API Sessions Overview  ¶
¶
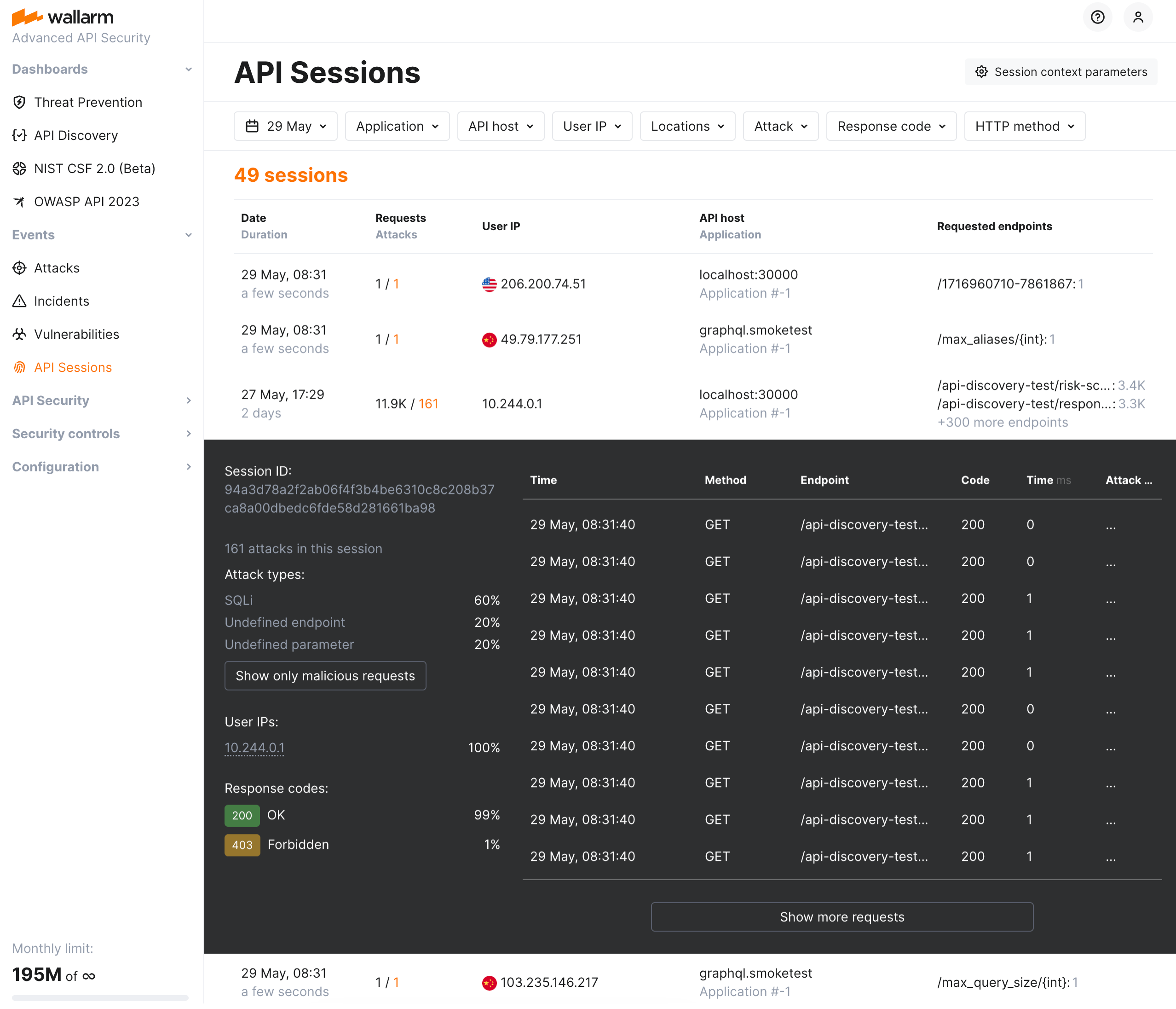
Wallarm's API Sessions provide visibility into user sessions within your traffic. For each session, Wallarm gathers detailed request and related response data, enabling a structured view of session activity. This article gives an overview of API Sessions: issues addressed by it, its purpose and main possibilities.
API Sessions require NGINX Wallarm node 5.1.0 or native Wallarm node 0.8.0. Response parsing - NGINX Wallarm node 5.3.0 or native node 0.12.0.
Addressed issues¶
The primary challenge the API Sessions address is the lack of full context when viewing only individual attacks detected by Wallarm. By capturing the logical sequence of requests and responses within each session, API Sessions provide insights into broader attack patterns and helps identify the areas of business logic impacted by security measures.
As there are API sessions precisely identified by Wallarm, they:
- Make bot detection by API Abuse Prevention more precise.
As you have the API sessions monitored by Wallarm, you can:
-
Track user activity by displaying a list of requests made in a single session with an ability to view the parameters of corresponding responses, so you can identify unusual patterns of behavior or deviations from typical usage.
-
Know which API flow/business logic sequences will be affected before tuning a particular false positive, applying the virtual patch, adding rules, or enabling API Abuse Prevention controls.
-
Inspect endpoints requested in user sessions to quickly assess their protection status, risk level, and any detected issues such as being shadow or zombie.
-
Identify performance issues and bottlenecks to optimize the user experience.
-
Verify API abuse detection accuracy by viewing the entire sequence of requests that were flagged as malicious bot activity along with corresponding responses.
How API Sessions work¶
All traffic that Wallarm node is enabled to secure is organized into sessions and displayed in the API Sessions section.
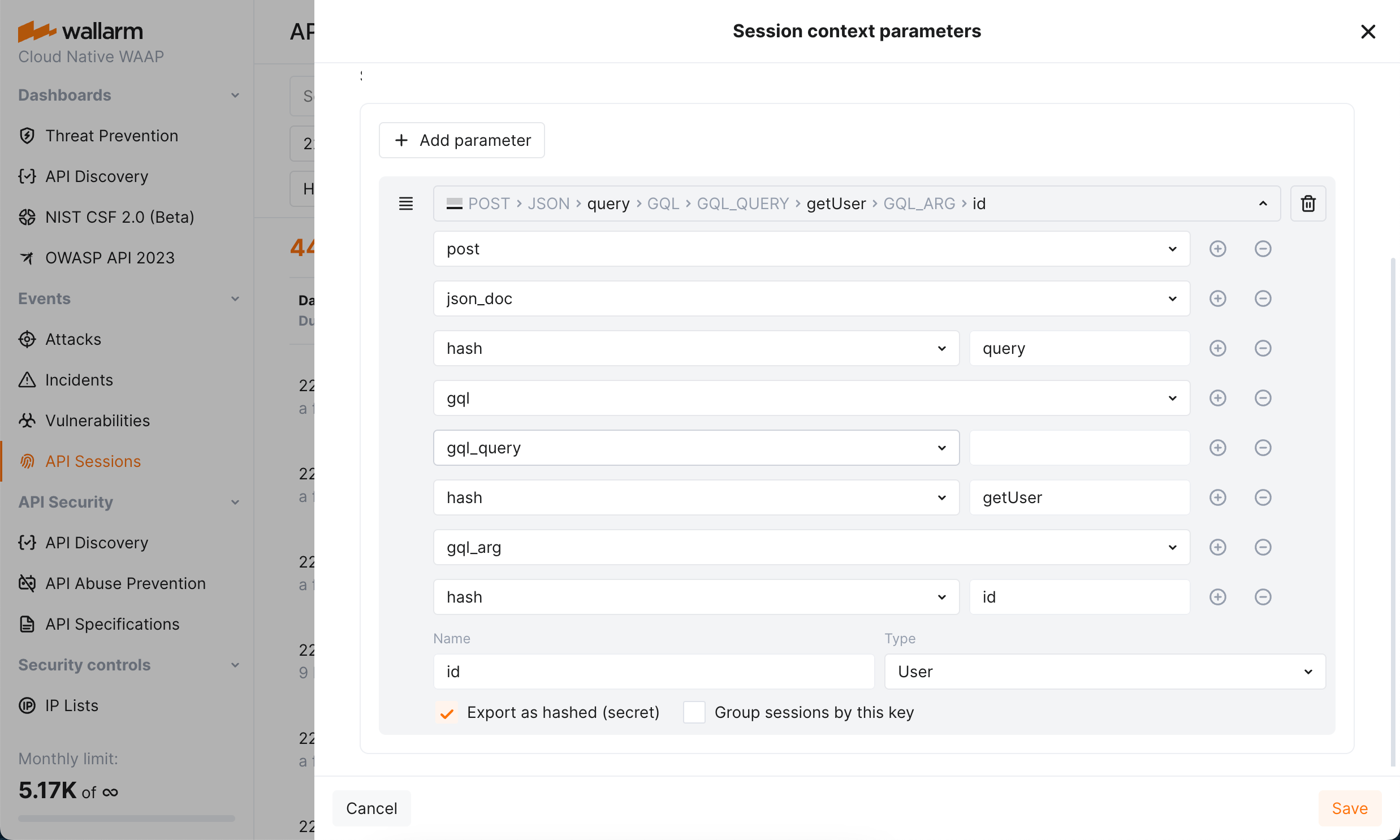
You can customize how requests should be grouped into sessions based on your applications' logic. Also, you can specify which parameters of requests and corresponding responses should be displayed within session to help you to understand the session content: what and in what order the user did (context parameters). See details in API Sessions Setup.
Note that Wallarm stores and displays sessions only for the last week. The older sessions are deleted to provide an optimal performance and resource consumption.
API Sessions and API Abuse Prevention¶
Wallarm's API Abuse Prevention detects malicious bots analyzing the sequences of requests in one or several related sessions, for example, sessions having the same value of the SESSION-ID header and only divided by time/date.
Thus, when you customize how requests are grouped into sessions in accordance with your specific application logic, it affects the work of API Abuse Prevention making both session identification and bot detection more precise.
GraphQL requests in API Sessions¶
API Sessions support working with GraphQL requests and their specific request points, you can configure sessions to extract and display values of GraphQL request parameters.
Requires NGINX Node 5.3.0 or higher or native node 0.12.0.