Schema-Based Testing  ¶
¶
Wallarm's Schema-Based Testing is designed to perform dynamic security testing of your applications and APIs to identify a wide range of vulnerabilities - including those outlined in both the OWASP Top 10 and the OWASP API Security Top 10 - through comprehensive, automated tests.
Schema-Based Testing capabilities:
-
Deep, dynamic analysis of API endpoints.
-
Detection of vulnerabilities in the application or API itself, as well as security misconfigurations in the underlying infrastructure or environment.
-
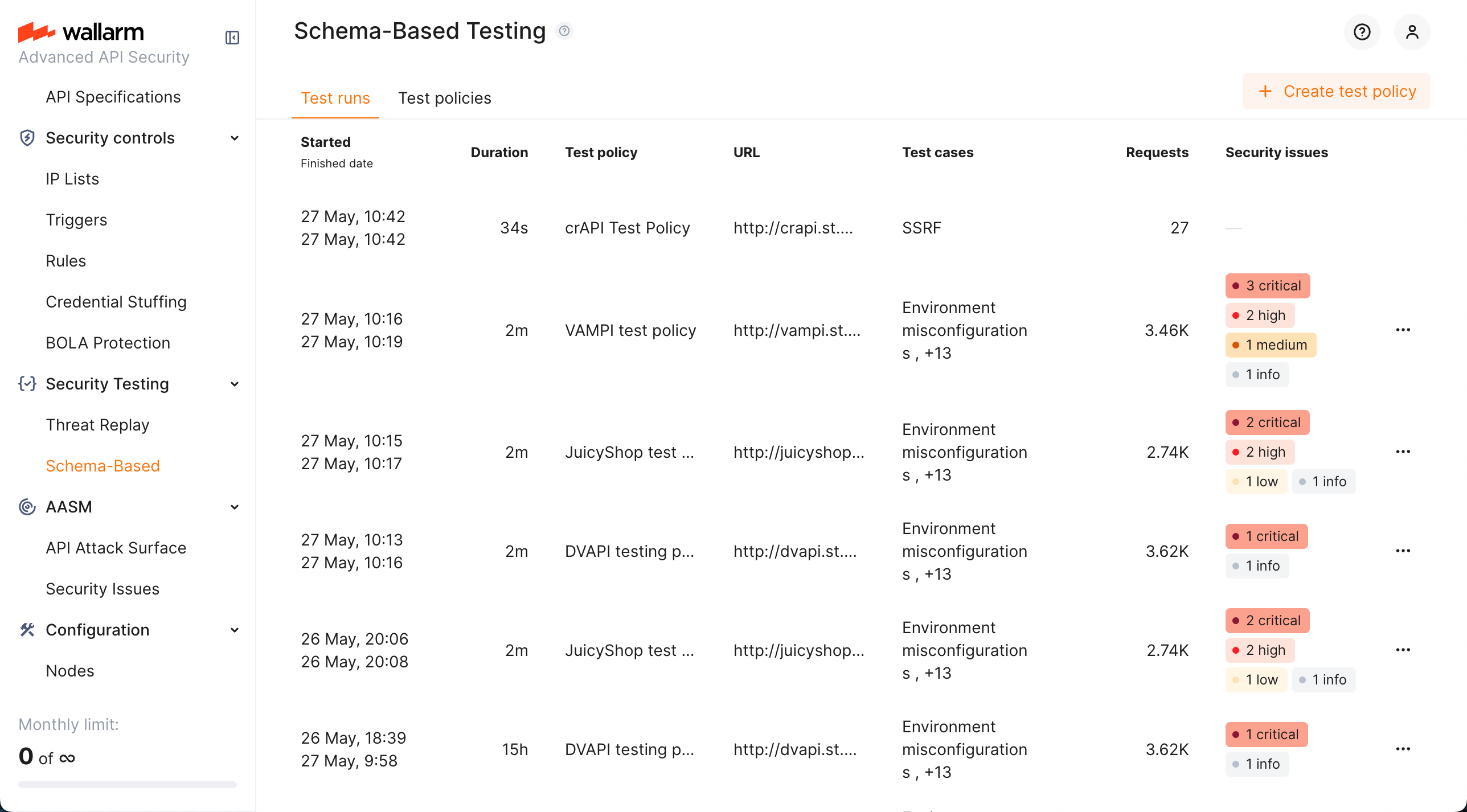
Visualization of found issues in the Wallarm Console's Security Issues section.
-
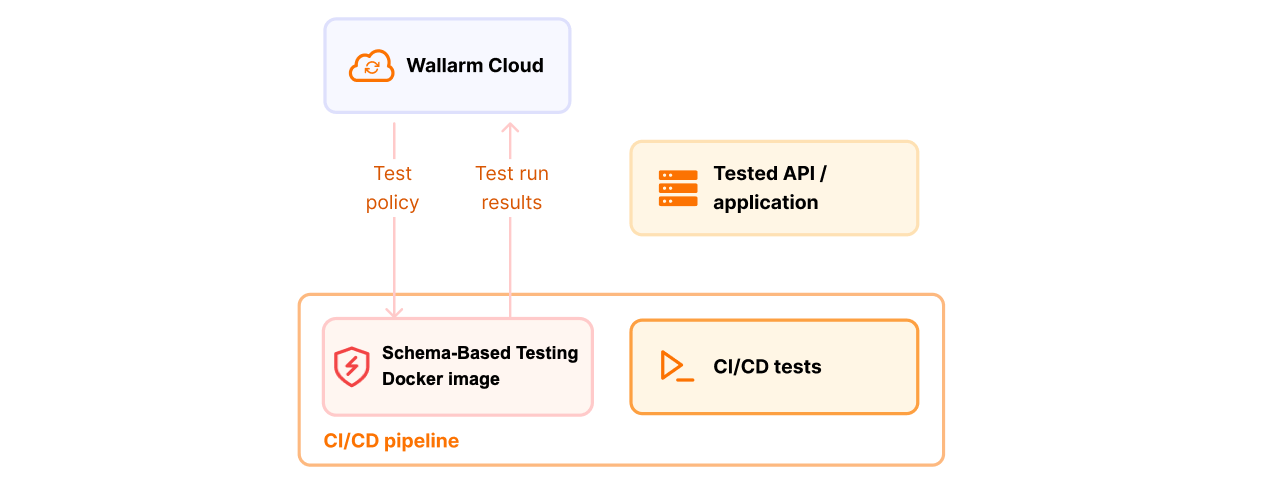
Lightweight execution via Docker container, enabling embedding into your CI/CD pipeline alongside functional tests, smoke test, and other security testing.
How it works¶
Use Schema-Based Testing by fulfilling the following steps:
-
Create test policy: specify the target application, provide its OpenAPI specification or Postman collection, base URL, and select the tests to run.
-
Copy Docker command: find your test policy on the Test policies tab, click it, and copy the provided Docker command.
-
Run and monitor: start the agent with the command. Track progress and view results on the Test runs tab.
Test basis¶
Schema-Based Testing can base its tests on:
-
OpenAPI specification (OAS) - precise and machine-readable blueprint of your API allows to build efficient and reliable test suite for your application. OAS-based testing is focused on input validation, injection, and misconfiguration detection.
-
Postman collection - if you use the Postman API design platform, the functional tests from its collections may be used to build security tests alongside. See details. Postman collection-based testing is focused on complex business logic and access control vulnerabilities.
Test types¶
For OpenAPI specification-based tests, Schema-Based Testing uses three types of tests to detect security issues:
-
Environment misconfiguration tests check for vulnerabilities and misconfigurations in the environment or infrastructure the application and APIs run on (not the API logic). Examples:
- Exposed source code, backups, configuration files.
- Accessible
.git,.env, or system files. - Insecure web server settings (e.g., directory listing, weak TLS).
-
GraphQL vulnerability detection checks for 10 GraphQL most popular misconfigurations (API2, API4).
-
Input parameter tests check each input point (parameters, headers, etc.) defined in the OpenAPI specification for application-level vulnerabilities. Covered vulnerabilities:
- Command injection
- CRLF injection
- LFI / RFI
- NoSQL injection
- Open redirect
- Path traversal
- Remote code execution (RCE)
- SQL injection
- SSRF
- SSTI
- XSS
- XXE
- Infoleak
Enabling and setup¶
To start using Schema-Based Testing, enable and configure it as described in Schema-Based Testing Setup.