Security Edge Inline Deployment  ¶
¶
To deploy the Wallarm Security Edge for inline traffic analysis, follow this guide.
Requirements¶
-
Security Edge subscription (free or paid)
-
Ability to edit DNS records for your domains to verify ownership and route traffic to Wallarm
-
Selecting gRPC traffic for locations is supported starting from Edge Node version 6.6.0
Configuration flow¶
To run the Edge inline, go to the Wallarm Console → Security Edge → Inline → Configure. If this section is unavailable, contact sales@wallarm.com to access the required subscription.
On the Free Tier, after deploying Edge Nodes via Quick setup, the Security Edge section lets you adjust settings.
You can update the Edge Node deployment settings at any time. The Node will be re‑deployed with existing CNAME and A records remaining unchanged.
See a demo of the full configuration flow:
1. Provider and region¶
Choose one or more regions (AWS or Azure) for Edge Node deployment. Select locations close to your APIs for optimal latency.
Available regions depend on your Wallarm Cloud (US → US regions, EU → EU regions and UAE North).
More about multi-region and multi-cloud deployment
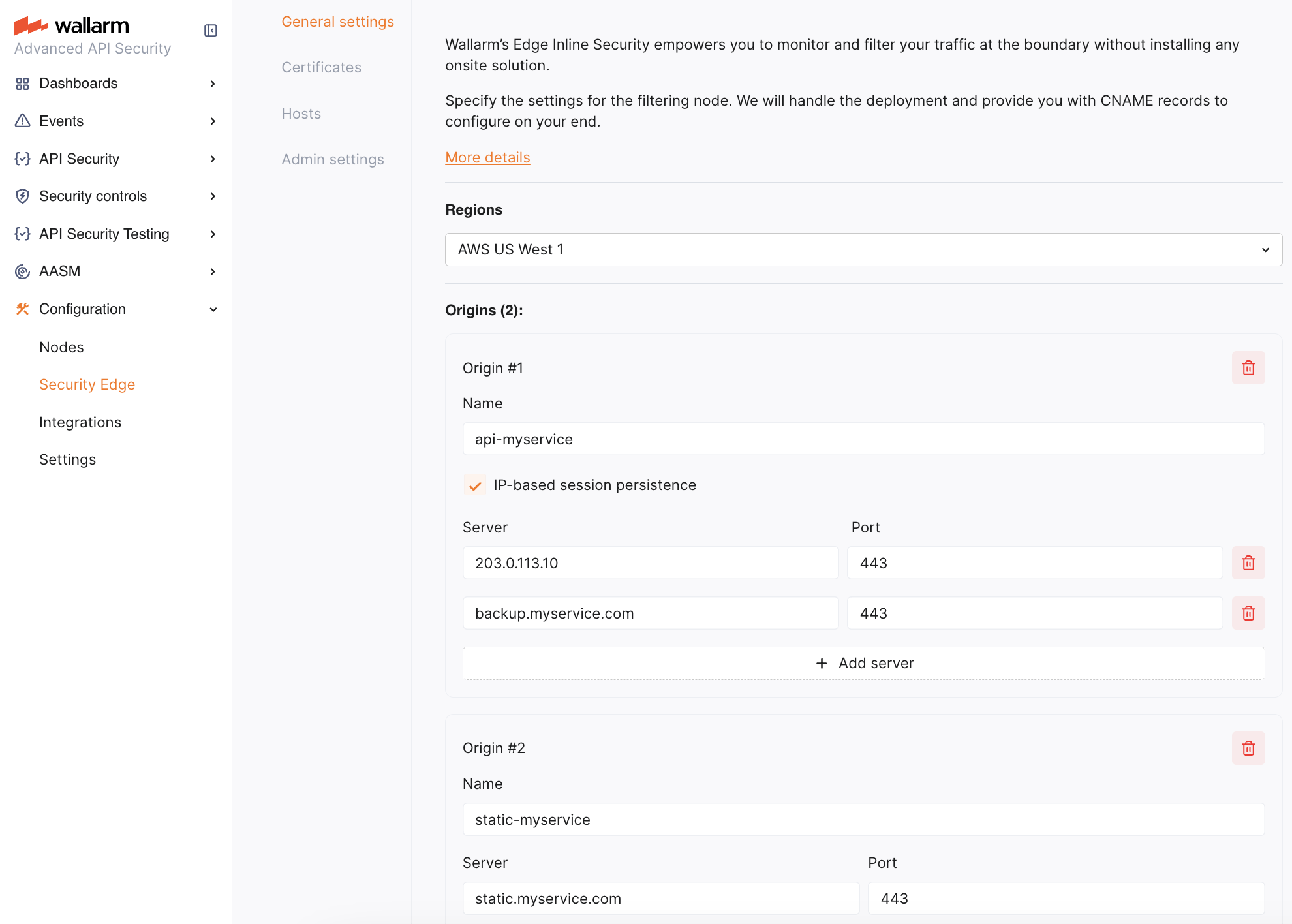
2. Origins¶
Specify origins to which the Edge Node will forward filtered traffic. For each origin, provide a server IP address or FQDN with an optional port (default: 443).
If an origin has multiple servers, you can specify all of them. Requests are distributed as follows:
-
The round-robin algorithm is used. The first request is sent to the first server, the second to the next, and so on, cycling back to the first server after the last.
-
With IP-based session persistence, traffic from the same IP consistently routes to the same server.
Securing access to origins
To restrict your origins to trusted traffic only, allow Edge Node connections using one of the methods:
-
(Recommended) Authenticate Edge Nodes with mTLS. This avoids issues if Wallarm IPs change.
-
Allow traffic only from the IP ranges of the selected deployment regions (IPs may change).
Show Wallarm IP ranges
-
AWS
-
Azure
-
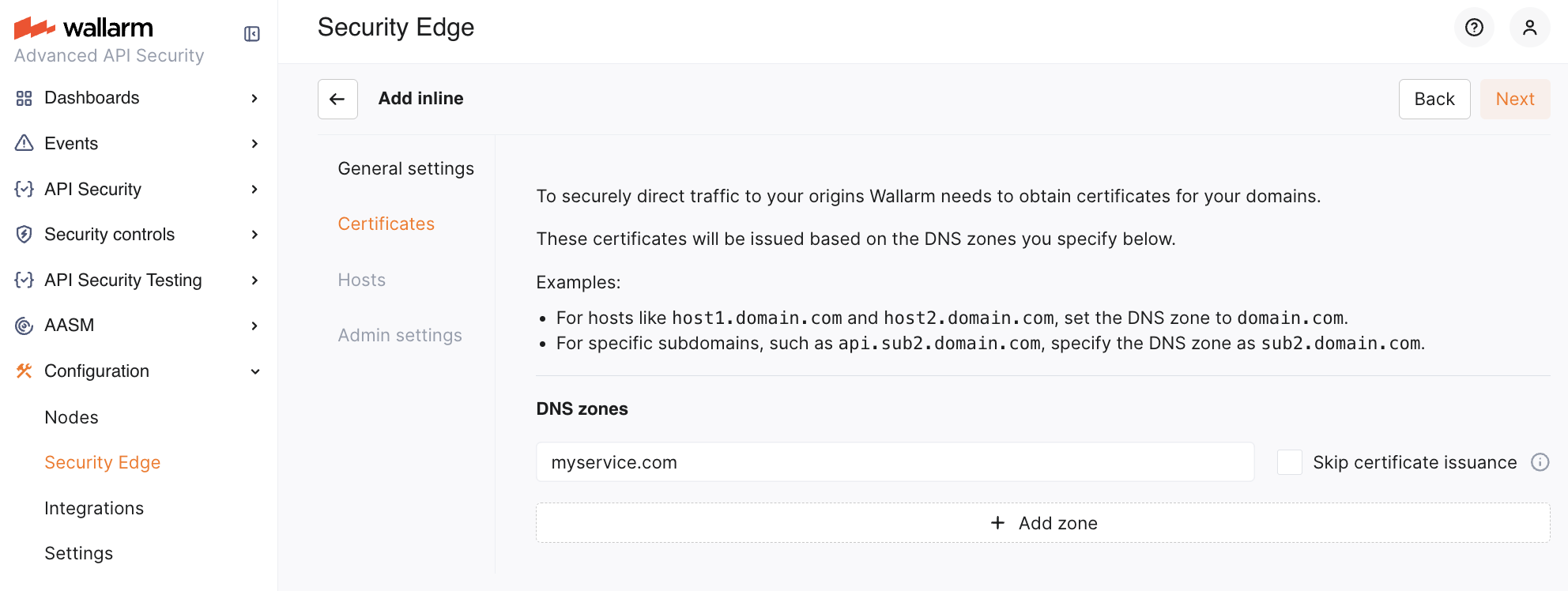
3. Certificates¶
-
If the Edge Inline Node is deployed as a direct, Internet-facing solution, Wallarm requires certificates to securely route traffic to your origin servers. Certificates are issued based on the DNS zones specified in this section.
Once configuration is complete, Wallarm provides a CNAME for each DNS zone. Add this CNAME record to your DNS settings to verify domain ownership and complete the certificate issuance process.
-
If your origin servers are behind a third-party service (e.g., a CDN or a DDoS protection provider like Cloudflare or Akamai) that proxies traffic, certificate issuance is not required. In this case, select the Skip certificate issuance option.
You can specify multiple DNS zones, each with a different certificate issuance approach.
CAA records
Some organizations use CAA DNS records to restrict which Certificate Authorities (CAs) are allowed to issue certificates for their domains.
If you maintain CAA records, make sure to allow Let's Encrypt with the Wallarm Account ID, otherwise certificates for Security Edge cannot be issued:
0 issue "letsencrypt.org;validationmethods=dns-01;accounturi=https://acme-v02.api.letsencrypt.org/acme/acct/2513765531"
You can check your current CAA records with:
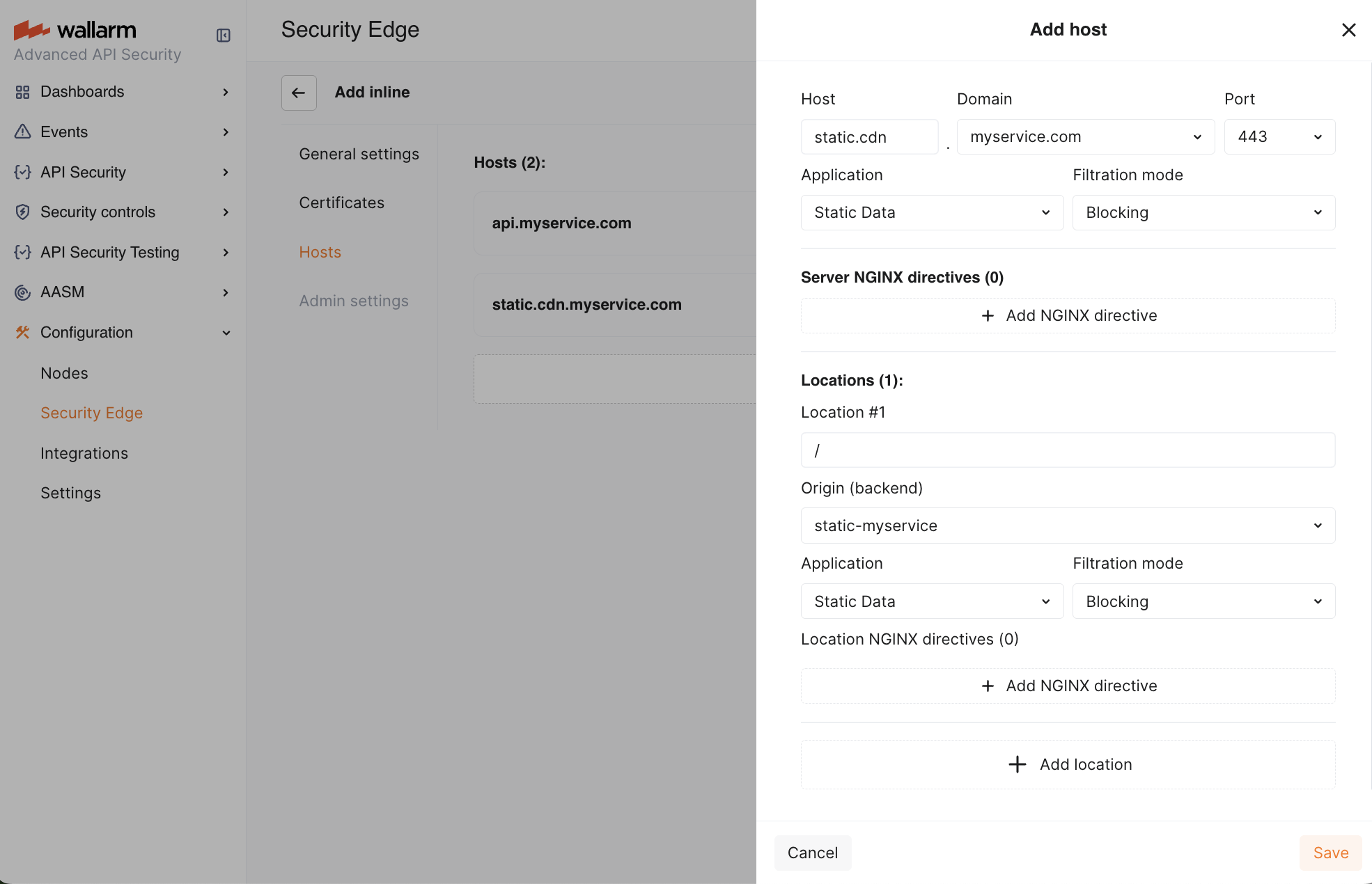
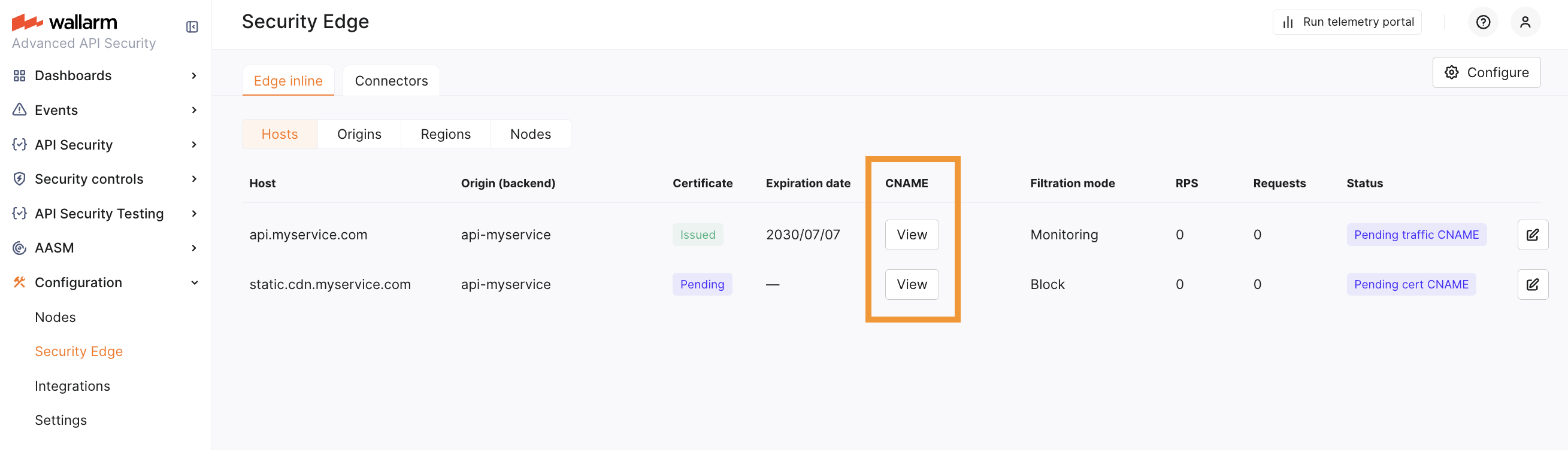
4. Hosts¶
Specify the public domains, ports and subdomains that will direct traffic to the Edge Node for analysis.
Apex domains
Use www.example.com instead of apex domains when possible. Or configure a redirection from the apex domain to www.*. This allows Wallarm to use a global CNAME and avoid manual traffic balancing with A records.
-
Specify your hosts. Each host entry must match a DNS zone (when specified in the Certificates section) and differ from origins to avoid routing loops.
Allowed ports
Directing traffic from HTTP ports to the Edge Node is not allowed. The following ports are supported:
- 443
- 1024–49151 (except: 9000, 9003, 9010, 9113, 9091, 9092, 18080)
-
(Optional) Associate the host's traffic with a Wallarm application to categorize and manage different API instances or services on the Wallarm platform.
-
Set the Wallarm mode for each host.
-
(Optionally) Select the traffic type for each host (HTTP/1.1 or HTTP/2).
-
(Optionally) Customize server NGINX directives. Defaults follow standard NGINX values.
-
For each host, define the configuration for the root location (
/):- Origin where the Wallarm Node will forward the filtered traffic (if no other location-specific settings are defined). The location's path is automatically appended to the origin.
- (Optionally) Wallarm application.
- Filtration mode.
- Traffic type (gRPC, GraphQL, WebSocket, or GraphQL (WebSocket)).
-
(Optionally) For each host, select the block page to show when a malicious request is blocked. By default, the standard NGINX 403 Forbidden page is selected. You can also choose the Wallarm-branded block page or a custom one.
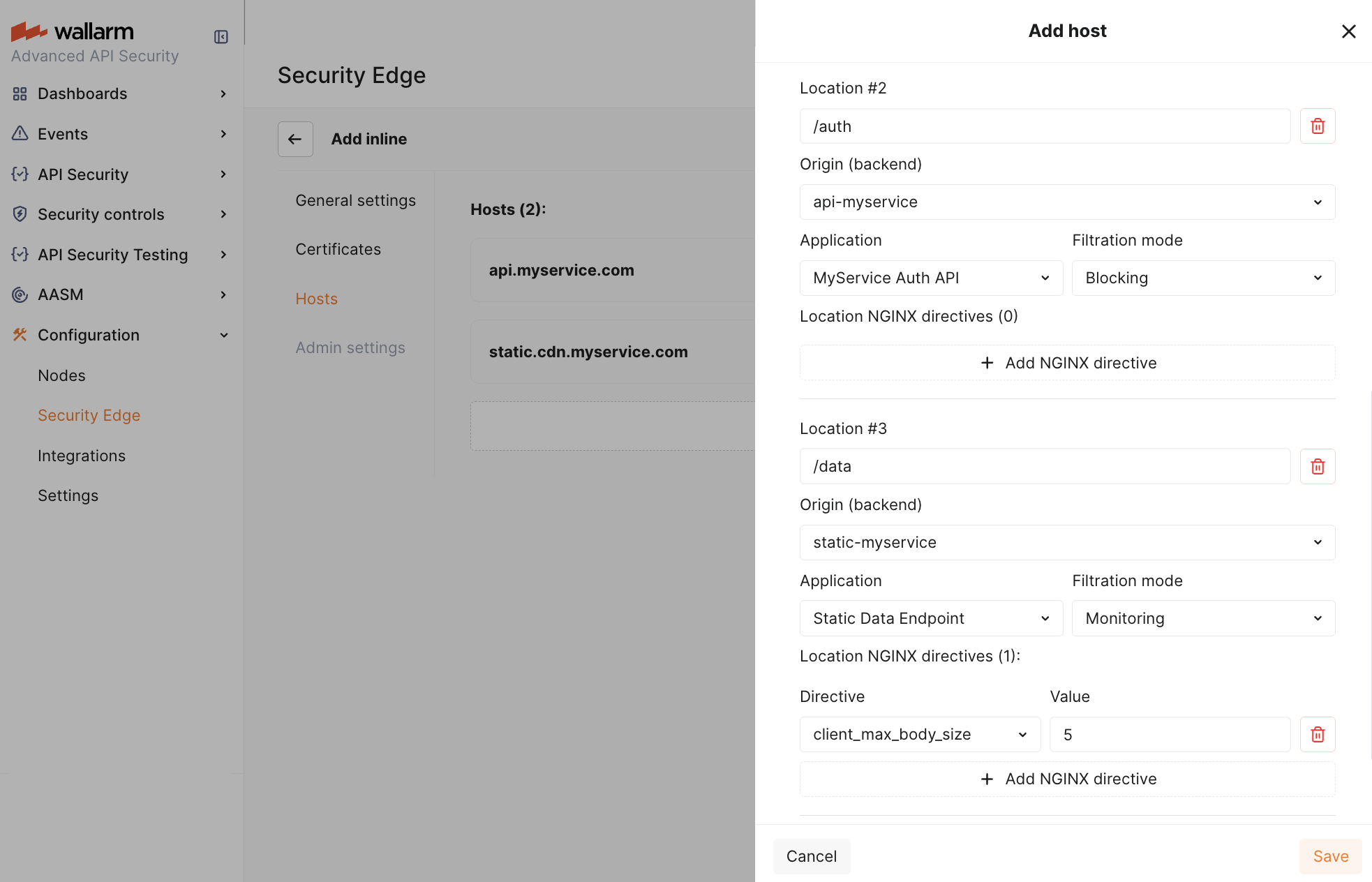
5. Locations¶
For specific locations within hosts, you can further customize:
-
Origin. The path defined in the location will automatically append to the origin.
-
Wallarm application.
-
Filtration mode.
-
Traffic type (gRPC, GraphQL, WebSocket, or GraphQL (WebSocket)).
-
Location NGINX directives. Defaults follow standard NGINX values.
Each location inherits settings from the host and root location, unless specifically overridden.
The below example configuration customizes settings per path to meet specific needs: /auth prioritizes security with blocking mode enabled, while /data allows larger uploads by increasing the client_max_body_size to 5MB.
In addition to standard prefix paths (/path), you can define locations using the following NGINX regular expression patterns:
-
= /path- exact match -
^~ /path- priority prefix match -
~ pattern- case-sensitive regular expression -
~* pattern- case-insensitive regular expression
Examples:
-
~ ^/api/v[0-9]+/users$ -
~* \.(jpg|png|gif)$ -
= /health -
^~ /static/
Prohibited characters in locations
To prevent NGINX configuration injection, location values must not contain {, }, ;, #, or newline characters.
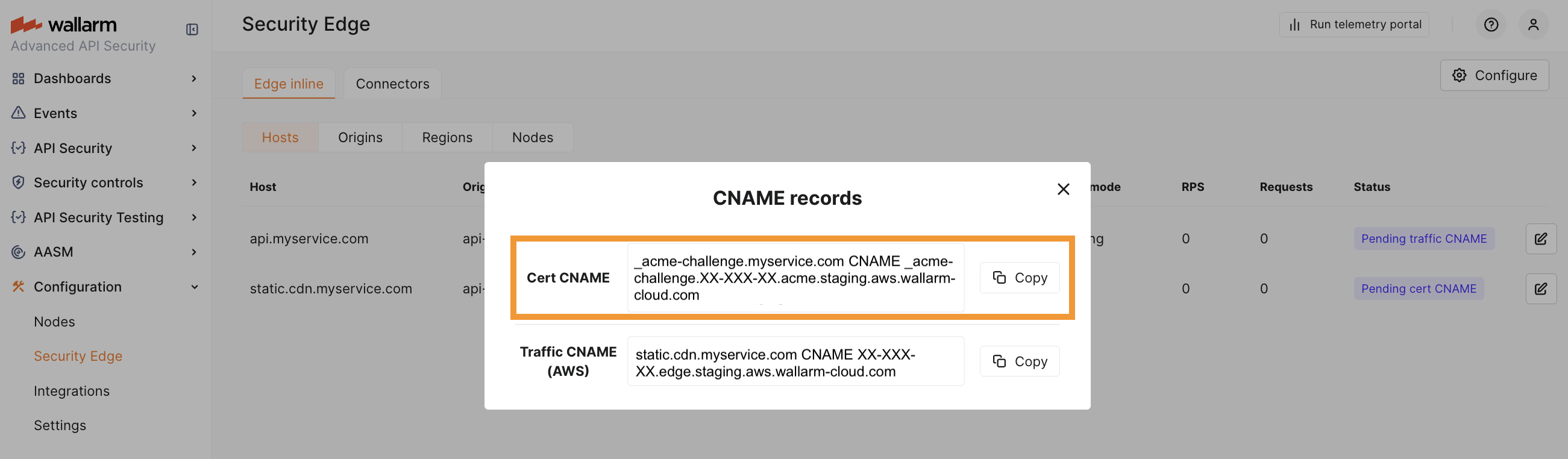
6. Certificate CNAME configuration¶
For domain verification, add the CNAME records provided in the Wallarm Console to your DNS provider's settings for each DNS zone. These records are required for Wallarm to verify domain ownership and issue certificates.
Do not remove the certificate CNAME
The certificate CNAME record must stay in your DNS settings. It is needed for further deployment configuration updates and certificate renewal.
DNS changes can take up to 24 hours to propagate. Wallarm starts the Edge Node deployment once the CNAME records are verified (if needed).
7. Routing traffic to the Edge Node¶
To send client requests through the Edge Node, update your DNS records based on the type of domain you protect.
CNAME record¶
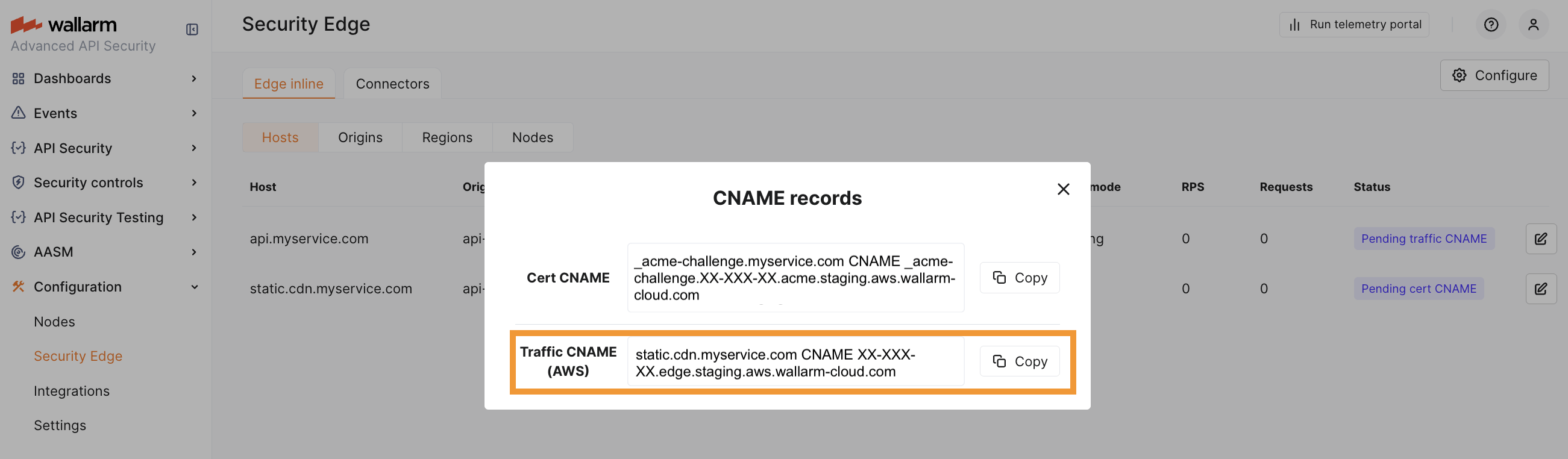
If your protected host is a third-level (or higher-level) domain (e.g., api.example.com), you need to specify the CNAME record pointing to the Wallarm‑proided FQDN in your DNS zone.
Once the certificate CNAME is verified, a Traffic CNAME is available for each host. If no certificate is issued, the CNAME is available immediately after the configuration is complete.
-
Single cloud deployment: use the Traffic CNAME for the selected cloud provider.
-
Multi-cloud deployment: use the Traffic CNAME (Global) to automatically distribute traffic across all selected regions and providers.
Per-provider CNAMEs are also available if you need to enforce routing to a specific provider - for example, to test latency or performance across providers.
DNS changes can take up to 24 hours to propagate. Once propagated, Wallarm will proxy all traffic to the configured origins.
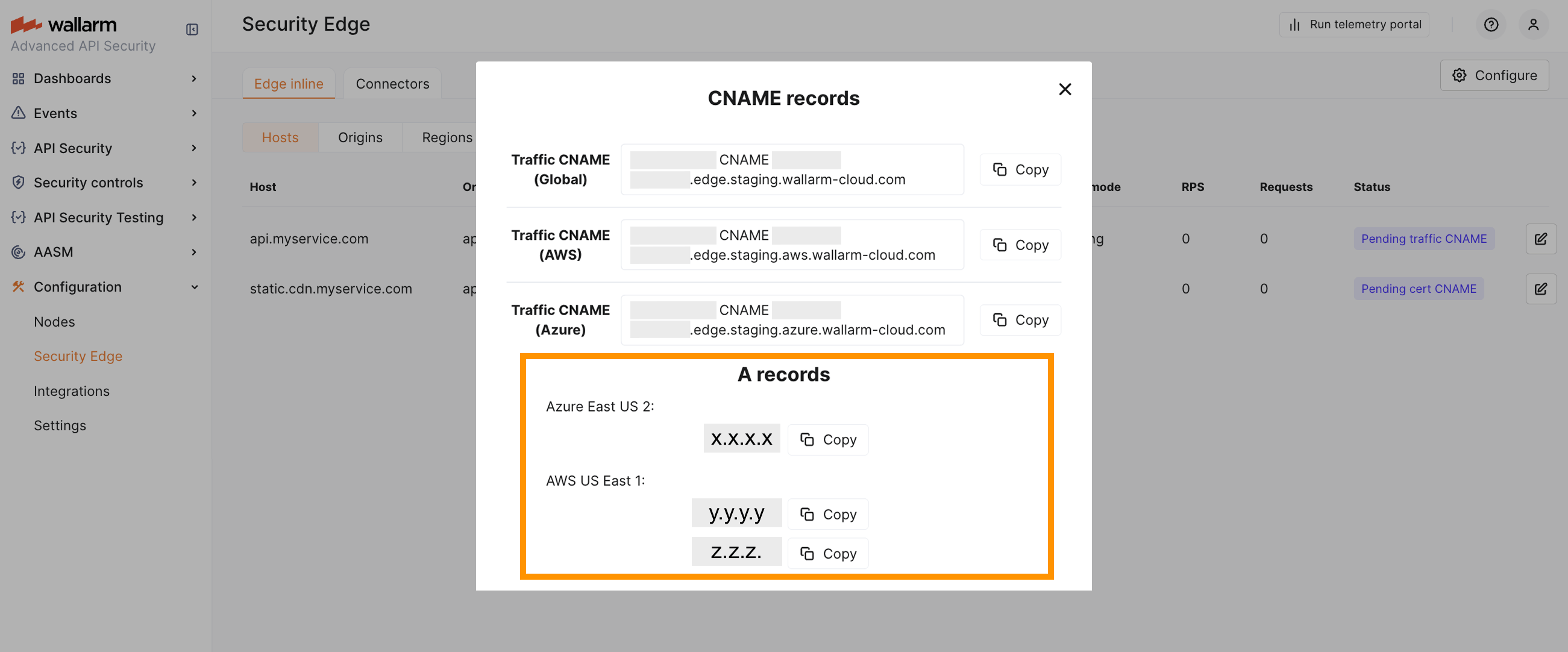
A records¶
If your protected host is an apex domain (e.g., example.com), a CNAME cannot be used. In this case, the DNS setup must use A records, which are returned once the deployment becomes Active.
Traffic routing in this case is managed by your DNS provider. By default, most DNS providers use round-robin logic, but some may support latency-based routing as well.