mTLS for Edge Node to Origins  ¶
¶
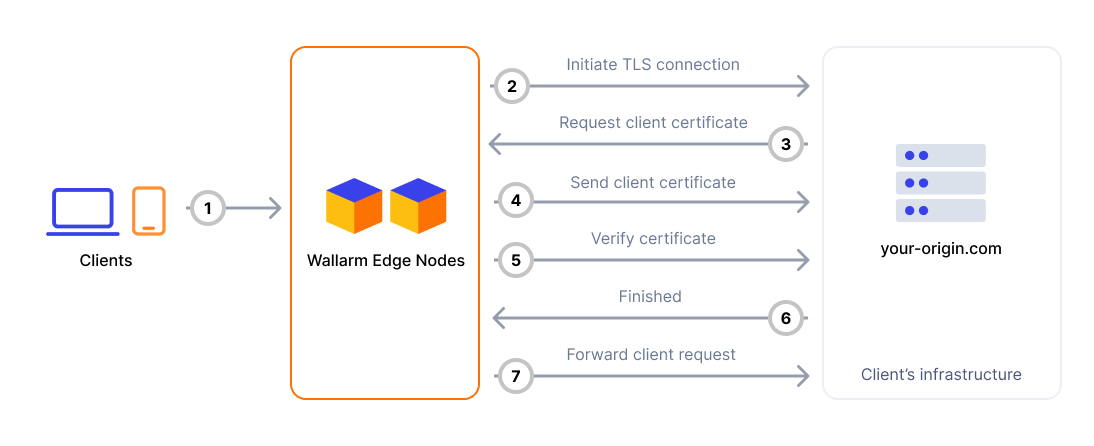
Mutual TLS (mTLS) allows the Wallarm Edge Node to authenticate itself to your origin servers using a client certificate. This ensures that your origins accept requests only from trusted sources.
When configuring Security Edge, you can generate and upload client certificates for the Edge Nodes.
Version requirements
mTLS is supported starting from Edge Node version 5.3.14-200.
How it works¶
When mTLS is enabled for an origin:
-
Before forwarding filtered traffic to your origin, the Edge Node presents a client certificate during the TLS handshake.
-
The origin verifies the certificate against a trusted CA (Certificate Authority) bundle.
-
If the certificate is valid and matches the expected parameters (e.g., Common Name or Subject Alternative Name), the connection is established and the request is accepted.
Enabling mTLS¶
You can upload multiple certificates and assign different ones to different origins.
-
Generate a client certificate and private key pair, signed by a trusted CA. They must meet the following requirements:
-
Client certificate: X.509, PEM format.
Must include the
Extended Key Usage (EKU)extension set toClient Authentication. -
Private key: PEM format, must correspond to the client certificate.
- CA bundle: PEM format, must include the issuing certificate authority for the client certificate.
- Signature algorithm: RSA, ED25519, ECDSA with the secp256r1, secp384r1, and secp521r1 curves.
-
-
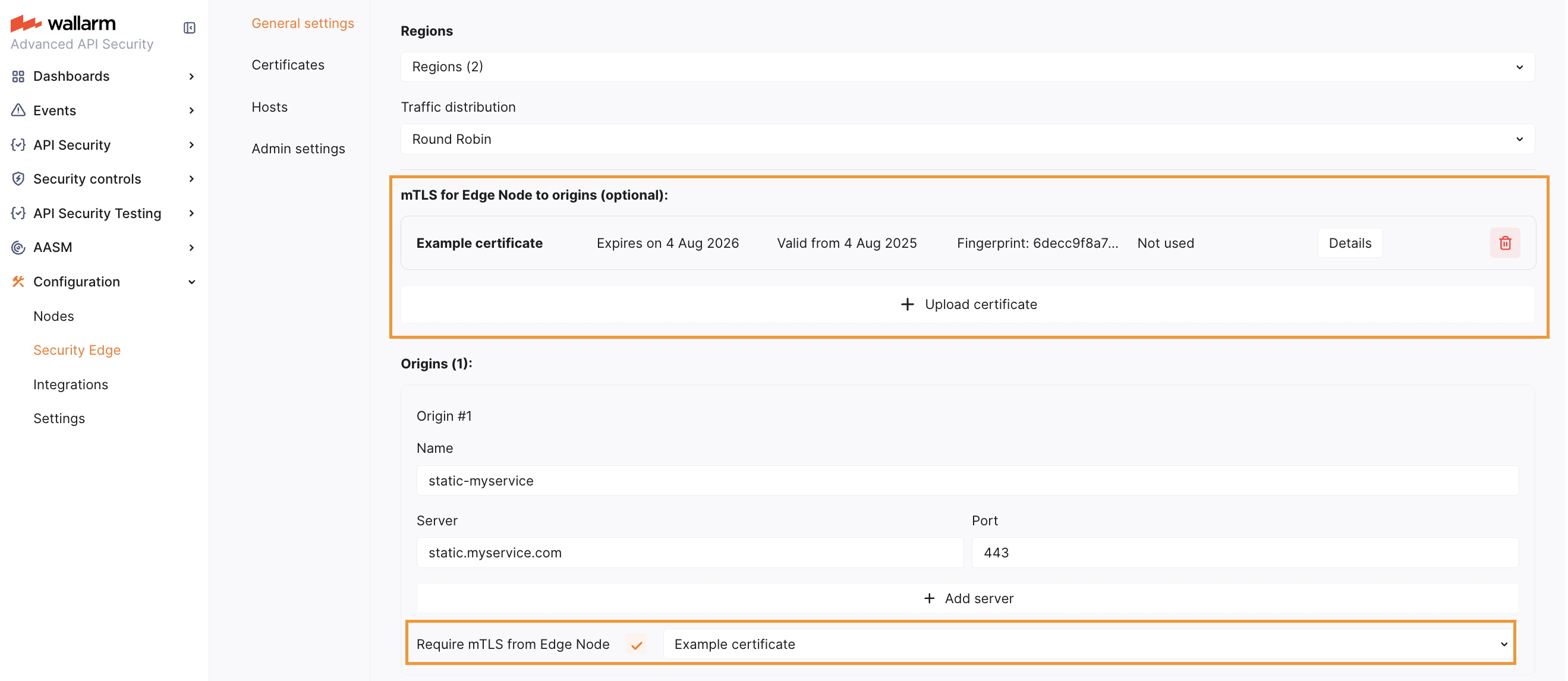
In Wallarm Console → Security Edge → Configure, under General settings, upload the certificate, private key, and CA bundle.
-
In the Origins section, enable Require mTLS from Edge Node for the relevant origin and select the appropriate certificate.
Each origin can use a different certificate if needed.
-
Save the settings.
-
Configure your origin to require mTLS for incoming connections. Trust the CA bundle used to issue the client certificate.