
Azure
CNAME records¶
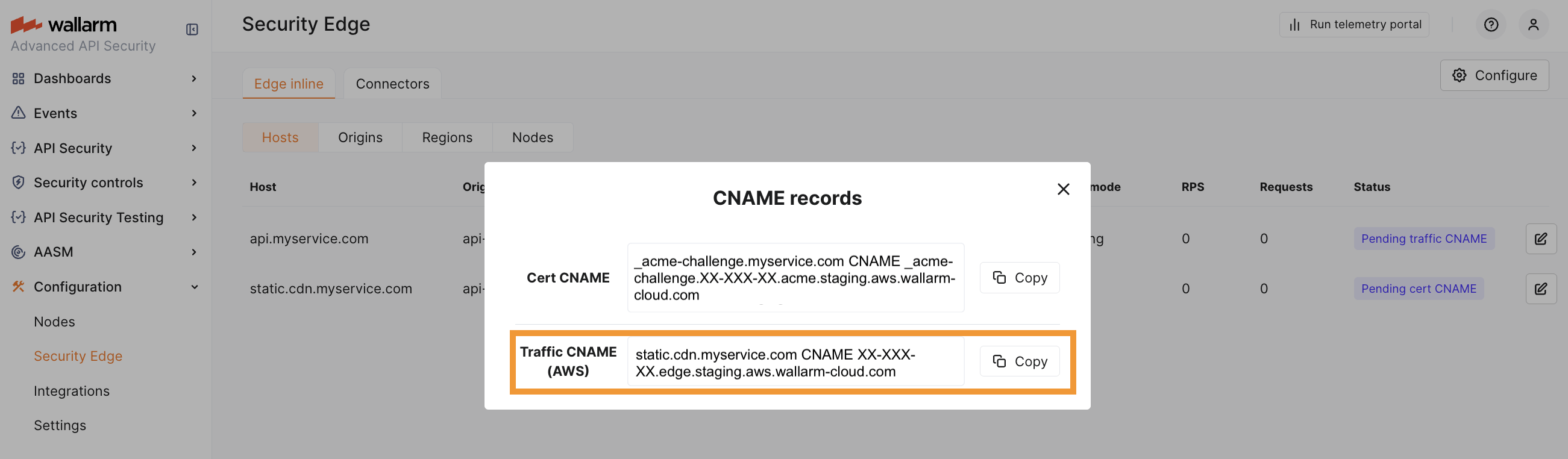
If your protected host is a third-level (or higher-level) domain (e.g., api.example.com), you need to specify the CNAME record pointing to the Wallarm‑proided FQDN in your DNS zone. This record is returned as the Traffic CNAME.
-
Single cloud deployment: use the Traffic CNAME for the selected cloud provider.
-
Multi-cloud deployment: use the Traffic CNAME (Global) to automatically distribute traffic across all selected regions and providers.
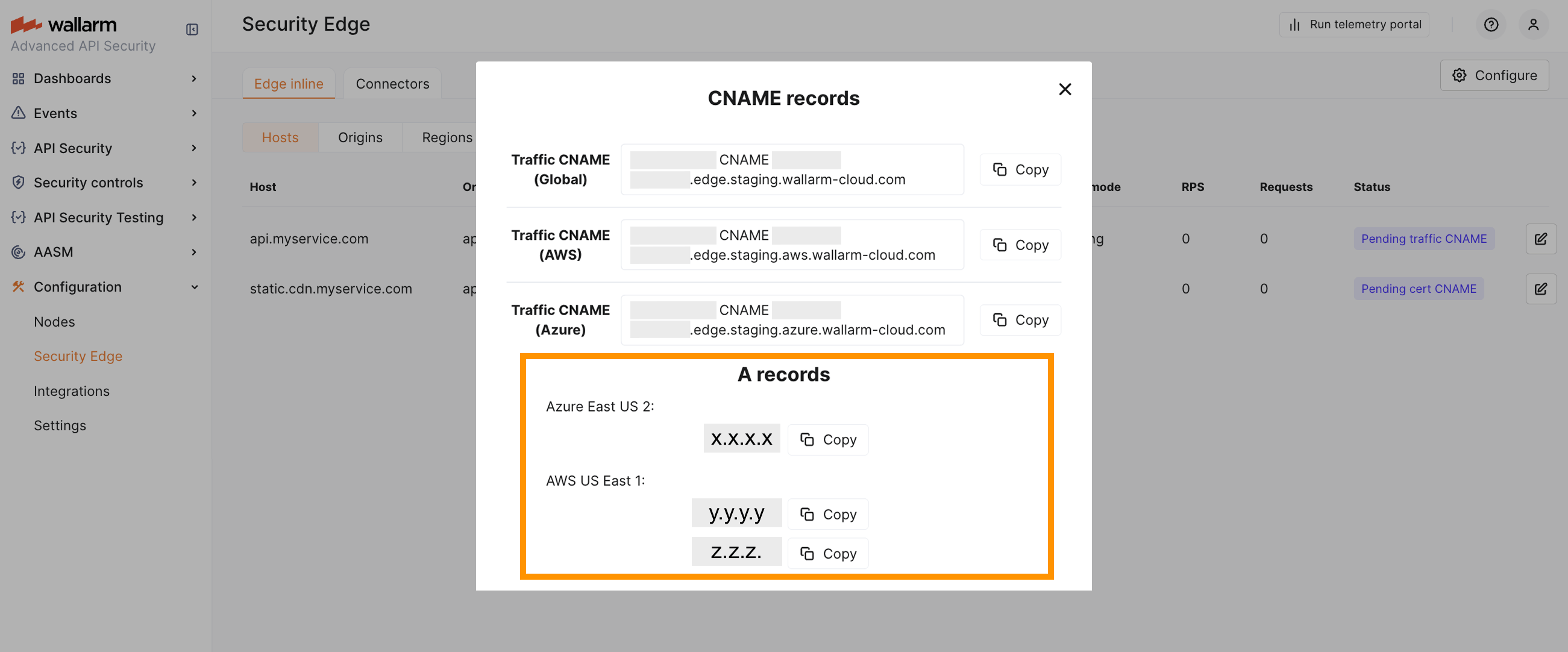
Per-provider CNAMEs are also available if you need to enforce routing to a specific provider - for example, to test latency or performance across providers.
A records¶
If your protected host is an apex domain (e.g., example.com), a CNAME cannot be used. In this case, the DNS setup must use A records, which are returned once the deployment becomes Active.
If you have selected multiple regions or providers for Edge Node deployment, you need to configure all returned A records in your DNS zone.
Traffic routing in this case is managed by your DNS provider. By default, most DNS providers use round-robin logic, but some may support latency-based routing as well.
Removing a cloud provider or a region¶
-
Before removing a cloud provider, switch your DNS setup to use the Traffic CNAME of the remaining provider.
When a cloud provider is removed, its Traffic CNAME is deleted.
If only one provider remains, the Traffic CNAME (Global) is also removed and becomes unavailable.
-
Before removing a region, update your A records accordingly.
If a region is removed, the associated A records will no longer be available.