Upgrading Wallarm NGINX modules¶
These instructions describe the steps to upgrade the Wallarm NGINX modules 4.x installed from the individual packages to version 6.x. These are the modules installed in accordance with one of the following instructions:
-
Individual packages for NGINX stable
-
Individual packages for NGINX Plus
-
Individual packages for distribution-provided NGINX
Upgrading with all-in-one installer
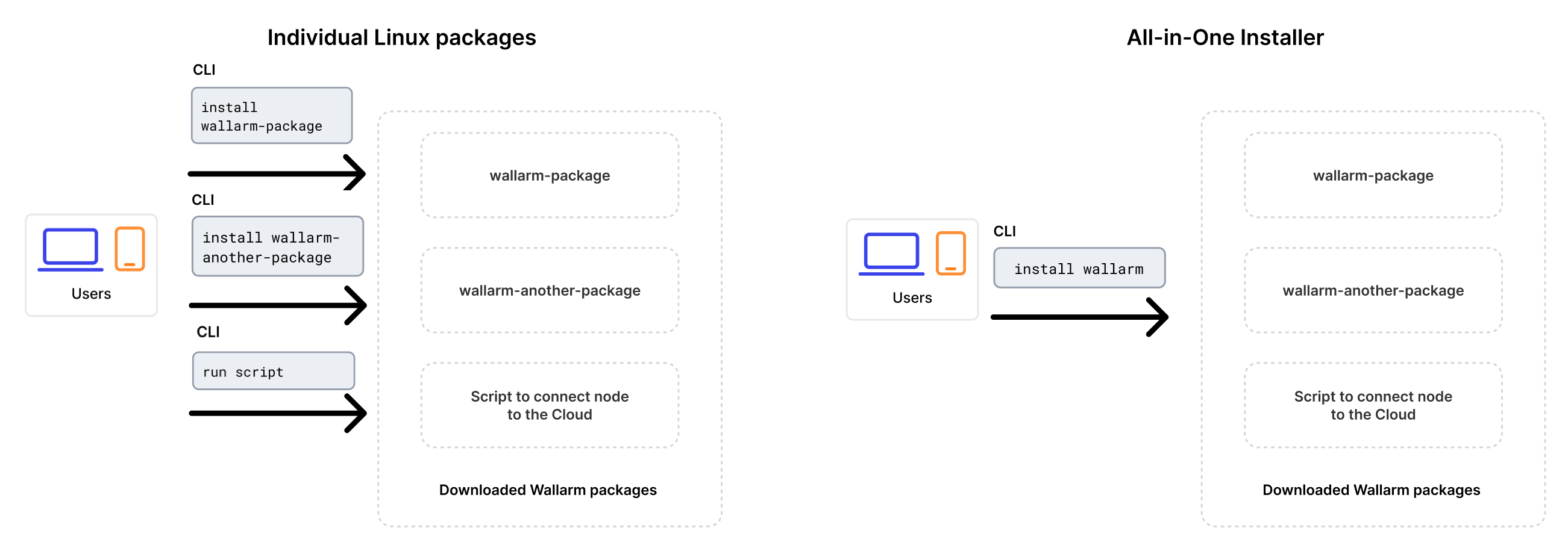
Since version 4.10, upgrading is performed using Wallarm's all-in-one installer as the individual Linux packages have been deprecated. This method simplifies the upgrade process and ongoing deployment maintenance compared to the previous approach.
The installer automatically performs the following actions:
- Checking your OS and NGINX version.
- Adding Wallarm repositories for the detected OS and NGINX version.
- Installing Wallarm packages from these repositories.
- Connecting the installed Wallarm module to your NGINX.
- Connecting the filtering node to Wallarm Cloud using the provided token.
To upgrade the end‑of‑life node (3.6 or lower), please use the different instructions.
Requirements¶
-
Access to the account with the Administrator role in Wallarm Console for the US Cloud or EU Cloud.
-
Access to
https://meganode.wallarm.comto download all-in-one Wallarm installer. Ensure the access is not blocked by a firewall. -
Access to
https://us1.api.wallarm.comfor working with US Wallarm Cloud or tohttps://api.wallarm.comfor working with EU Wallarm Cloud. If access can be configured only via the proxy server, then use the instructions. -
Executing all commands as a superuser (e.g.
root). -
Access to the IP addresses below for downloading updates to attack detection rules and API specifications, as well as retrieving precise IPs for your allowlisted, denylisted, or graylisted countries, regions, or data centers.
Upgrade procedure¶
-
If filtering node and postanalytics modules are installed on the same server, then follow the instructions below to upgrade all.
You will need to run a node of the newer version using all-in-one installer on a clean machine, test that it works well and stop the previous one and configure traffic to flow through the new machine instead of the previous one.
-
If filtering node and postanalytics modules are installed on different servers, first upgrade the postanalytics module and then the filtering module following these instructions.
Step 1: Prepare clean machine¶
When upgrading modules with all-in-one installer, you cannot upgrade an old package installation - instead you need to use a clean machine. Thus, as step 1, prepare a machine with one of the supported OS:
-
Debian 10, 11 and 12.x
-
Ubuntu LTS 18.04, 20.04, 22.04
-
CentOS 7, 8 Stream, 9 Stream
-
Alma/Rocky Linux 9
-
RHEL 8.x
-
RHEL 9.x
-
Oracle Linux 8.x
-
Oracle Linux 9.x
-
Redox
-
SuSe Linux
-
Others (the list is constantly widening, contact Wallarm support team to check if your OS is in the list)
Using new clean machine will lead to that at some moment you will have both old and new node, which is good: you can test the new one working properly without stopping the old one.
Step 2: Install latest NGINX and dependencies¶
Install the latest NGINX version of:
-
NGINX
stable(the latest supported version is v1.28.0) - see how to install it in the NGINX documentation. -
NGINX Mainline (the latest supported version is v1.27.5) - see how to install it in the NGINX documentation.
-
NGINX Plus (the latest supported version is NGINX Plus R33) - see how to install it in the NGINX documentation.
-
Distribution-Provided NGINX - to install, use the following commands:
Step 3: Prepare Wallarm token¶
To install node, you will need a Wallarm token of the appropriate type. To prepare a token:
Step 4: Download all-in-one Wallarm installer¶
Wallarm suggests all-in-one installations for the following processors:
-
x86_64
-
ARM64 (beta)
To download all-in-one Wallarm installation script, execute the command:
Step 5: Run all-in-one Wallarm installer¶
Filtering node and postanalytics on the same server¶
-
Run downloaded script:
# If using the x86_64 version: sudo env WALLARM_LABELS='group=<GROUP>' sh wallarm-6.2.1.x86_64-glibc.sh # If using the ARM64 version: sudo env WALLARM_LABELS='group=<GROUP>' sh wallarm-6.2.1.aarch64-glibc.shThe
WALLARM_LABELSvariable sets group into which the node will be added (used for logical grouping of nodes in the Wallarm Console UI). -
Enter Wallarm token.
Filtering node and postanalytics on different servers¶
Sequence of steps to upgrade the filtering node and postanalytics modules
If the filtering node and postanalytics modules are installed on different servers, then it is required to upgrade the postanalytics packages before updating the filtering node packages.
-
Upgrade postanalytics module following these instructions.
-
Upgrade filtering node:
# If using the x86_64 version: sudo env WALLARM_LABELS='group=<GROUP>' sh wallarm-6.2.1.x86_64-glibc.sh filtering # If using the ARM64 version: sudo env WALLARM_LABELS='group=<GROUP>' sh wallarm-6.2.1.aarch64-glibc.sh filteringThe
WALLARM_LABELSvariable sets group into which the node will be added (used for logical grouping of nodes in the Wallarm Console UI).
Step 6: Transfer NGINX and postanalytics configuration from old node machine to new¶
Migrate the node-related NGINX and postanalytics configurations from the old machine to the new one by copying the necessary directives or files:
-
/etc/nginx/conf.d/default.confor/etc/nginx/nginx.confwith NGINX settings for thehttplevelIf the filtering and postanalytics nodes are on different servers, in the
httpblock of/etc/nginx/nginx.confon the filtering node machine, renamewallarm_tarantool_upstreamtowallarm_wstore_upstream. -
/etc/nginx/sites-available/defaultwith NGINX and Wallarm settings for traffic routing -
/etc/nginx/conf.d/wallarm-status.conf→ copy to/etc/nginx/wallarm-status.confon the new machineDetailed description is available within the link.
-
/etc/wallarm/node.yaml→ copy to/opt/wallarm/etc/wallarm/node.yamlon the new machineIf using a custom host and port on a separate postanalytics server, rename the
tarantoolsection towstorein the copied file on the postanalytics node machine.
Step 7: Restart NGINX¶
Restart NGINX using the following command:
Step 8: Test Wallarm node operation¶
To test the new node operation:
-
Send the request with test SQLI and XSS attacks to the protected resource address:
-
Open the Wallarm Console → Attacks section in the US Cloud or EU Cloud and ensure attacks are displayed in the list.
-
As soon as your Cloud stored data (rules, IP lists) is synchronized to the new node, perform some test attacks to make sure your rules work as expected.
Step 9: Configure sending traffic to Wallarm node¶
Update targets of your load balancer to send traffic to the Wallarm instance. For details, please refer to the documentation on your load balancer.
Before full redirecting of the traffic to the new node, it is recommended to first redirect it partially and check that the new node behaves as expected.
Step 10: Remove old node¶
-
Delete old node in Wallarm Console → Nodes by selecting your node and clicking Delete.
-
Confirm the action.
When the node is deleted from Cloud, it will stop filtration of requests to your applications. Deleting the filtering node cannot be undone. The node will be deleted from the list of nodes permanently.
-
Delete machine with the old node or just clean it from Wallarm node components: