Wallarm Connector for MuleSoft¶
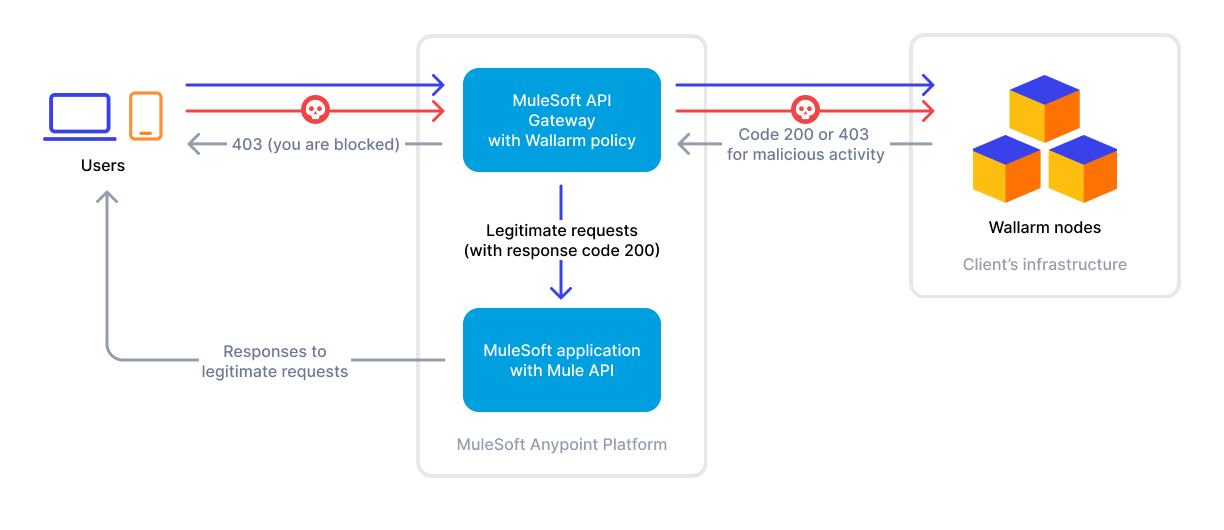
MuleSoft is an integration platform that enables seamless connectivity and data integration between services with an API gateway serving as the entry point for client applications to access APIs. Wallarm can act as a connector to secure APIs running on MuleSoft.
To use Wallarm as a connector for MuleSoft, you need to deploy the Wallarm node externally and apply the Wallarm-provided policy in MuleSoft to route traffic to the Wallarm node for analysis.
The Wallarm connector for MuleSoft supports only in-line traffic analysis:
Use cases¶
Among all supported Wallarm deployment options, this solution is the recommended one for securing APIs deployed on the MuleSoft Enterprise Edition platform with only one policy.
Limitations¶
-
Rate limiting by the Wallarm rule is not supported.
-
Multitenancy is not supported yet.
Requirements¶
To proceed with the deployment, ensure that you meet the following requirements:
-
Understanding of the Mulesoft platform.
-
Docker installed and running on your host system.
-
You have been assigned the Mulesoft Exchange contributor's role, enabling you to upload artifacts to your organization's Mulesoft Anypoint Platform account.
-
Your Mulesoft Exchange credentials (username and password) are specified in the
<MAVEN_DIRECTORY>/conf/settings.xmlfile. -
Your application and API are linked and running on Mulesoft.
-
Access to the account with the Administrator role in Wallarm Console for the US Cloud or EU Cloud.
Deployment¶
1. Deploy a Wallarm node¶
The Wallarm node is a core component of the Wallarm platform that you need to deploy. It inspects incoming traffic, detects malicious activities, and can be configured to mitigate threats.
You can deploy it either hosted by Wallarm or in your own infrastructure, depending on the level of control you require.
To deploy a Wallarm-hosted node for the connector, follow the instructions.
Choose an artifact for a self-hosted node deployment and follow the attached instructions:
- All-in-one installer for Linux infrastructures on bare metal or VMs
- Docker image for environments that use containerized deployments
- AWS AMI for AWS infrastructures
- Helm chart for infrastructures utilizing Kubernetes
2. Obtain and upload the Wallarm policy to Mulesoft Exchange¶
To acquire and upload the Wallarm policy to Mulesoft Exchange, follow these steps:
-
Proceed to Wallarm Console → Security Edge → Connectors → Download code bundle and download a code bundle for your platform.
If running a self-hosted node, contact sales@wallarm.com to get the code bundle.
-
Extract the policy archive.
-
Within the
pom.xmlfile, specify the following:- Navigate to Mulesoft Anypoint Platform → Access Management → Business Groups → choose your organization → copy its ID.
- Specify the copied group ID in the
groupIdparameter of thepom.xmlfile:
- Navigate to Mulesoft Anypoint Platform → Access Management → Business Groups → choose your organization → copy its ID.
- Specify the copied group ID in the
groupIdparameter of thepom.xmlfile. - For Mulesoft instances hosted in specific regions, update the
pom.xmlfile to use the corresponding regional URLs. For example, for a European instance of Mulesoft:
<?xml version="1.0" encoding="UTF-8"?> <groupId>BUSINESS_GROUP_ID</groupId> <artifactId>wallarm</artifactId> <properties> <mule.maven.plugin.version>4.1.2</mule.maven.plugin.version> <exchange.url>https://maven.eu1.anypoint.mulesoft.com/api/v1/organizations/${project.groupId}/maven</exchange.url> </properties> <distributionManagement> <repository> <id>anypoint-exchange-v3</id> <name>Anypoint Exchange</name> <url>https://maven.eu1.anypoint.mulesoft.com/api/v3/organizations/${project.groupId}/maven </url> <layout>default</layout> </repository> </distributionManagement> <repositories> <repository> <id>anypoint-exchange-v3</id> <name>Anypoint Exchange</name> <url>https://maven.eu1.anypoint.mulesoft.com/api/v3/maven</url> <layout>default</layout> </repository> </repositories> -
Create the
confdirectory and asettings.xmlfile inside it with the following content:Replace
usernameandpasswordwith your actual credentials:<?xml version="1.0" encoding="UTF-8"?> <settings xmlns="http://maven.apache.org/SETTINGS/1.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/SETTINGS/1.0.0 http://maven.apache.org/xsd/settings-1.0.0.xsd"> <servers> <server> <id>anypoint-exchange-v3</id> <username>myusername</username> <password>mypassword</password> </server> <server> <id>mulesoft-releases-ee</id> <username>myusername</username> <password>mypassword</password> </server> </servers> </settings>Generate and specify your token in the
passwordparameter:<?xml version="1.0" encoding="UTF-8"?> <settings xmlns="http://maven.apache.org/SETTINGS/1.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/SETTINGS/1.0.0 http://maven.apache.org/xsd/settings-1.0.0.xsd"> <servers> <server> <id>anypoint-exchange-v3</id> <username>~~~Token~~~</username> <password>01234567-89ab-cdef-0123-456789abcdef</password> </server> <server> <id>mulesoft-releases-ee</id> <username>~~~Token~~~</username> <password>01234567-89ab-cdef-0123-456789abcdef</password> </server> </servers> </settings> -
Deploy the policy to Mulesoft using the following command:
Your custom policy is now available in your Mulesoft Anypoint Platform Exchange.
3. Attach the Wallarm policy to your API¶
You can attach the Wallarm policy to either all APIs or an individual API.
Attaching the policy to an individual API¶
To secure an individual API with the Wallarm policy, follow these steps:
-
In your Anypoint Platform, navigate to API Manager and select the desired API.
-
Navigate to Policies → Add policy and select the Wallarm policy.
-
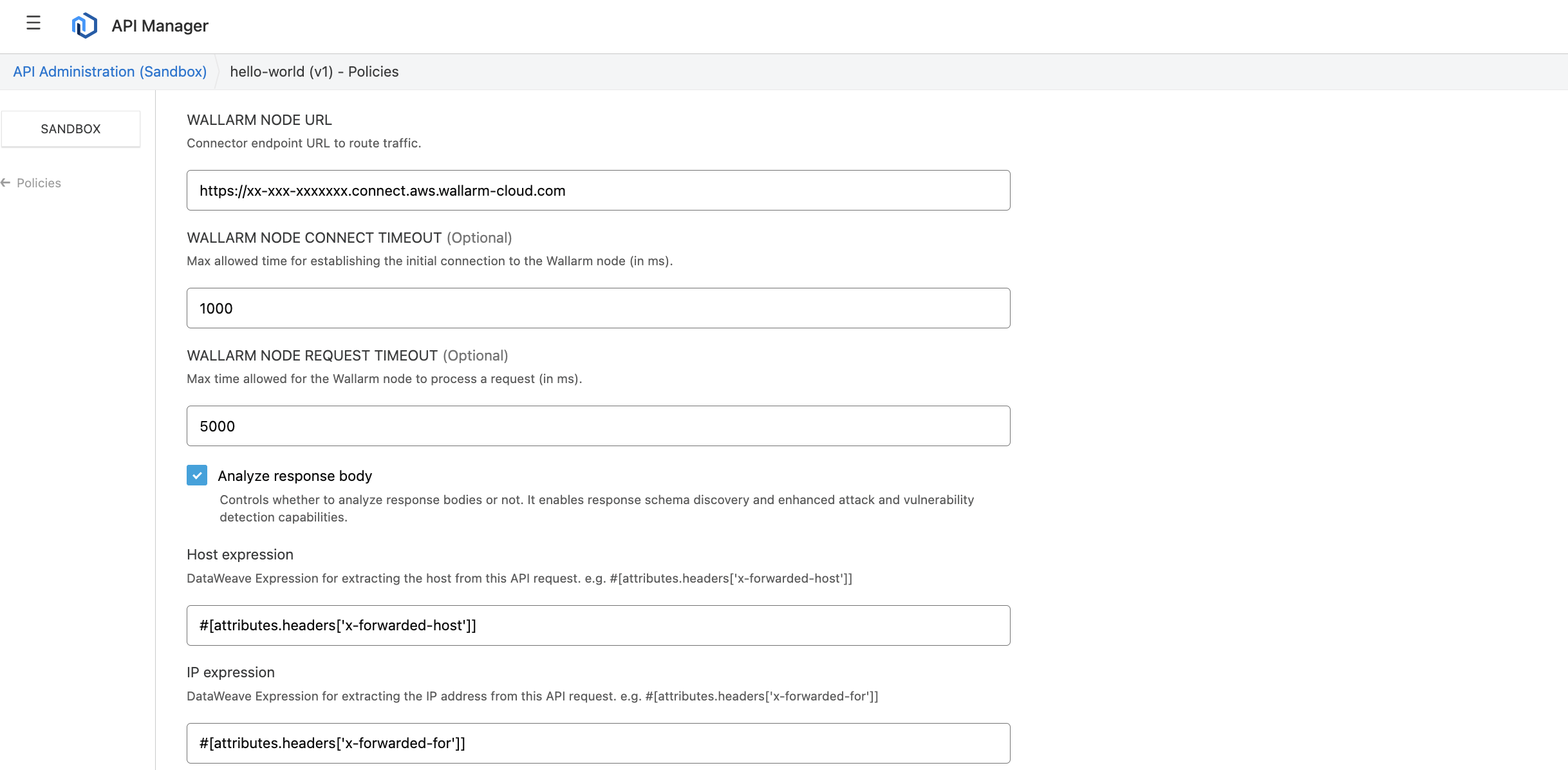
Specify an address of the Wallarm node instance including
http://orhttps://. -
If necessary, modify other parameters.
-
Apply the policy.
Attaching the policy to all APIs¶
To apply the Wallarm policy to all APIs using Mulesoft's Automated policy option, follow these steps:
-
In your Anypoint Platform, navigate to API Manager → Automated Policies.
-
Click Add automated policy and select the Wallarm policy from Exchange.
-
Specify an address of the Wallarm node instance including
http://orhttps://. -
If necessary, modify other parameters.
-
Apply the policy.
Testing¶
To test the functionality of the deployed policy, follow these steps:
-
Send the request with the test Path Traversal attack to your API:
-
Open Wallarm Console → Attacks section in the US Cloud or EU Cloud and make sure the attack is displayed in the list.
If the Wallarm node mode is set to blocking and the traffic flows in-line, the request will also be blocked.
Troubleshooting¶
If the solution does not perform as expected, refer to the logs of your API by accessing Mulesoft Anypoint Platform → Runtime Manager → your application → Logs.
You can also verify whether the policy is applied to the API by navigating to your API in the API Manager and reviewing the policies applied on the Policies tab. For automated policies, you can use the See covered APIs option to view the APIs covered and the reasons for any exclusions.
Upgrading the policy¶
To upgrade the deployed Wallarm policy to a newer version:
-
Download the updated Wallarm policy and upload it to Mulesoft Exchange, as described in Step 2.
-
Once the new version appears in Exchange, go to API Manager → your API → Policies → Wallarm policy → Edit configuration → Advanced options and choose the new policy version from the dropdown.
-
If the new version introduces additional parameters, provide the necessary values.
For example, if upgrading from 2.x to 3.x:
- CLIENT HOST EXPRESSION: use the default value
#[attributes.headers['x-forwarded-host']]unless specific changes are needed. - CLIENT IP EXPRESSION: use the default value
#[attributes.headers['x-forwarded-for']]unless specific changes are needed.
- CLIENT HOST EXPRESSION: use the default value
-
Save changes.
If the Wallarm policy is applied as an automated policy, direct upgrades may not be possible. In such cases, remove the current policy and reapply the new version manually.
Policy upgrades may require a Wallarm node upgrade, especially for major version updates. See the Native Node changelog for the self-hosted Node release notes and upgrade instructions or the Edge connector upgrade procedure. Regular node updates are recommended to avoid deprecation and simplify future upgrades.
Uninstalling the policy¶
To uninstall the Wallarm policy, use the Remove policy option in either the automated policy list or the list of policies applied to an individual API.