Cloud-Native WAAP¶
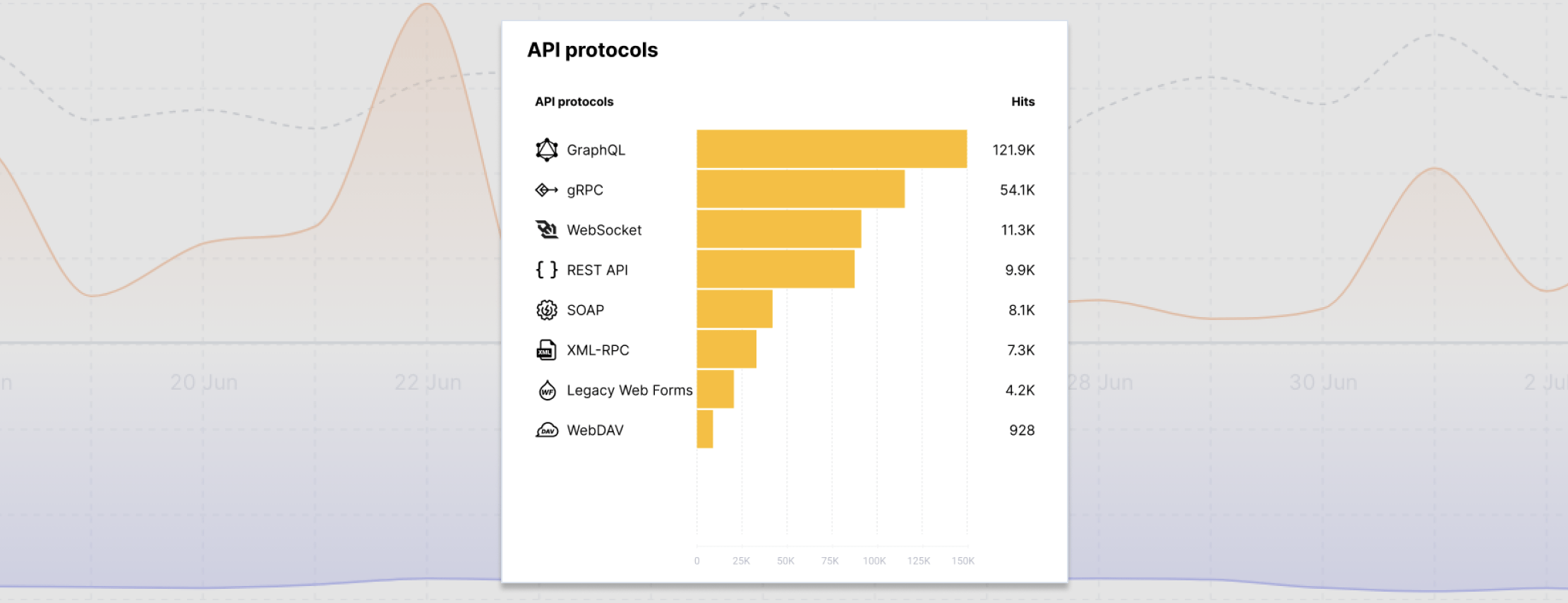
Wallarm Cloud-Native WAAP (Web Application & API Protection) provides advanced protection for applications and APIs in any customer environment. Wallarm's WAAP supports multiple API protocols, such as REST, SOAP, GraphQL, and others, and implies a deep packet inspection to fully cover OWASP Top 10 and more. WAAP provides high accuracy in detecting various threats, including 0-days, and a low number of false positives. This allows you to quickly and effectively protect your infrastructure.
General principles¶
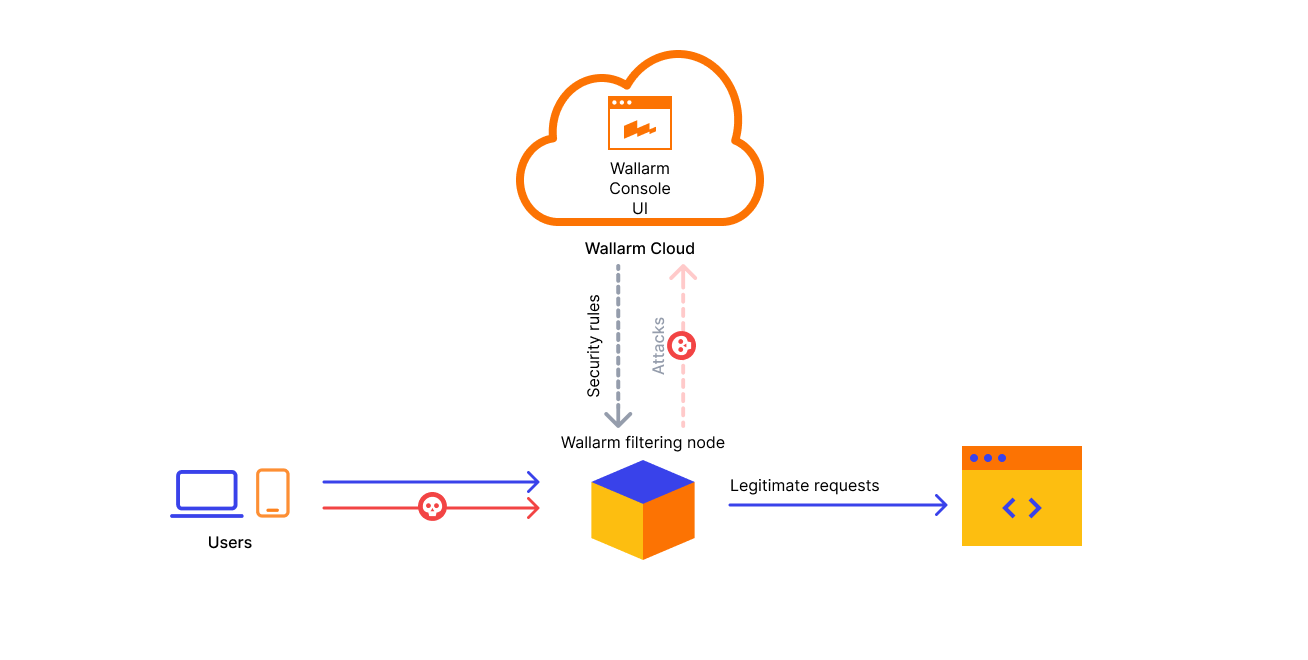
Traffic is handled by two components: Wallarm filtering nodes and Wallarm Cloud. Wallarm filtering nodes are deployed in the customer's infrastructure and are responsible for analyzing traffic and blocking attacks. The collected attack statistics are sent to Wallarm Cloud for statistical analysis and event processing. Wallarm Cloud is also responsible for centralized management and integration with other security tools.
Wallarm supports various deployment options, including public cloud, on-premises, full SaaS deployment, and integrating with Kubernetes, Gateway APIs, Security Edges, etc. Wallarm filtering nodes can be deployed either in-line or out-of-band, depending on your needs and infrastructure. Flexible security policy configuration options allow you to quickly switch between monitoring and blocking modes, eliminating fear of blocking legitimate traffic.
Protection measures¶
Wallarm WAAP provides a wide range of security measures to protect your applications from all types of threats, including but not limited to:
-
Up-to-date stamps against XSS, SQLi, RCE, etc.
-
Virtual patching
-
Custom detectors creating
-
Rate limiting
-
Malicious IPs feeds
Additional capabilities¶
In addition to protecting applications, Wallarm Cloud Native WAAP provides capabilities to identify vulnerabilities (passive detection) before malefactors attack them.
Flexible reporting capabilities and integration with other applications allow you to quickly learn about emerging threats and respond to them on time.
Advanced API protection and analysis capabilities can easily be added as needed.