Wallarm API Protection  ¶
¶
Wallarm's API Protection is an advanced set of API and AI protection capabilities. While basic cloud-native WAAP protection already includes support for all API protocols and their inspection for attacks, protection against L7 DDoS, etc., modern APIs are subject to additional risks such as automated threats, API misuse and AI exploitation. The Advanced API Security bundle provides advanced features for more complete risk mitigation.
API Protection includes:
-
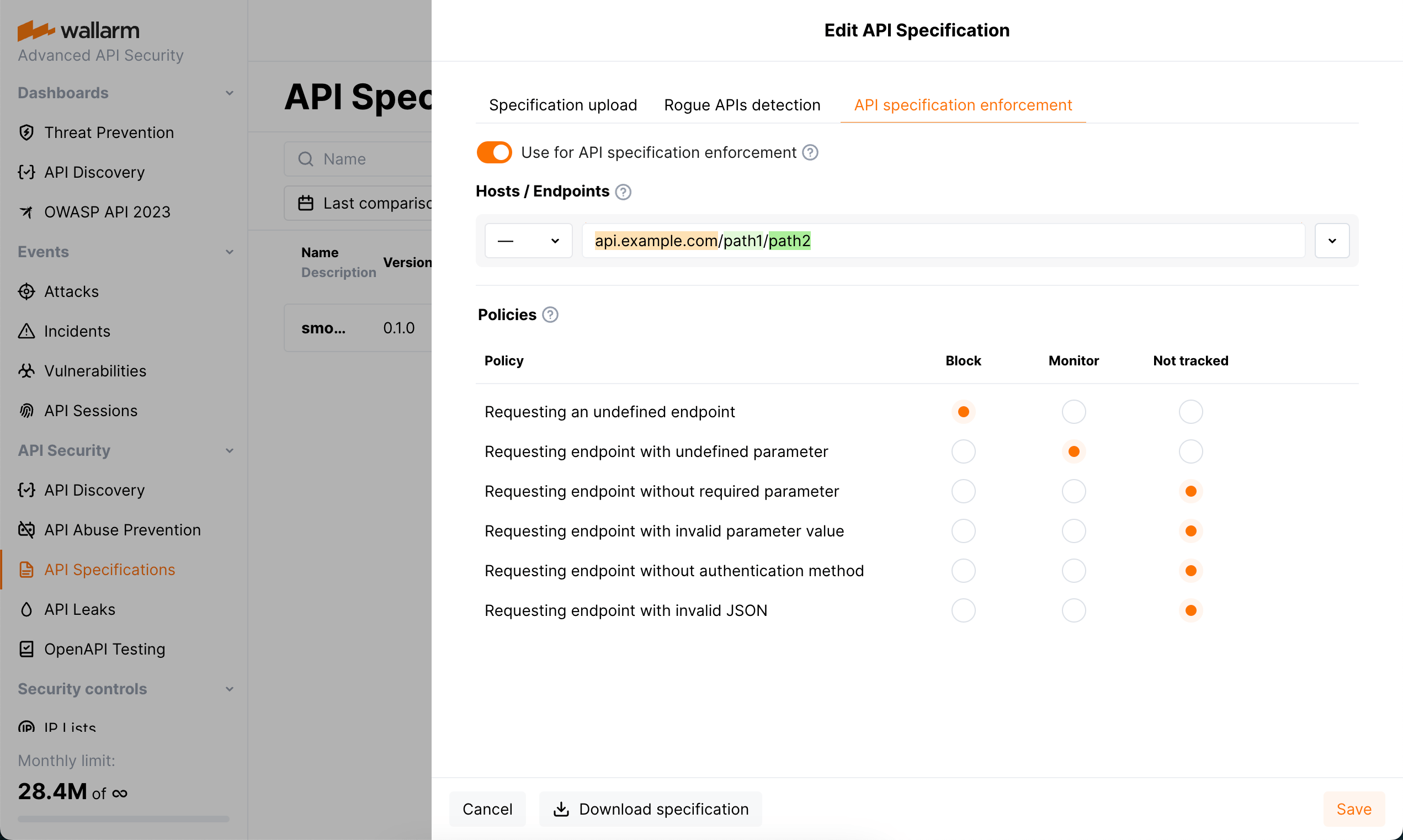
API Specification Enforcement is designed to apply security policies to your APIs basing on your uploaded specifications. It detects discrepancies between the endpoint descriptions in your specification and the actual requests made to your REST APIs and take predefined actions if discrepancies are found.
-
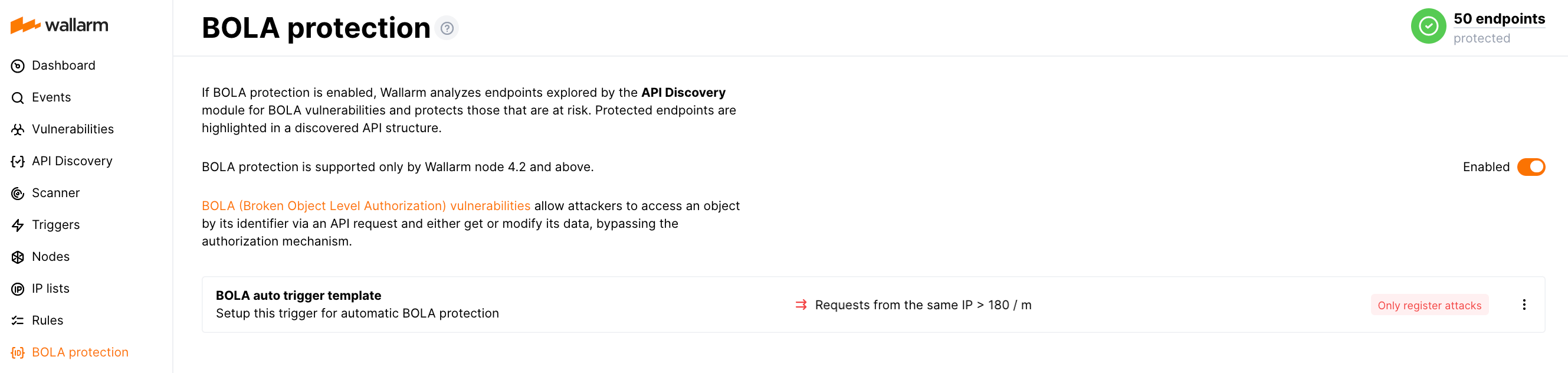
Automatic BOLA Protection provides automatic protection against BOLA attacks that were marked as #1 threat in OWASP API Top 10. Wallarm automatically discovers vulnerable endpoints and protects them against enumeration.
-
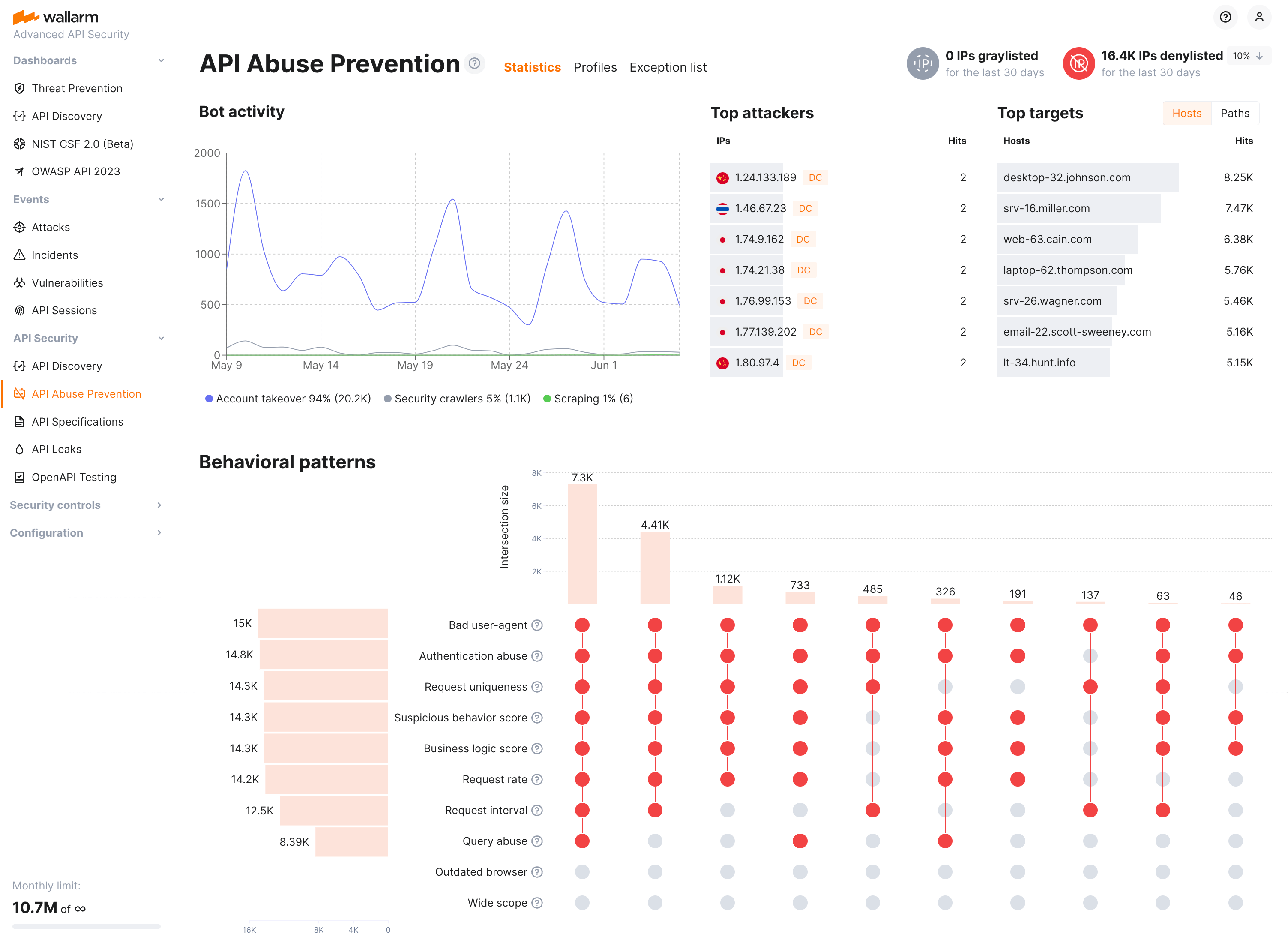
API Abuse Prevention protects your applications and APIs against different types of automated threats. Based on behavioral analysis Wallarm can easily identify and block malicious bots such as Scrappers, Security Crawlers, etc.
-
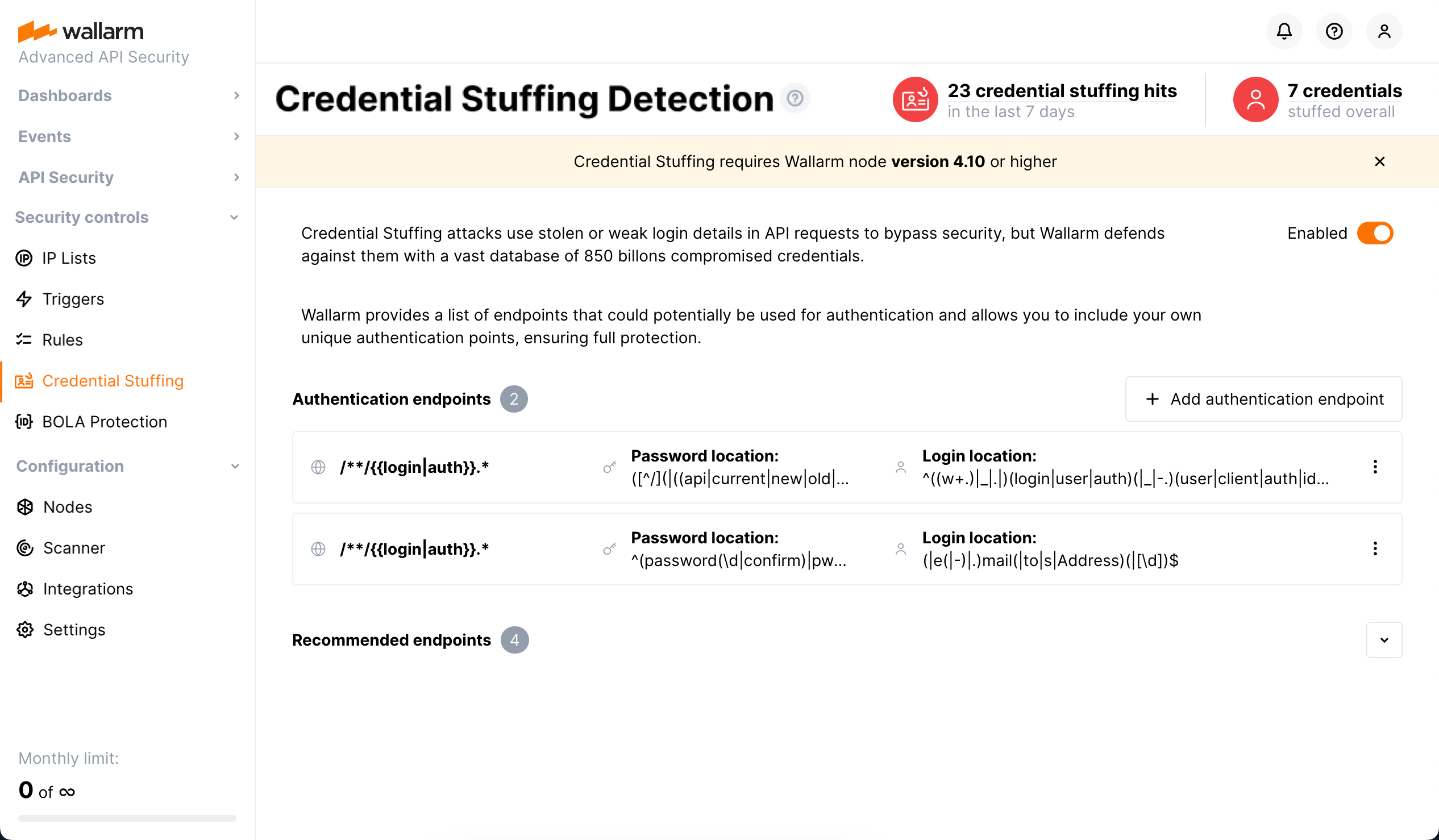
Credential Stuffing Detection provides one more layer of protection against Account Takeover attacks. Wallarm allows you to recognize even a single use of compromised credentials, which is important to identify low and slow Credential Stuffing attacks.
-
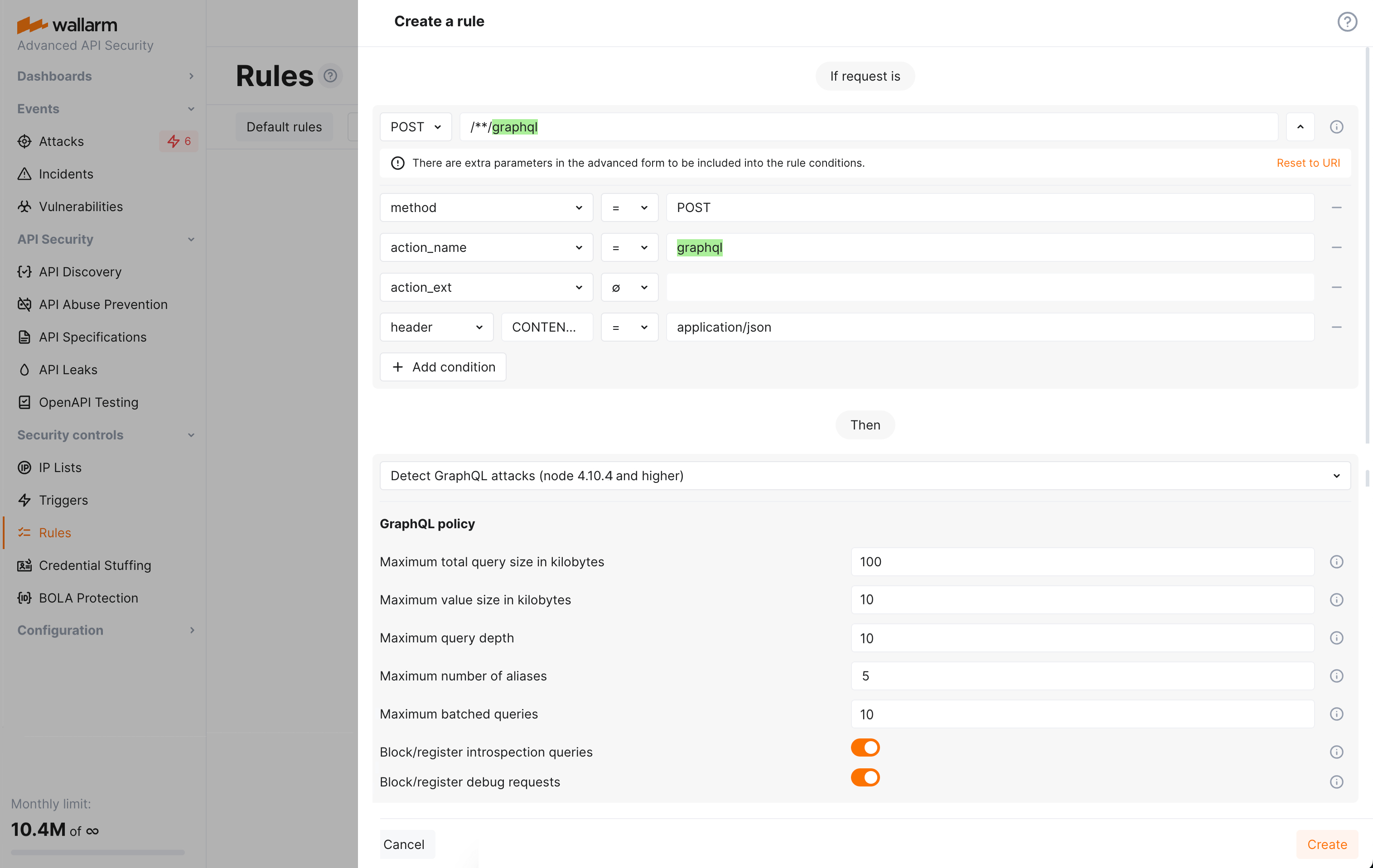
GraphQL API Protection protects your GraphQL APIs against specialized attacks that exploit protocol specific such as batching, nesting queries, introspection, etc. It can prevent Resource Exhaustion, Denial of Service (DoS), Excessive Information Exposure and other attacks.
While WAAP is available under the basic Cloud Native WAAP subscription, tools of the API Protection bundle are the part of the Advanced API Security subscription.
API Specification Enforcement¶
The API Specification Enforcement is designed to apply security policies to your APIs basing on your uploaded specifications. Its primary function is to detect discrepancies between the endpoint descriptions in your specification and the actual requests made to your REST APIs. When such inconsistencies are identified, the system can take predefined actions to address them.
Proceed to detailed description and configuration →
Automatic BOLA Protection¶
Use Wallarm's API Discovery module to discover endpoints vulnerable to broken object level authorization (BOLA) threat and automatically protect from attacks trying to exploit this vulnerability.
Automatic BOLA protection serves as a great extension or replacement to the manually created BOLA protection rules. You can configure automatic BOLA protection to make Wallarm's behavior match your organization security profile.
Proceed to detailed description and configuration →
API Abuse Prevention¶
The API Abuse Prevention delivers detection and mitigation of bots performing API abuse like credential stuffing, fake account creation, content scraping and other malicious actions targeted at your APIs.
API Abuse Prevention uses the complex bot detection model that involves ML-based methods as well as statistical and mathematical anomaly search methods and cases of direct abuse. The module self-learns the normal traffic profile and identifies dramatically different behavior as anomalies.
Proceed to detailed description and configuration →
Credential Stuffing Detection¶
Wallarm's Credential Stuffing Detection collects and displays real-time information about attempts to use compromised or weak credentials to access your applications and enables instant notifications about such attempts. It also forms downloadable list of all compromised or weak credentials providing access to your applications.
To identify compromised and weak passwords, Wallarm uses a comprehensive database of more than 850 million records collected from the public HIBP compromised credentials database.
Proceed to detailed description and configuration →
GraphQL API Protection¶
Wallarm detects regular attacks (SQLi, RCE, etc.) in GraphQL by default even under the basic WAAP subscription plan. However, some aspects of the protocol allow implementing GraphQL specific attacks related to excessive information exposure and DoS.
Wallarm to protect your APIs from these attacks by setting GraphQL policy - a set of limits for the GraphQL requests.