Sensitive Business Flows  ¶
¶
With the sensitive business flow capability, Wallarm's API Discovery can automatically identifies endpoints that are critical to specific business flows and functions, such as authentication, account management, billing, and similar critical capabilities. Learn from this article how to use the sensitive business flow functionality.
Requires NGINX Node 5.2.11 or Native Node 0.10.1 or higher.
Addressed issues¶
The abuse of the sensitive business flows ranks sixth (API6) among OWASP API Top 10 risks. Protecting these sensitive business flows ensures business continuity, prevents leaking of sensitive data, reputation risks, and financial damage.
WIth the sensitive business flows capability, Wallarm highlights health of the business-critical functions and helps to:
-
Regularly monitor and audit endpoints related to sensitive business flows for vulnerabilities or breaches.
-
Prioritize them for development, maintenance, and security efforts.
-
Implement stronger security measures (e.g., encryption, authentication, access controls, and rate limits).
-
Easily produce audit trails and evidence of data protection measures.
Automatic tagging¶
For your convenience, API Discovery tags endpoints as belonging to sensitive business flows automatically - on discovering a new endpoint, it checks whether this endpoint potentially belongs to one or more sensitive business flows:
-
AI/LLM (artificial intelligence/large language models) flows - requests/endpoints/parameters related to the systems that use ML models, neural networks, chatbots or systems that in turn access some paid third-party AI services, such as OpenAI.
-
Acc create (account creation) and Acc mgmt (account management) flows - the key administrative flows relating to your applications.
-
Admin (administrative) flows - requests/endpoints/parameters related to applications' administrative functions and activities. Such requests/endpoints/parameters are usually targeted by attackers in order to access functionality intended for privileged users only (BFLA), escalate privileges and gaining control over the system.
-
Auth (authentication) flows - requests/endpoints/parameters critical to access control, as they verify user identity and manage permissions. As the entry point to the app, they are often the first target for attackers seeking to bypass security, gain unauthorized access, and take over accounts.
-
Billing flows - sensitive due to usage and possible breach of critical personal financial data and susceptible to fraud.
-
SMS GW (SMS gateway) flows - requests/endpoints/parameters sensitive because attackers can exploit them in SMS pumping attacks, flooding them with messages to inflate costs. Since these requests/endpoints/parameters are connected to API gateways and payment systems, this can lead to financial loss and system overload.
Automatic checks are conducted using keywords from the endpoint URL. For example, keywords like payment, subscription, or purchase automatically associate the endpoint with the Billing flow, while keywords such as auth, token, or login link it to the Authentication flow. If matches are detected, the endpoint is automatically assigned to the appropriate flow.
The automatic tagging discovers most of the sensitive business flows. However, it is also possible to manually adjust the list of assigned business flows as described in the section below.
Tagging endpoints manually¶
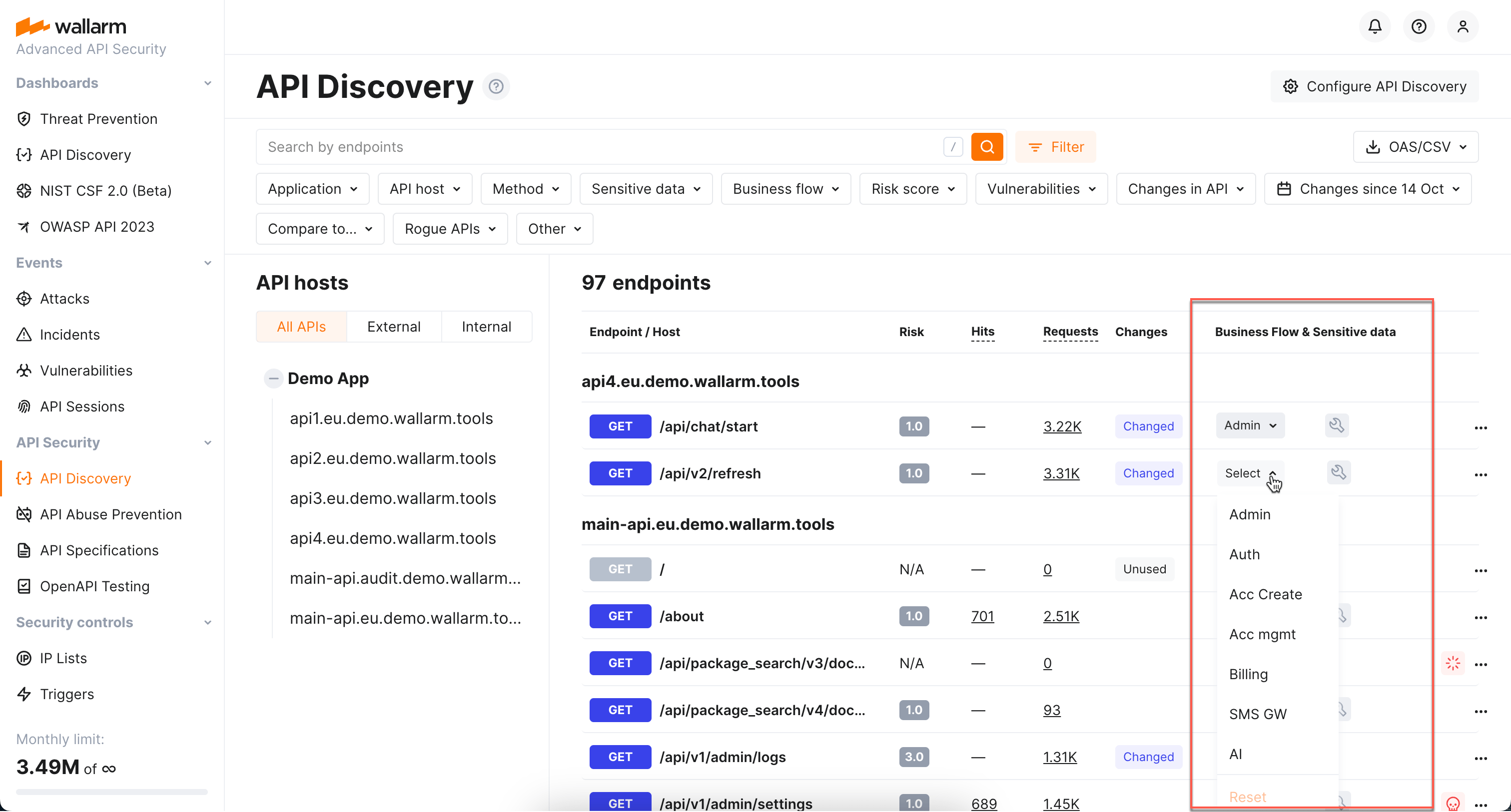
To adjust the results of automatic tagging, you can manually edit the list of sensitive business flow the endpoint belongs to. You can also manually tag endpoints that do not directly fall under the keyword list.
To edit the list of flows the endpoint belongs to, in Wallarm Console, go to API Discovery, then for your endpoint, in the Business flow & sensitive data, select one or several flows from the list.
You can do the same in the endpoint details.
Business flows in Sessions¶
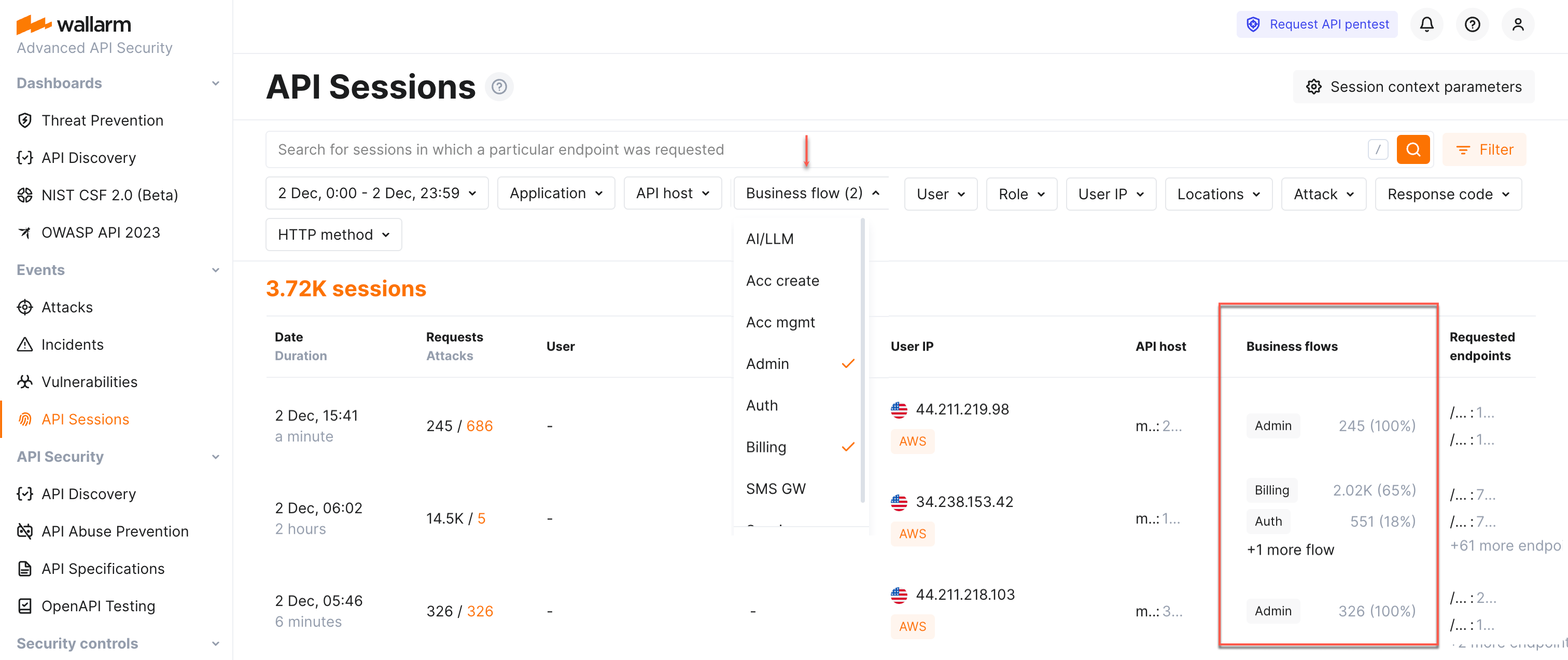
Wallarm's API Sessions are used to provide you with the full sequence of user activities and thus give more visibility into the logic of malicious actors. If session's requests affect the endpoints that in API Discovery were tagged as important for some sensitive business flows, such session will be automatically tagged as affecting this business flow as well.
Once sessions are assigned with the sensitive business flow tags, it becomes possible to filter them by a specific business flow which makes it easier to select the sessions that are most important to analyze.
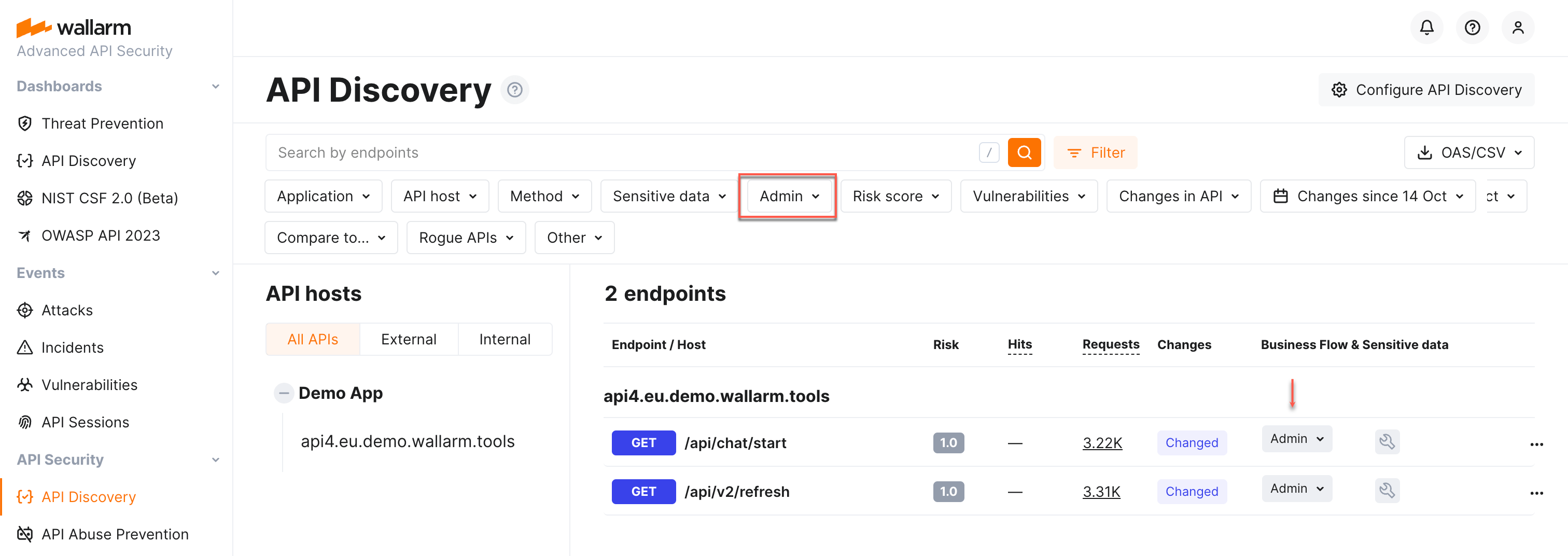
Filtering by business flow¶
Once endpoints are assigned with the sensitive business flow tags, it becomes possible to filter all discovered endpoint by a specific business flow (the Business flow filter) which makes it easier on protecting the most critical business capabilities.