Deploying Wallarm as a Connector¶
API deployment can be done in various ways, including utilizing external tools such as Azion Edge, Akamai Edge, MuleSoft, Apigee, and CloudFront. If you are looking for a way to secure these APIs with Wallarm, we offer a solution in the form of "connectors" specifically designed for such cases.
How it works¶
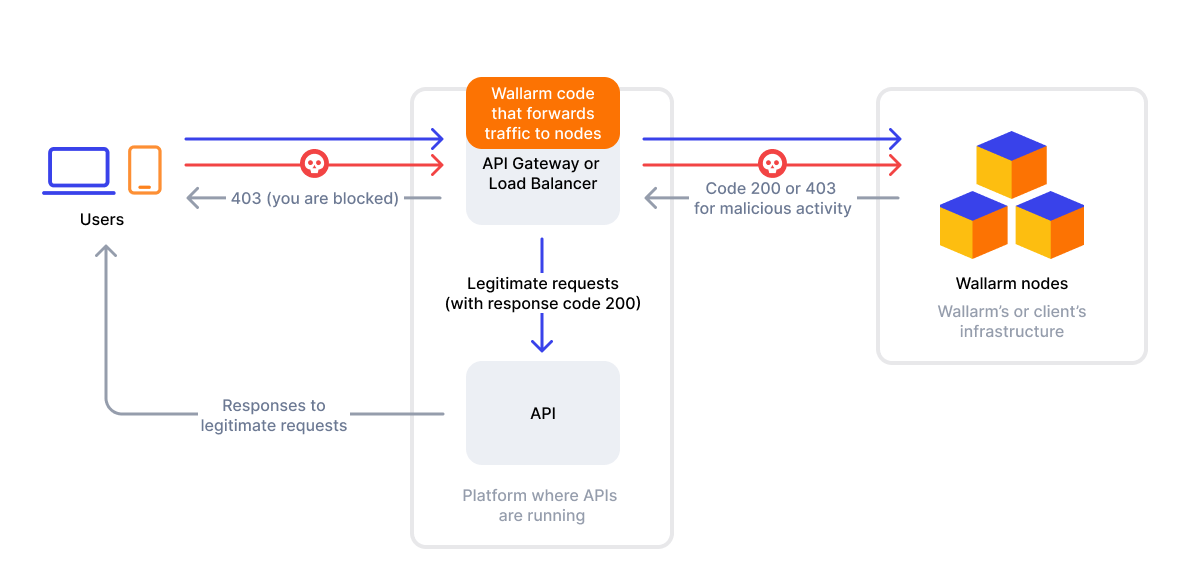
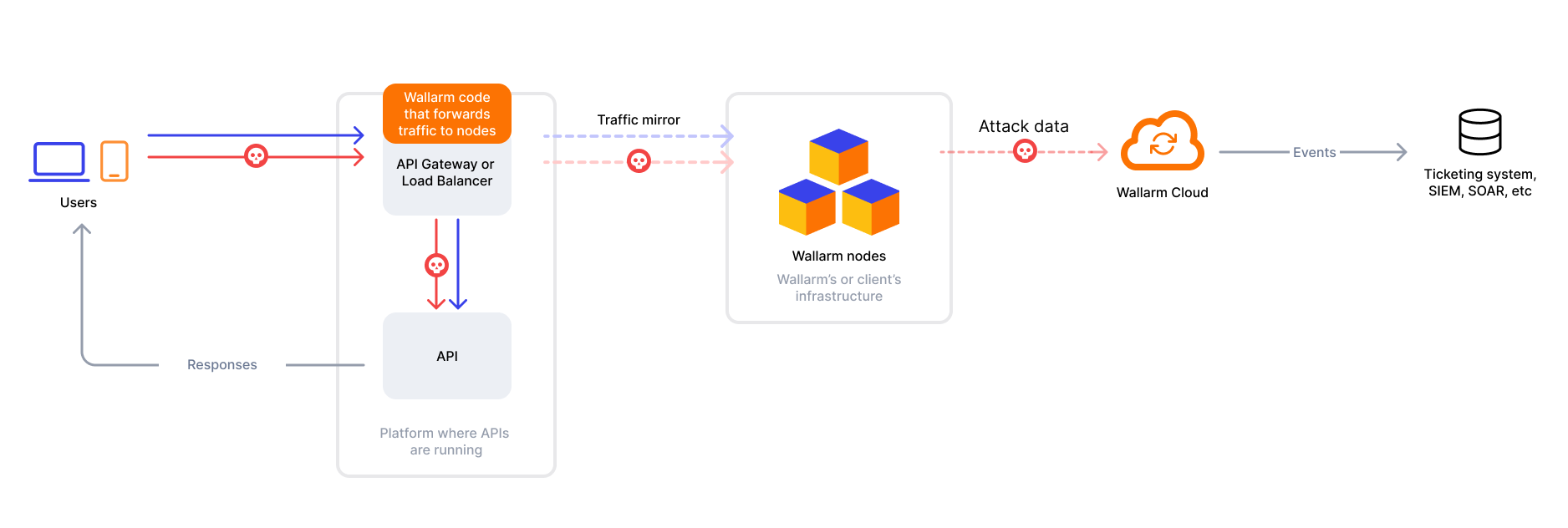
Wallarm's connector solution integrates with third-party platforms, such as API gateways or edge platforms, to filter and analyze traffic. The solution operates with two main components:
-
The Wallarm node, hosted either by Wallarm or the client, performs traffic analysis and security checks.
-
A Wallarm-provided code bundle or policy which is injected into the third-party platform to route traffic for analysis to the Wallarm node.
With connectors, traffic can be analyzed either in-line or out-of-band:
If Wallarm is configured to block malicious activity:
Supported platforms¶
Wallarm offers connectors for the following platforms:
| Connector | Supported traffic flow mode | Connector hosting |
|---|---|---|
| MuleSoft | In-line | Security Edge, self-hosted |
| Apigee | In-line | Self-hosted |
| Akamai EdgeWorkers | In-line | Self-hosted |
| Azion Edge | In-line | Self-hosted |
| Amazon CloudFront | In-line, out-of-band | Security Edge, self-hosted |
| Cloudflare | In-line, out-of-band | Security Edge, self-hosted |
| Kong Ingress Controller | In-line | Self-hosted |
| Istio Ingress | Out-of-band | Self-hosted |
| Broadcom Layer7 API Gateways | In-line | Self-hosted |
| Fastly | In-line, out-of-band | Security Edge, self-hosted |
| IBM DataPower | In-line | Security Edge, self-hosted |
If you couldn't find the connector you are looking for, please feel free to contact our Sales team to discuss your requirements and explore potential solutions.