The overlimit_res attack detection fine‑tuning¶
The Wallarm node spends limited time on a single incoming request processing and if the time limit is exceeded, marks the request as the resource overlimiting (overlimit_res) attack. The Fine-tune the overlimit_res attack detection rule enables you to customize the time limit allocated for a single request processing and default node behavior when the limit is exceeded.
Limiting the request processing time prevents the bypass attacks aimed at the Wallarm nodes. In some cases, the requests marked as overlimit_res can indicate insufficient resources allocated for the Wallarm node modules resulting in long request processing.
Rule support in different node versions
The Fine-tune the overlimit_res attack detection rule is supported only by the Wallarm node 3.6 and higher.
In versions 3.4 and lower:
- The custom time limit for a single request processing is configured via the
wallarm_process_time_limitNGINX directive and theprocess_time_limitEnvoy parameter. - The
overlimit_resattack processing mode is configured via thewallarm_process_time_limit_blockNGINX directive and theprocess_time_limit_blockEnvoy parameter.
It is recommended to transfer the overlimit_res attack detection configuration from directives to the rule during the Wallarm module upgrade up to the latest version. Relevant instructions are provided for each node deployment option.
Default node behavior¶
The Wallarm node is configured to spend no more than 1,000 milliseconds on a single incoming request processing by default.
If the time limit is exceeded, the Wallarm node:
-
Stops request processing.
-
Marks the request as the
overlimit_resattack and uploads attack details to the Wallarm Cloud.If the processed request part also contains other attack types, the Wallarm node uploads details on them to the Cloud as well.
Attacks of the corresponding types will be displayed in the event list in Wallarm Console.
-
In the monitoring mode, the node forwards the original request to the application address. The application has the risk to be exploited by the attacks included in both processed and unprocessed request parts.
In the safe blocking mode, the node blocks the request if it originates from the graylisted IP address. Otherwise, the node forwards the original request to the application address. The application has the risk to be exploited by the attacks included in both processed and unprocessed request parts.
In the block mode, the node blocks the request.
Request processing in the "Disabled" mode
In the disabled mode, the node does not analyze incoming traffic and, consequently, does not catch the attacks aimed at resource overlimiting.
Changing the default node behavior¶
Risk of protection bypass or running out of system memory
- It is recommended to change the default node behavior only in the strictly specific locations where it is really necessary, e.g. where the upload of the large files is performed, and where there is no risk of protection bypass and vulnerability exploit.
- The high time limit and/or continuation of request processing after the limit is exceeded can trigger memory exhaustion or out-of-time request processing.
The Fine-tune the overlimit_res attack detection rule enables you to change the default node behavior as follows:
-
Set custom limit on a single request processing
-
Stop or continue the request processing when the time limit is exceeded
If the node continues request processing after the time limit has been exceeded, it uploads data on detected attacks to the Cloud only after the request processing is fully completed.
If the rule is set to stop processing, the node stops the request processing once the time limit is exceeded. It then forwards the request unless it is set to record an attack and is in blocking mode. In that case, the node blocks the request and logs the
overlimit_resattack. -
Register the
overlimit_resattack when the request processing time limit is exceeded or notIf the node is configured to register the attack, it either blocks the request or forwards it to the application address depending on the filtration mode.
If the node is not configured to register the attack and the request does not contain other attack types, the node forwards the original request to the application address. If the request contains other attack types, the node either blocks the request or forwards it to the application address depending on the filtration mode
The rule DOES NOT allow to:
- Set the blocking mode for the
overlimit_resattacks separately from other configurations. If the Register and display in the events option is chosen, the node either blocks theoverlimit_resattack or forwards it to the application address depending on the filtration mode set for the corresponding endpoint.
Rule example¶
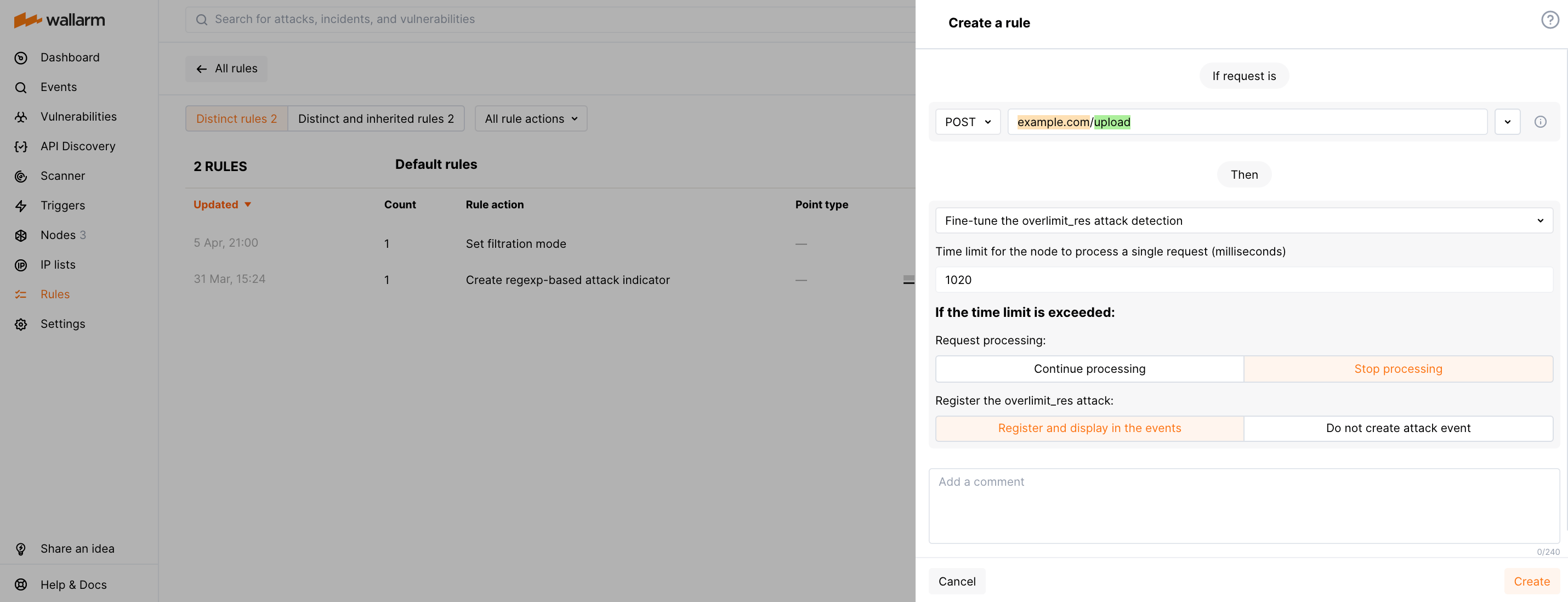
-
The rule increases the time limit for processing each POST request to
https://example.com/uploadup to 1,020 milliseconds. The specified endpoint performs large file uploading. -
Other parameters of the node behavior remain default - if the node processes the request longer than 1,020 milliseconds, it stops the request processing and registers the
overlimit_resattack.