Wallarm Platform Overview¶
In today's digital world, APIs face growing threats, especially with the rise of AI. Traditional security can overlook API vulnerabilities or be difficult to deploy. With Wallarm, you get a single platform for API protection and inventory observability across cloud-native and on-prem environments.
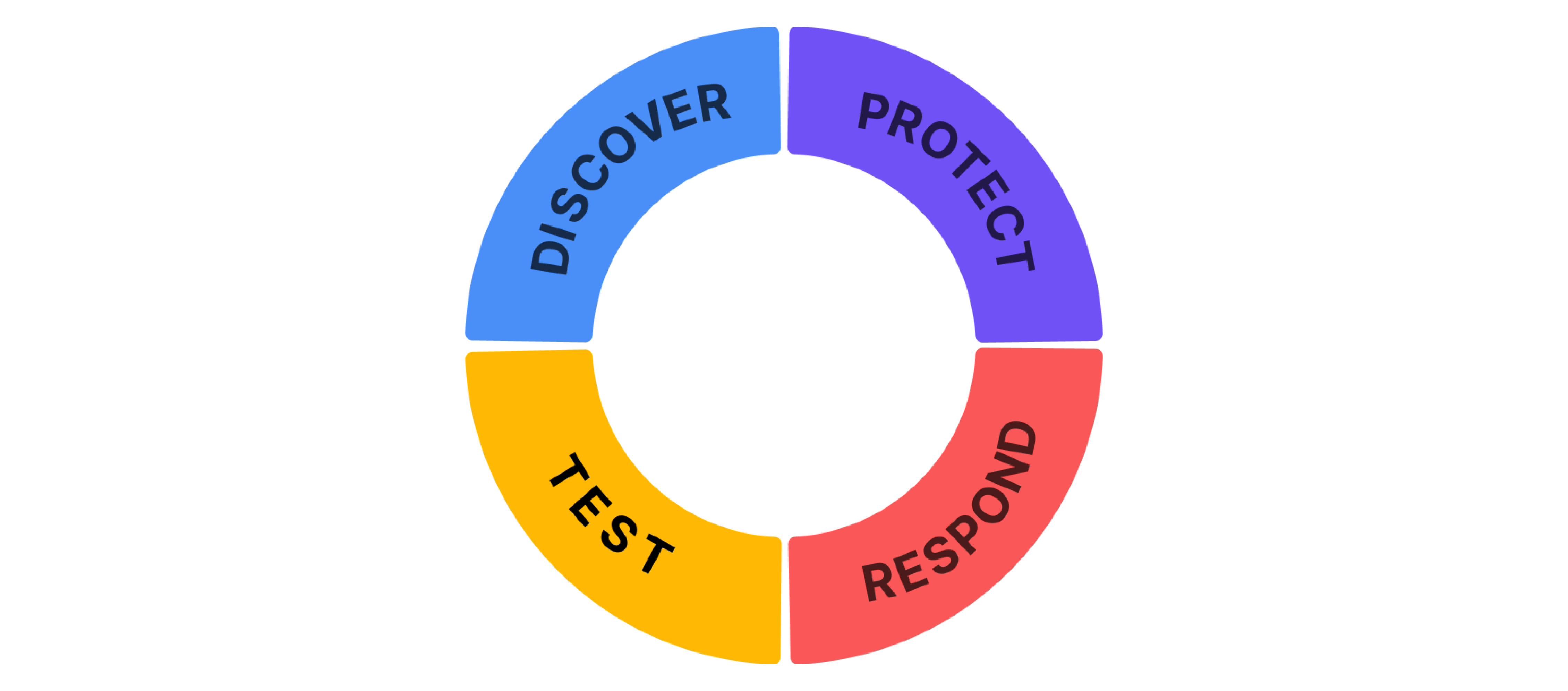
Enterprises prefer Wallarm for its enhanced API security, easy deployment, and value. It combines API discovery, risk management, real-time protection, and testing with advanced API security capabilities.
Discover¶
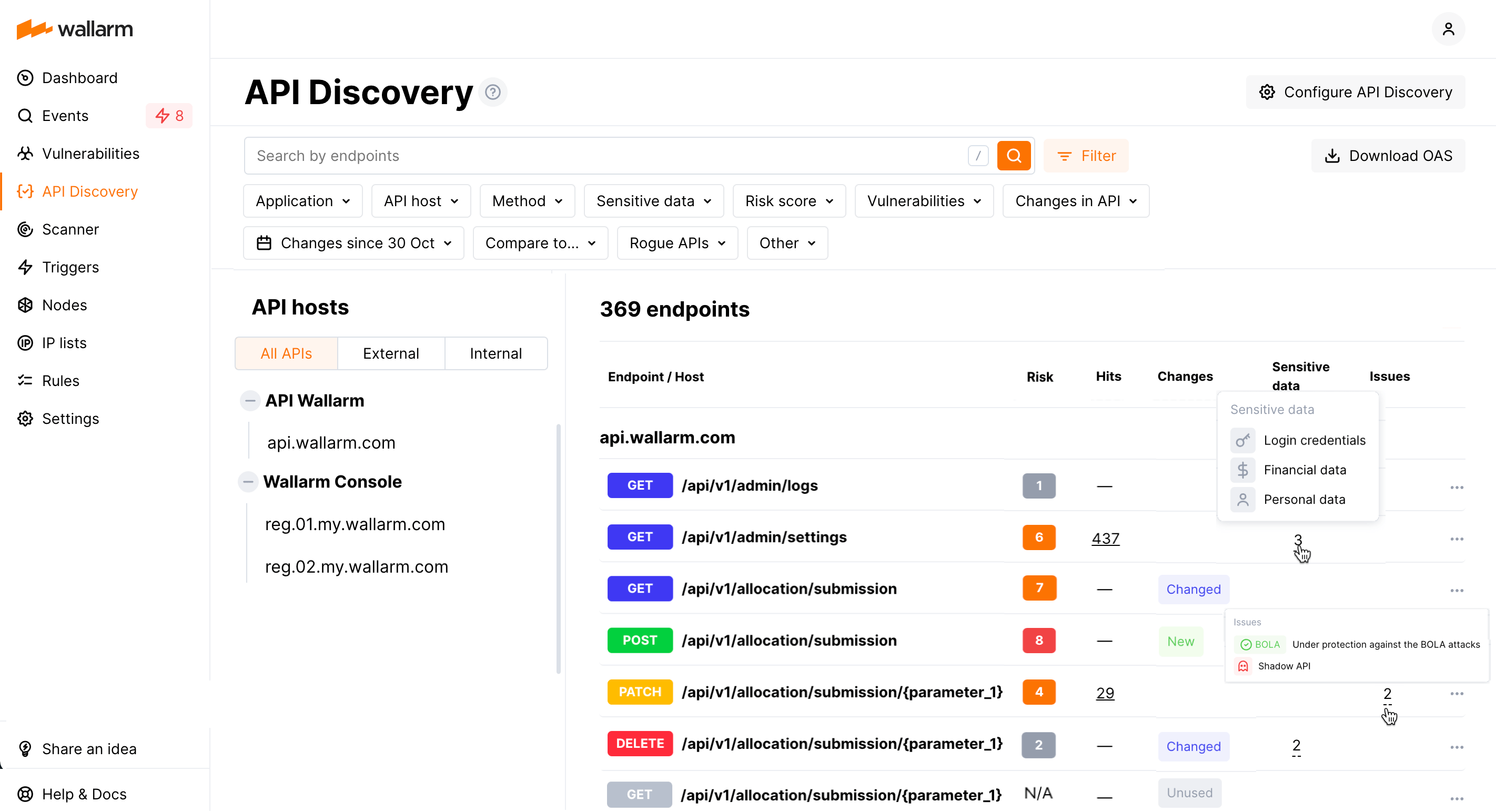
You need to know it to protect it. Wallarm offers comprehensive API discovery capabilities to identify APIs in your environment and evaluate their security risks. Here is what Wallarm's API discovery does:
-
Detects your API endpoints and their parameters, and continually updates the API view through consistent traffic analysis.
-
Identifies rogue endpoints, including shadow, orphan, and zombie APIs.
-
Spots endpoints that could expose sensitive data, like PII.
-
Assesses each endpoint for security risks, vulnerabilities, and provides a risk score.
Protect¶
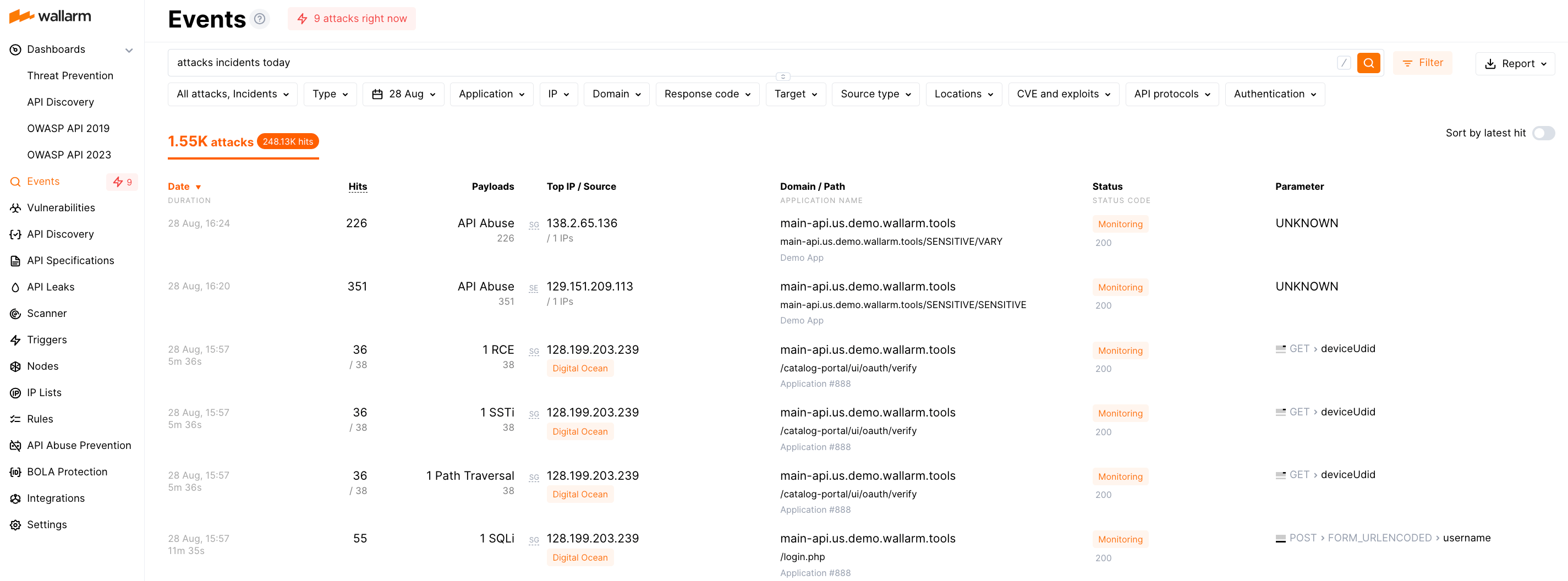
Wallarm extends discovery to deliver real protection by detecting and blocking application and API attacks in traffic. Wallarm’s proprietary detection techniques deliver highly accurate results, including detection of attacks against OWASP Top 10 and OWASP API Top 10 vulnerabilities. Here is how Wallarm ensures protection:
-
Detects attacks both inline and out-of-band.
-
Combats various threats, from web-based to API-specific ones, like code injections, remote code execution, brute force, BOLA, and more.
-
Identifies API specific malicious bot abuse.
-
Counters Layer 7 Denial of Service attacks with customizable rate limiting.
-
Allows users to create custom defenses by setting their own threat definitions, complementing the built-in measures.
-
Maps attacks with your system's vulnerabilities to highlight critical incidents.
-
Detects credential stuffing attempts.
Respond¶
Wallarm gives you the tools to effectively respond to security threats, offering in-depth data, broad integrations, and blocking mechanisms. It first presents detailed information, helping security analysts gauge the threat's nature and severity. You can then tailor responses, act on threats, and send alerts to relevant systems. Here is how Wallarm backs you up:
-
Deep attack inspection, which includes unpacked encoded requests, detailing every aspect of an attack, from headers to the body.
-
Geolocation-based controls to block suspicious traffic sources like VPNs and Tor networks.
-
Attack blocking measures to prevent malicious activities from reaching your APIs.
-
Integrations with the most widely used security, operational, and development tools to create tickets, notifications, and deliver data on detected security threats. Compatible platforms include Slack, Sumo Logic, Splunk, Microsoft Sentinel, and more.
-
Virtual patches for urgent issues highlighted by Wallarm's vulnerability detection.
Test¶
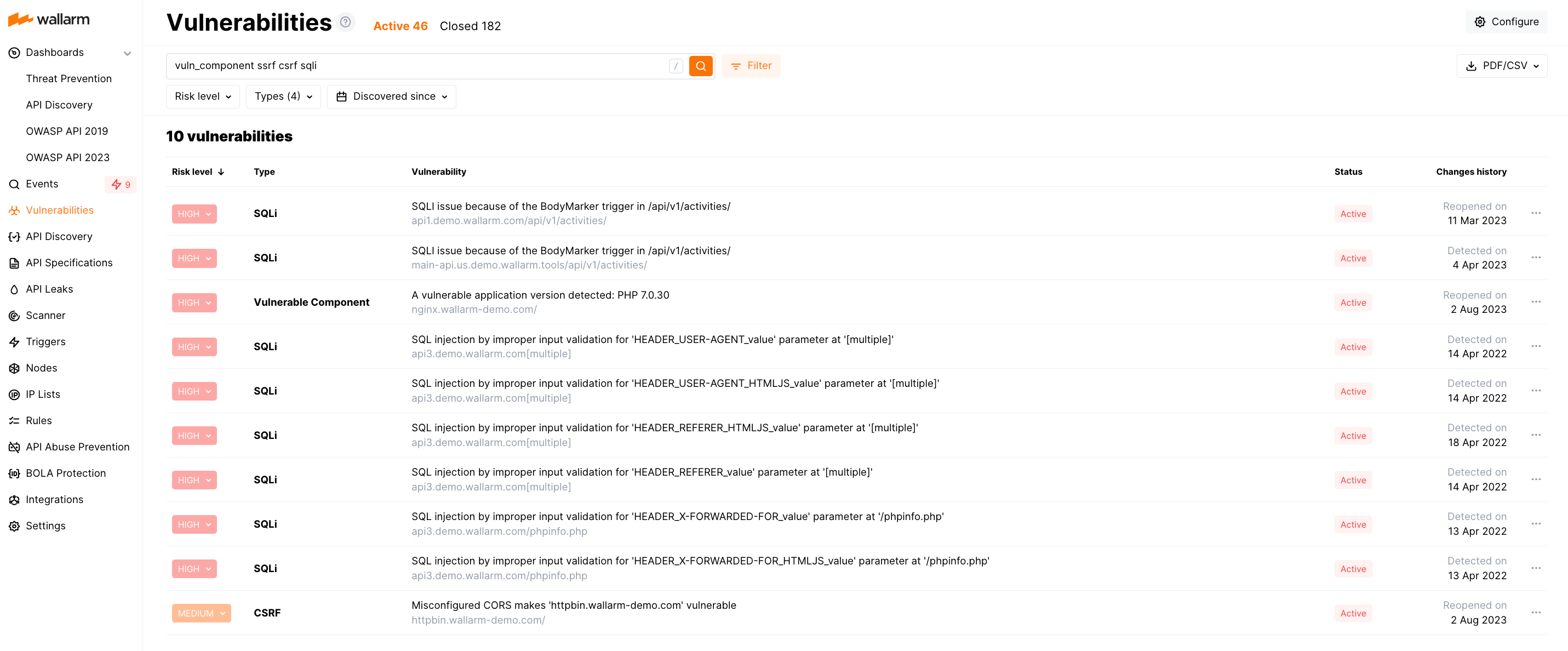
Managing deployed risk is the first line of defense, but reducing the risk exhibited by product applications and APIs is the most effective way to reduce incidents. Wallarm closes the loop on application and API security by providing a suite of testing capabilities to find and eliminate vulnerability risk as follows:
-
Identifies vulnerabilities through passive traffic analysis.
-
Examines identified APIs for weak points.
-
Dynamically creates API security tests from observed traffic.
How Wallarm works¶
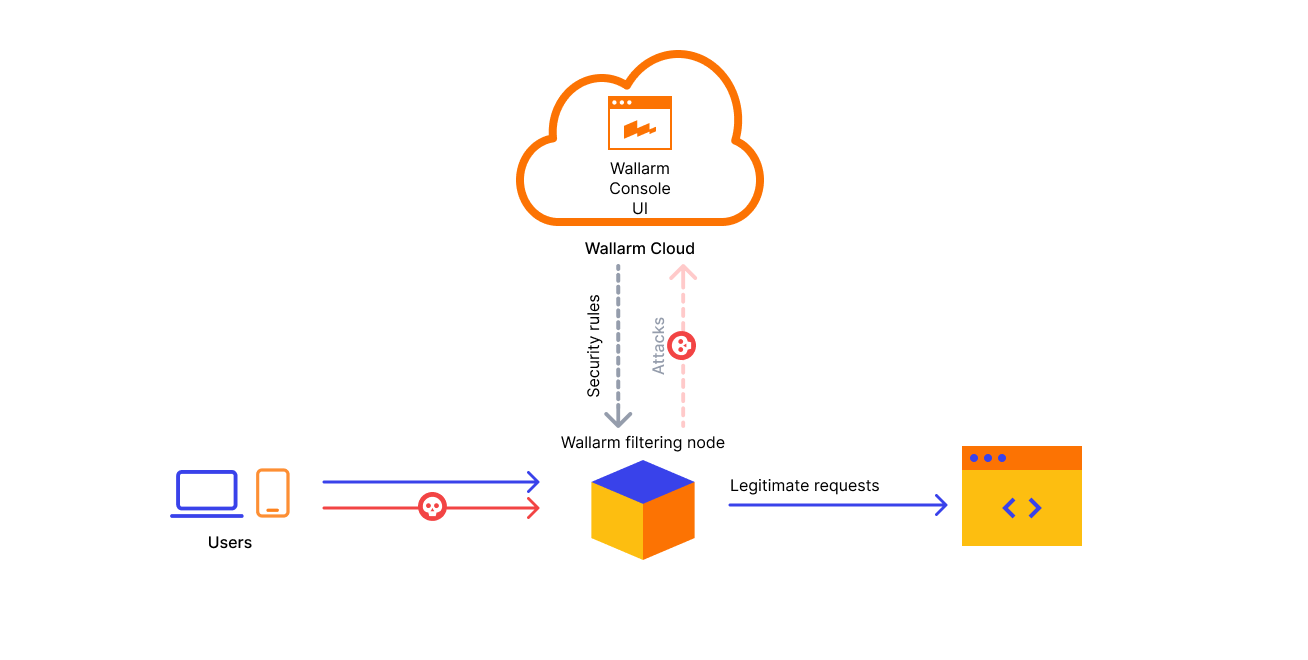
Wallarm's platform is primarily built upon two main components: the Wallarm filtering node and the Wallarm Cloud.
Filtering node¶
Positioned between the Internet and your APIs, the Wallarm filtering node:
-
Analyzes the company's entire network traffic and mitigates malicious requests.
-
Collects the network traffic metrics and uploads the metrics to the Wallarm Cloud.
-
Downloads resource-specific security rules you defined in the Wallarm Cloud and applies them during the traffic analysis.
-
Detects sensitive data in your requests, ensuring it remains secure within your infrastructure and is not transmitted to the Cloud as to a third-party service.
You can set up the Wallarm filtering node within your own network or opt for Wallarm Security Edge via the available deployment choices.
Cloud¶
The Wallarm Cloud does the following:
-
Processes the metrics that the filtering node uploads.
-
Compiles custom resource-specific security rules.
-
Scans the company's exposed assets to detect vulnerabilities.
-
Builds API structure based on the traffic metrics received from the filtering node.
-
Houses the Wallarm Console UI, your command center for navigating and configuring the Wallarm platform, ensuring you have a comprehensive view of all security insights.
Wallarm offers cloud instances in both the US and Europe, enabling you to select the best fit considering your data storage preferences and regional service operation requirements.
Proceed to signup on the US Wallarm Cloud
Proceed to signup on the EU Wallarm Cloud
Where Wallarm works¶
The described Wallarm components: filtering node and Cloud - can be deployed in one of three forms:
-
Security Edge: complete cloud-based deployment. Both Wallarm filtering nodes and Wallarm Cloud components are managed by Wallarm.
-
Hybrid: Wallarm clients deploy and manage the Wallarm filtering nodes, and Wallarm manages the Wallarm Cloud component.
-
On-Premise: both Wallarm filtering node and Wallarm Cloud components are hosted and managed by the client.