The Detect Phase Parameters Description¶
Detecting a vulnerability in the Detect phase
To detect vulnerability in the Detect phase using a server's response, it is necessary either for the response to contain one of the response elements described in the response parameter or for one of the Out-of-Band DNS markers described in the oob parameter to trigger (see the detailed information about out-of-band markers below). Otherwise, it will be assumed that no vulnerabilities were found.
Markers operation logic
If the Detect phase detects a marker from any payload in the server's response, then the attack is successful, meaning that the vulnerability was successfully exploited. To see detailed information about the Detect phase operating with markers, proceed to this link.
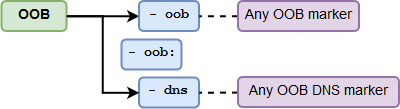
OOB¶
The oob parameter checks the triggering of Out-Of-Band markers by the test request.
Detecting the OOB marker in the server response
If the OOB marker is detected in the server's response, then it will be assumed that the vulnerability was found in the target application.
-
If only
oobis specified, at least one of the Out-of-Band markers triggering is expected. -
You can also specify the exact type of Out-of-Band marker to check for its triggering.
At least one of the
DNS_MARKERmarkers triggering is expected:Available OOB markers
Currently, there is only one Out-of-Band marker available:
DNS_MARKER.
The Out-of-Band attack mechanism
The Out-of-Band (resource load) attack mechanism fully corresponds to its name. When performing the attack, the malefactor forces the server to download malicious content from the external source.
For example, when performing an OOB DNS attack, the malefactor can embed the domain name into the <img> tag as follows: <img src=http://vulnerable.example.com>.
Upon receiving the malicious request, the server resolves the domain name using DNS and addresses the resource controlled by the malefactor.
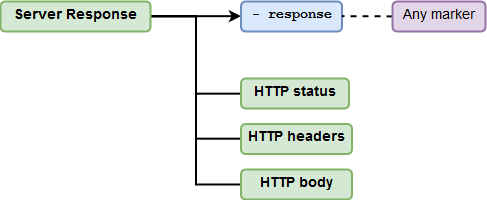
Response¶
This parameter checks whether the necessary elements are present in the server's response to a test request. If at least one of these elements is found, then it is assumed that a vulnerability was detected.
-
The response should contain any marker.
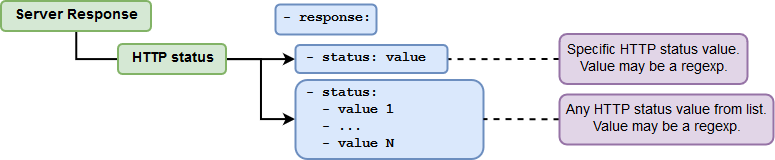
Checking the HTTP Statuses¶
-
The response should contain a certain HTTP status.
Example
- status: 500— the status should have the value of500.- status: '5\d\d'— this regular expression covers all the5xxstatuses. -
The response should contain any of the HTTP statuses from the list.
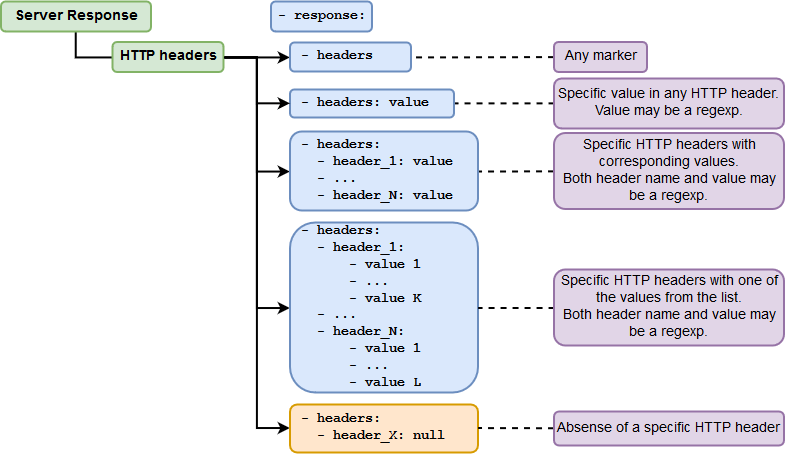
Checking the HTTP headers¶
-
The response headers should contain any marker.
-
The response headers should contain certain data (the
valuecan be a regular expression). -
The certain response header should contain certain data (the
header_#andheader_#_valuecan be regular expressions). -
The certain response headers should contain data from the specified list (the
header_#andheader_#_value_#can be regular expressions). -
The Detect phase can also check whether a certain header is absent from the server's response. To do this, assign
nullto the certain header's value.
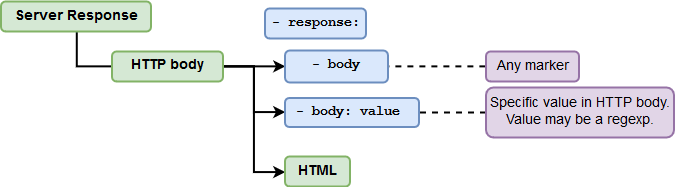
Checking the Body of the HTTP Response¶
-
The body of the response should contain any marker.
-
The body of the response should contain certain data (the
valuecan be a regular expression).
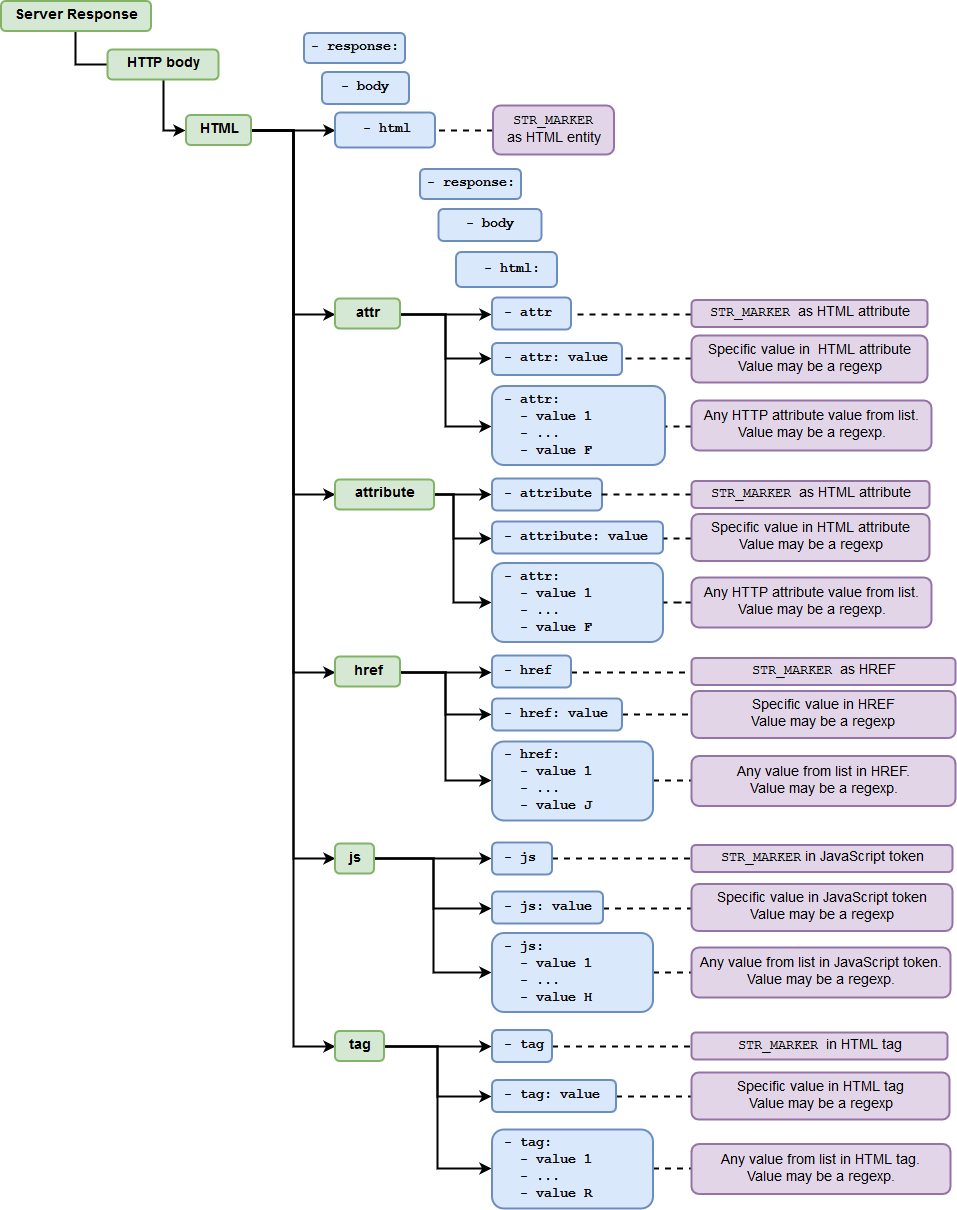
Checking the HTML Markup¶
-
The HTML markup should contain the
STR_MARKER. -
The HTML tag in the response should contain the
STR_MARKER. -
The HTML tag in the response should contain certain data (the
valuecan be a regular expression). -
The HTML tag in the response should contain any data from the specified list (the
value_#can be a regular expression). -
The HTML attribute of the response should contain the
STR_MARKER. -
The HTML attribute should contain certain data (the
valuecan be a regular expression). -
The HTML attribute of the response should contain any of the data from the specified list (the
value_#can be a regular expression):
The shortened version of the attribute parameter
Instead of using the attribute parameter, you can use the shortened version — attr.
-
The HREF link of the response should contain the
STR_MARKER. -
The HREF link of the response should contain certain data (the
valuecan be a regular expression). -
The HREF link of the response should contain any data from the specified list (the
value_#can be a regular expression). -
The JavaScript tokens of the response should contain the
STR_MARKER. -
The JavaScript tokens of the response should contain certain data (the value can be a regular expression).
-
The JavaScript tokens of the response should contain any data from the specified list (the
value_#can be a regular expression).