API Specification Enforcement Overview  ¶
¶
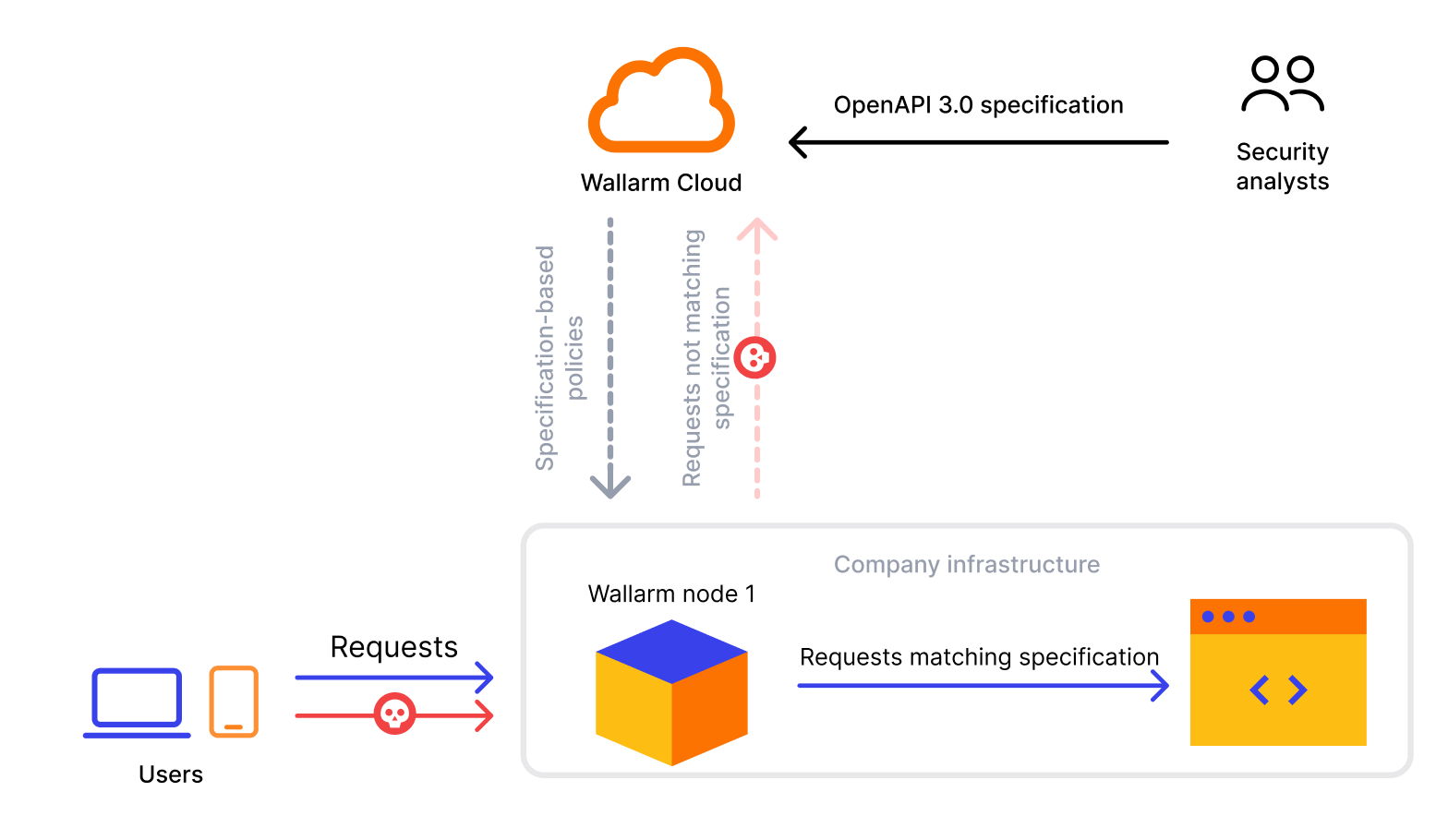
The API Specification Enforcement is designed to apply security policies to your APIs basing on your uploaded specifications. Its primary function is to detect discrepancies between the endpoint descriptions in your specification and the actual requests made to your REST APIs. When such inconsistencies are identified, the system can take predefined actions to address them.
Issues addressed by API Specification Enforcement¶
Your organization may use a number of applications exposed via API and a large number of external IPs, including automation tools, trying to access them. It is a resource consuming task to create restrictions specifically bound to some sources, targets or behaviors.
The API Specification Enforcement allows lowering the security effort by utilizing the positive security model - via specification it defines what is allowed, via the short set of policies it defines how to deal with all the rest.
As you have your API inventory exhaustively described by API specification, you can:
-
Upload this specification to Wallarm.
-
With several clicks, set policies towards requests to API elements, not presented or contradicting the specification.
And thus:
-
Avoid creating of specific restricting rules.
-
Avoid these rules inevitable necessary updates.
-
Never miss attacks for which a direct restricting rule is not configured.
How it works¶
Requests may violate your specification by different positions:
-
Requesting an undefined endpoint - a request targets the endpoint not presented in your specification
-
Requesting endpoint with undefined parameter - a request contains the parameter not presented for this endpoint in your specification
-
Requesting endpoint without required parameter - a request does not contain the parameter or its value that are marked as required in your specification
-
Requesting endpoint with invalid parameter value - a request parameter's value in not in correspondence with its type/format defined by your specification
-
Requesting endpoint without authentication method - a request does not contain the information about the authentication method
-
Requesting endpoint with invalid JSON - a request contains an invalid JSON
The system can perform the following actions in case of found inconsistency:
-
Block - block a request and put in the Attacks section as blocked
Filtration mode
The Wallarm node will block requests only when the blocking filtration mode is enabled for target endpoint - otherwise, Monitor action will be performed.
-
Monitor - mark a request as incorrect, but do not block, put it in the Attacks section as monitored
-
Not tracked - do nothing
Note that several specifications can be used for setting policies. In case when one request falls on two different specifications (the same policy and different actions in different specifications), the following will happen:
-
Block and Block - the request will be blocked and two events will be added to the Attacks section with status
Blockedpointing at the reason of blocking and at the fact that the request violated two different specifications. -
Monitor and Block - the request will be blocked and one event will be added to the Attacks section with status
Blockedexplaining the reason of blocking. -
Monitor and Monitor - the request will not be blocked and two events will be added to the Attacks section with status
Monitoringpointing at the fact that specific policy was violated.
When using API Policy Enforcement, the CPU consumption normally increases by about 20%.
To limit resource consumption, API Specification Enforcement has limits by time (50 ms) and request size (1024 KB) - when exceeding these limits, it stops processing the request and creates the Specification processing overlimit event in the Attacks section, saying that one of these limits was exceeded.
API Specification Enforcement and other protection measures
Note that if API Specification Enforcement stops processing the request, this does not mean it is not processed by other Wallarm protection procedures. Thus, if it is an attack, it will be registered or blocked in accordance with the Wallarm configuration.
To change limits or Wallarm behavior (from monitoring of overlimits to blocking such requests), contact Wallarm Support.
Note that API Specification Enforcement adds its regulation to a usual attack detection performed by the Wallarm node and does not replaces it, so your traffic will be checked both for the absence of the attack signs and for correspondence to your specification.
Setup¶
To start protecting your APIs with API Specification Enforcement, upload your specification, and set policies as described here.