Credential Stuffing Detection  ¶
¶
Credential stuffing is a cyber attack where hackers use lists of compromised user credentials to gain unauthorized access to user accounts on multiple websites. This article describes how to detect this type of threats using Wallarm's Credential Stuffing Detection.
A credential stuffing attack is hazardous because of the common practice of reusing identical usernames and passwords across different services, along with the tendency to choose easily guessable (weak) passwords. A successful credential stuffing attack requires fewer attempts, so attackers can send requests much less frequently, which makes standard measures like brute force protection ineffective.
How Wallarm addresses credential stuffing¶
Wallarm's Credential Stuffing Detection collects and displays real-time information about attempts to use compromised or weak credentials to access your applications. It also enables instant notifications about such attempts and forms downloadable list of all compromised or weak credentials providing access to your applications.
To identify compromised and weak passwords, Wallarm uses a comprehensive database of more than 850 million records collected from the public HIBP compromised credentials database.
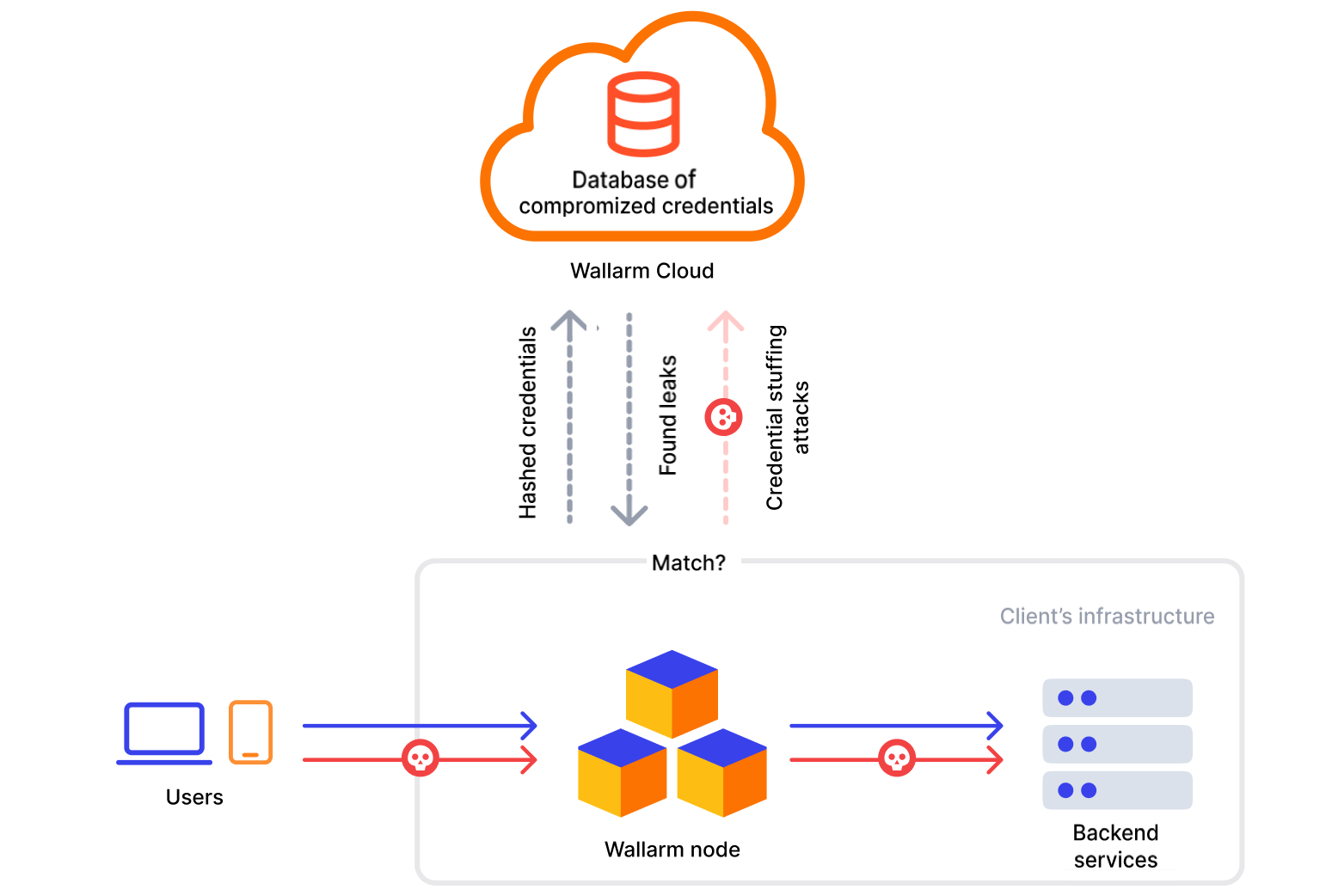
Wallarm's Credential Stuffing Detection keeps credentials data safe applying the following sequence of actions:
-
As the request arrives at the node, it generates SHA-1 from the password and sends several chars to the Cloud.
-
Cloud checks its database of known compromised passwords looking for those starting with the received chars. If found, they are sent to the node in the SHA-1 encrypted format, and the node compares them to the password from the request.
-
If it is a match, the node reports a credential stuffing attack to the Cloud, including the login taken from the request to this attack information.
-
The node passes the request to the application.
Thus, passwords from machines with Wallarm nodes are never sent to the Wallarm Cloud unencrypted. Credentials are not sent simultaneously, ensuring clients' authorization data remains secure within your network.
Mass and single attempts
Credential Stuffing Detection is capable of registering both massive attempts of usage of the compromised credentials performed by bots and single attempts, undetectable by other means.
Mitigation measures
Knowledge of accounts with stolen or weak passwords allows you to initiate measures to secure these accounts' data, like communicating with account owners, temporarily suspending access to the accounts, etc.
Wallarm does not block requests with compromised credentials to avoid blocking legitimate users even if their passwords are weak or were compromised. However, note that credential stuffing attempts can be blocked if:
-
They are part of detected malicious bot activity and you have enabled the API Abuse Prevention module.
-
They are part of requests with other attack signs.
Enabling¶
To enable Wallarm's Credential Stuffing Detection:
-
Make sure your subscription plan includes Credential Stuffing Detection. To change the subscription plan, please send a request to sales@wallarm.com.
-
Ensure your Wallarm node is version 4.10 or higher, deployed using one of the specified artifacts:
-
Check that your user's role allows configuring Credential Stuffing Detection.
-
In Wallarm Console → Credential Stuffing, enable the functionality (disabled by default).
Once Credential Stuffing Detection is enabled, a configuration is needed for it to start working.
Configuring¶
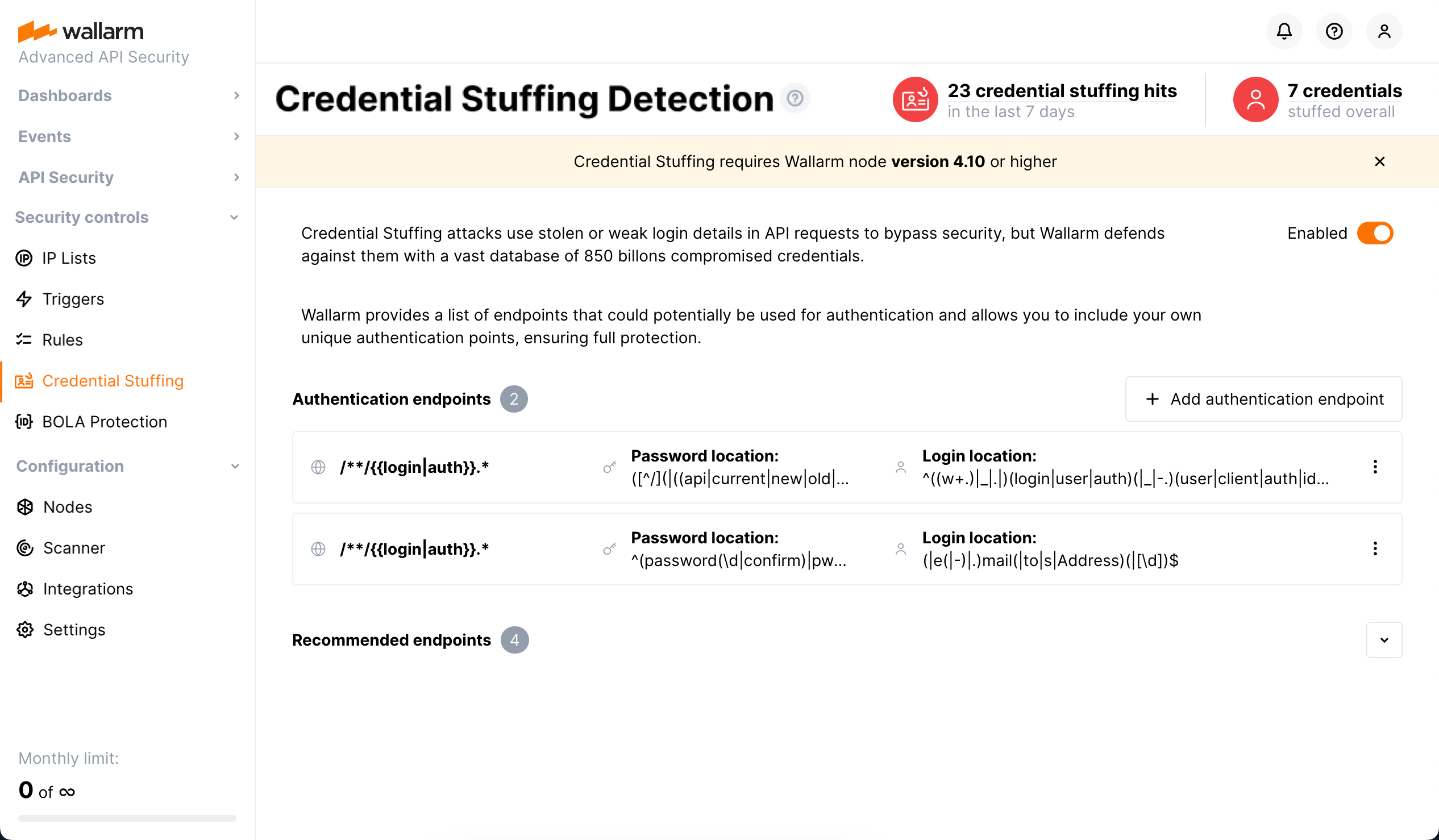
You need to form the list of authentication endpoints to be checked for attempts of compromised credentials usage. To form the list, navigate to Wallarm Console → Credential Stuffing.
There are two ways of adding endpoints to the list:
-
From the Recommended endpoints list that includes two types of elements:
- Wallarm's predefined rules utilizing regular expressions to specify commonly used authentication endpoints and their parameters storing passwords and logins.
- Endpoints used for authentication that were found by the API Discovery module and recorded as they actually received traffic.
- Wallarm's predefined rules utilizing regular expressions to specify commonly used authentication endpoints and their parameters storing passwords and logins.
-
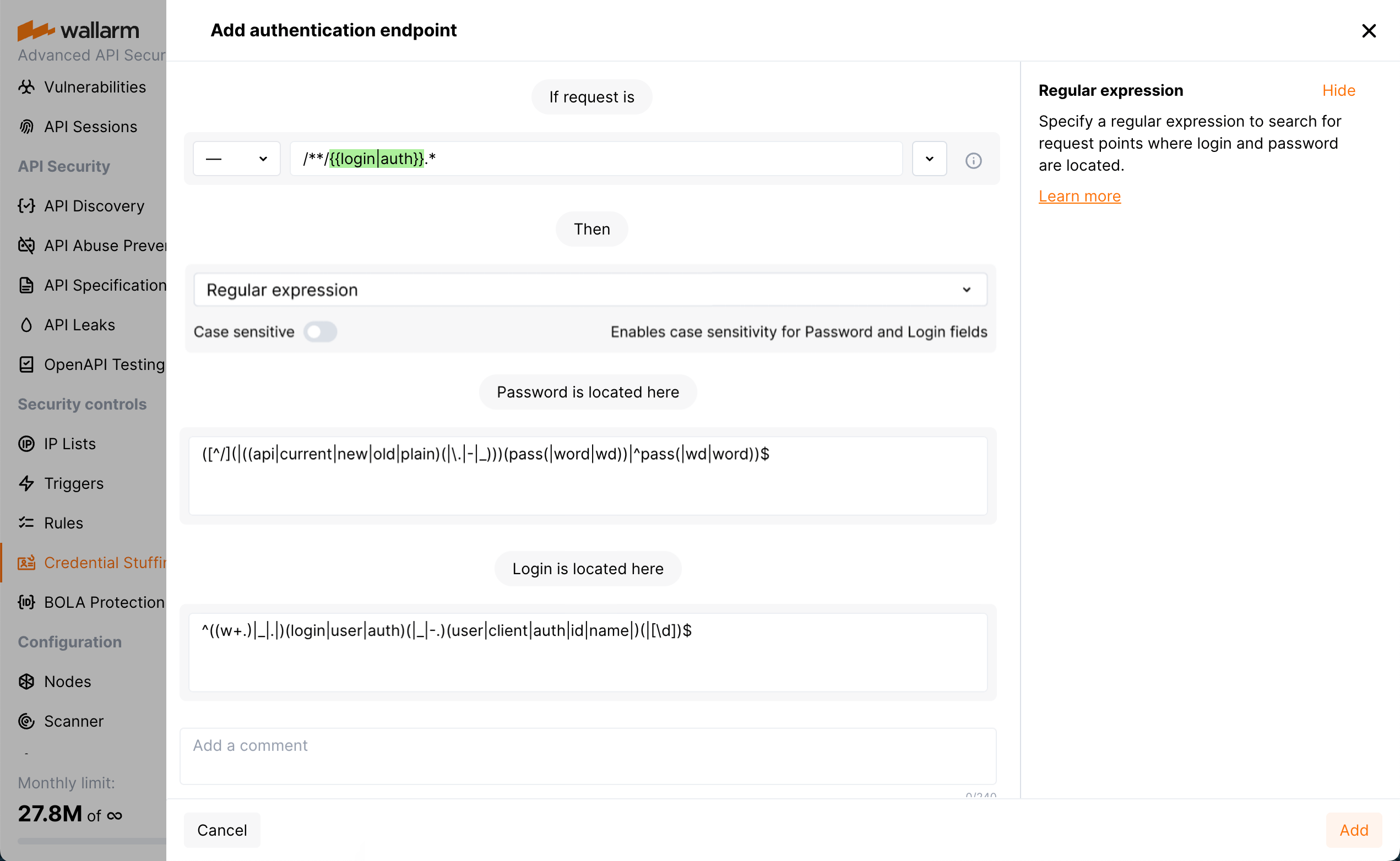
Manually - you can also include your own unique authentication endpoints, ensuring full protection. When adding manually, set URI and the way of searching for authentication parameters:
- By Exact location of parameters - you will need to indicate the exact endpoint request points where password and login are located.
-
By Regular expression - endpoint parameters with password and login will be searched using regular expression.
- By Exact location of parameters - you will need to indicate the exact endpoint request points where password and login are located.
Viewing compromised credentials usage attempts¶
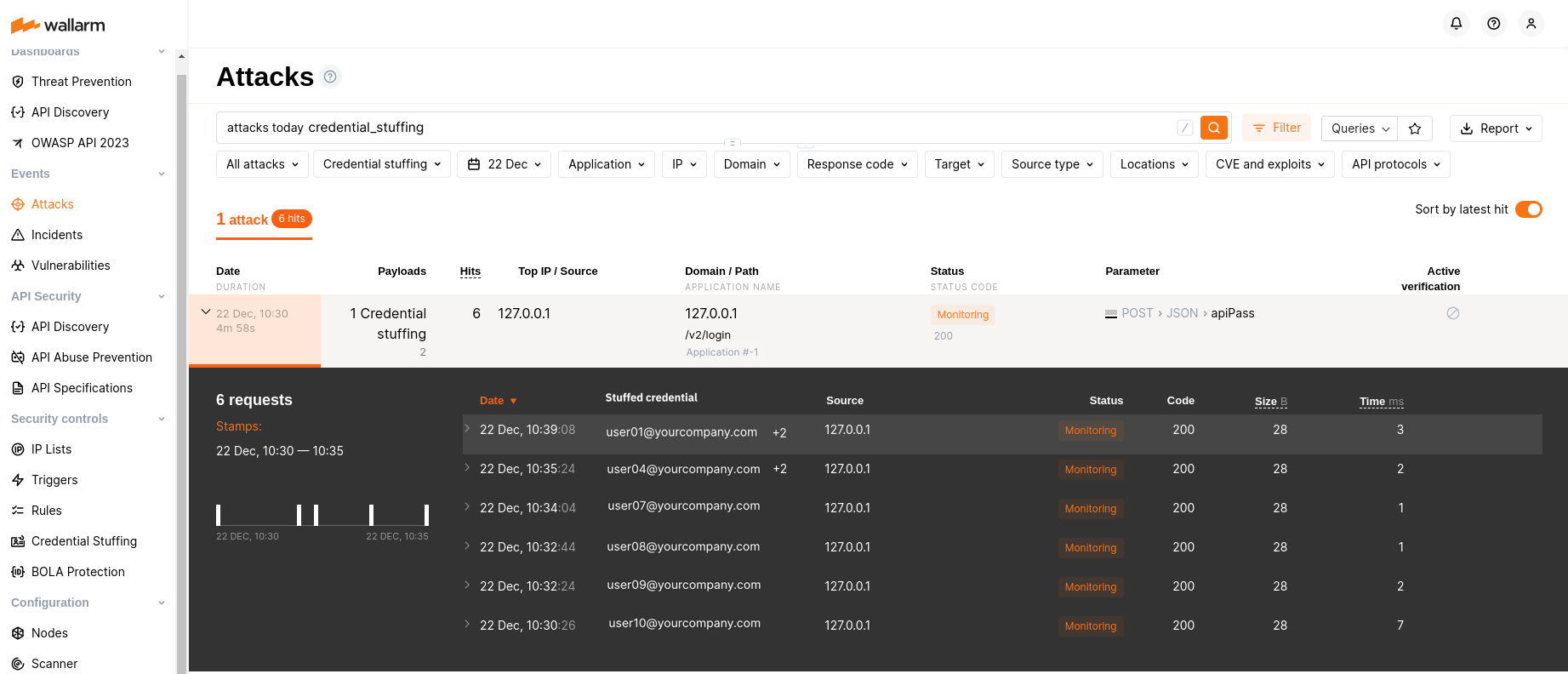
The number of attempts to use compromised credentials in the last 7 days is displayed in the Credential Stuffing section. Click the counter and you will be redirected to the Attacks section that will display all credential_stuffing attacks for the last 7 days.
Expand any of the attacks to see the list of logins which passwords were compromised.
Getting CSV list of compromised credentials¶
The overall number of compromised credentials is displayed in the Credential Stuffing section. Click the counter and your browser will download the CSV file with the list of compromised credentials.
Getting notified¶
You can get immediate notifications about attempts to use the compromised credentials to your email, messenger or one of your integrated systems. To enable such notifications, in the Triggers section of Wallarm Console, configure one or more triggers with the Compromised user account condition.
You can narrow notifications by the application or host that you want to monitor and by the response type.
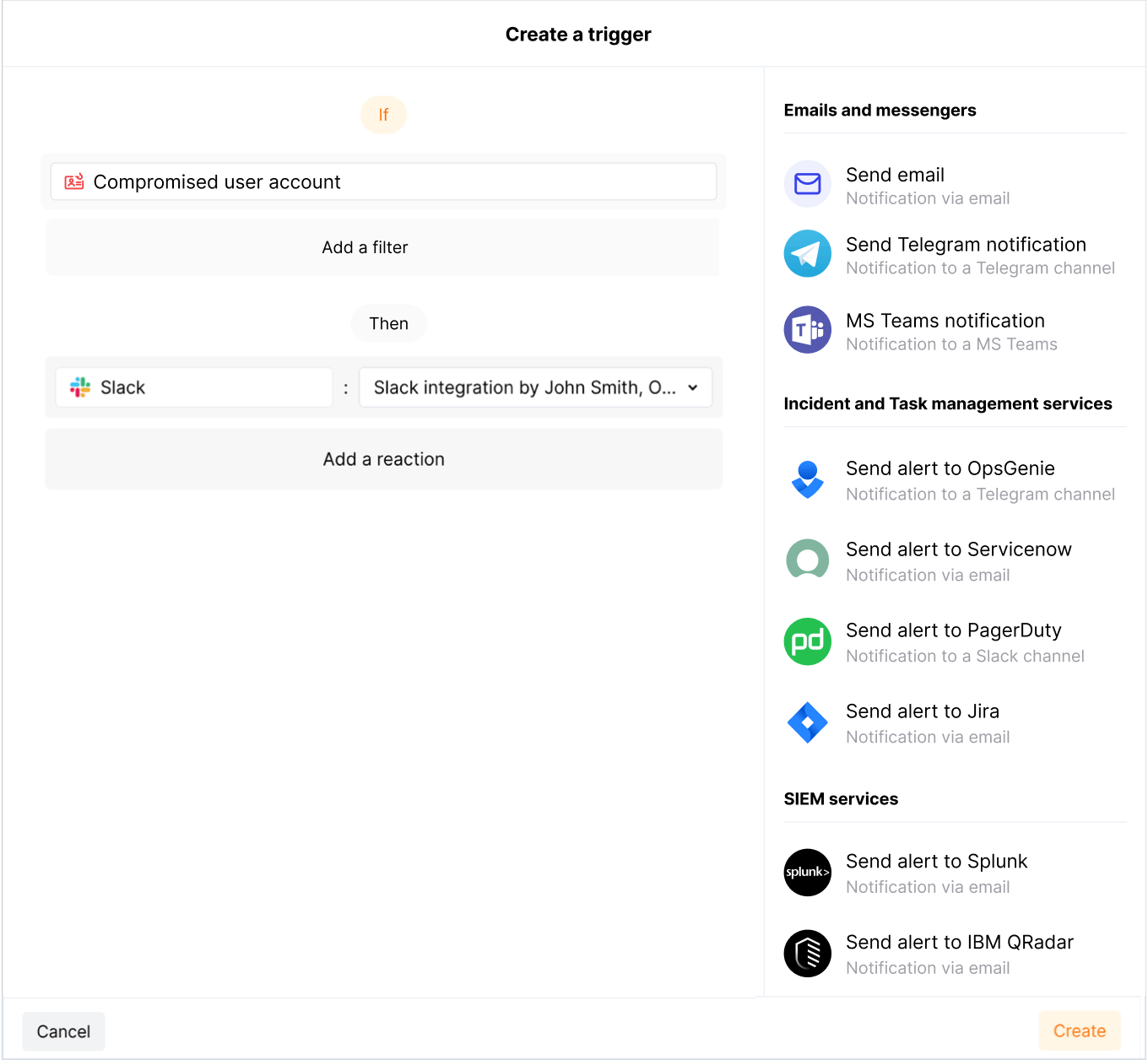
Trigger example: notification about an attempt to use compromised credentials in Slack
In this example, if a new attempt to use compromised credentials is detected, a notification about this will be sent to your configured Slack channel.
To test the trigger:
-
Go to Wallarm Console → Integrations in the US or EU cloud, and configure integration with Slack.
-
In the Credential Stuffing section, make sure Credential Stuffing is enabled, and the following Wallarm's predefined rule is added from the Recommended endpoints to the active Authentication endpoints:
Request is:
Password is located here:
Login is located here:
-
In the Triggers section, create a trigger as shown above, map it to your own Slack integration.
-
Send a request containing compromised credentials to you node's
localhost/loginendpoint: -
In the Attacks section, check that your request has been registered as the event of the
credential_stuffingtype: attempt to use the compromised credentials. -
Expand the attack to make sure it contains the compromised login information.
-
Check messages in your Slack channel. The new message should look like this:
[wallarm] Stolen credentials detected Notification type: compromised_logins Stolen credentials have been detected in your incoming traffic: Compromised accounts: user-01@company.com Associated URL: localhost/login Link: https://my.wallarm.com/attacks/?q=attacks+d%3Alocalhost+u%3A%2Flogin+statuscode%3A404+application%3Adefault+credential_stuffing+2024%2F01%2F22 Client: YourCompany Cloud: EU
Limitations¶
Currently, the Credential Stuffing Detection module is not supported on Wallarm nodes deployed via Terraform module for AWS.