Managing API Leaks¶
The API Leaks module actively scans thousands of public repositories and sources to check for leaks of API tokens, and allows you to block any leaked tokens to prevent attacks or other harm to your API portfolio. This article gives an information on how to manage the API leaks.
For a basic summary of capabilities, please refer to the API Leaks module overview.
Access API Leaks¶
In Wallarm console, use API Leaks section to work as outlined below.
-
To enable the API Leaks module, please send a request to the Wallarm technical support.
-
Only users with the Administrator or Global administrator role can access this section and manage leaks.
-
Users with the Analyst or Global analyst role can access this section, but cannot manage leaks.
New API leaks¶
There are two ways to register new leaks:
-
Automatic - Wallarm actively scans thousands of public repositories and sources and adds new leaks to the list. Sort by Status and view
Openedleaks - they require your attention. -
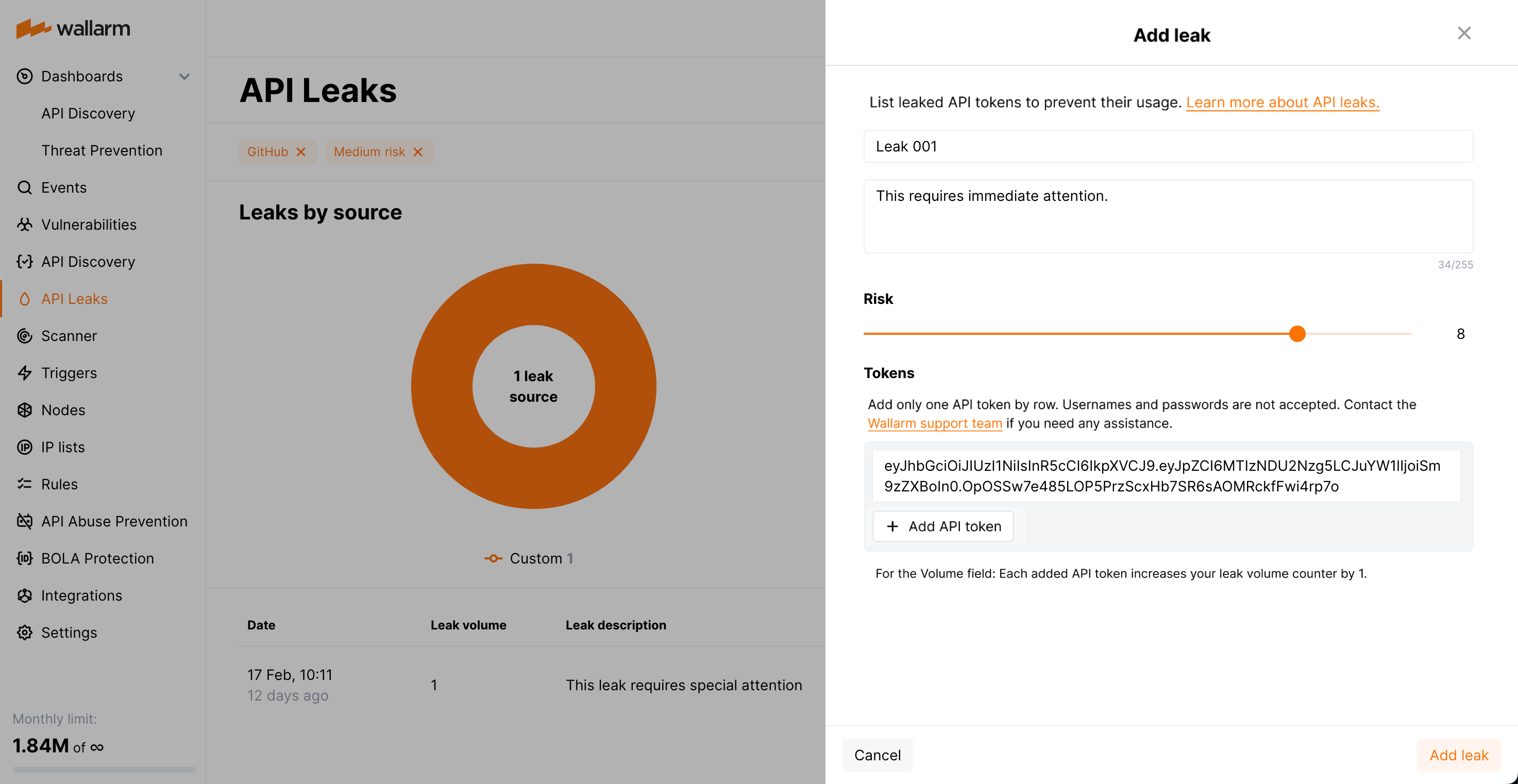
Manual - add API leaks manually. Each one is a set of leaked tokens.
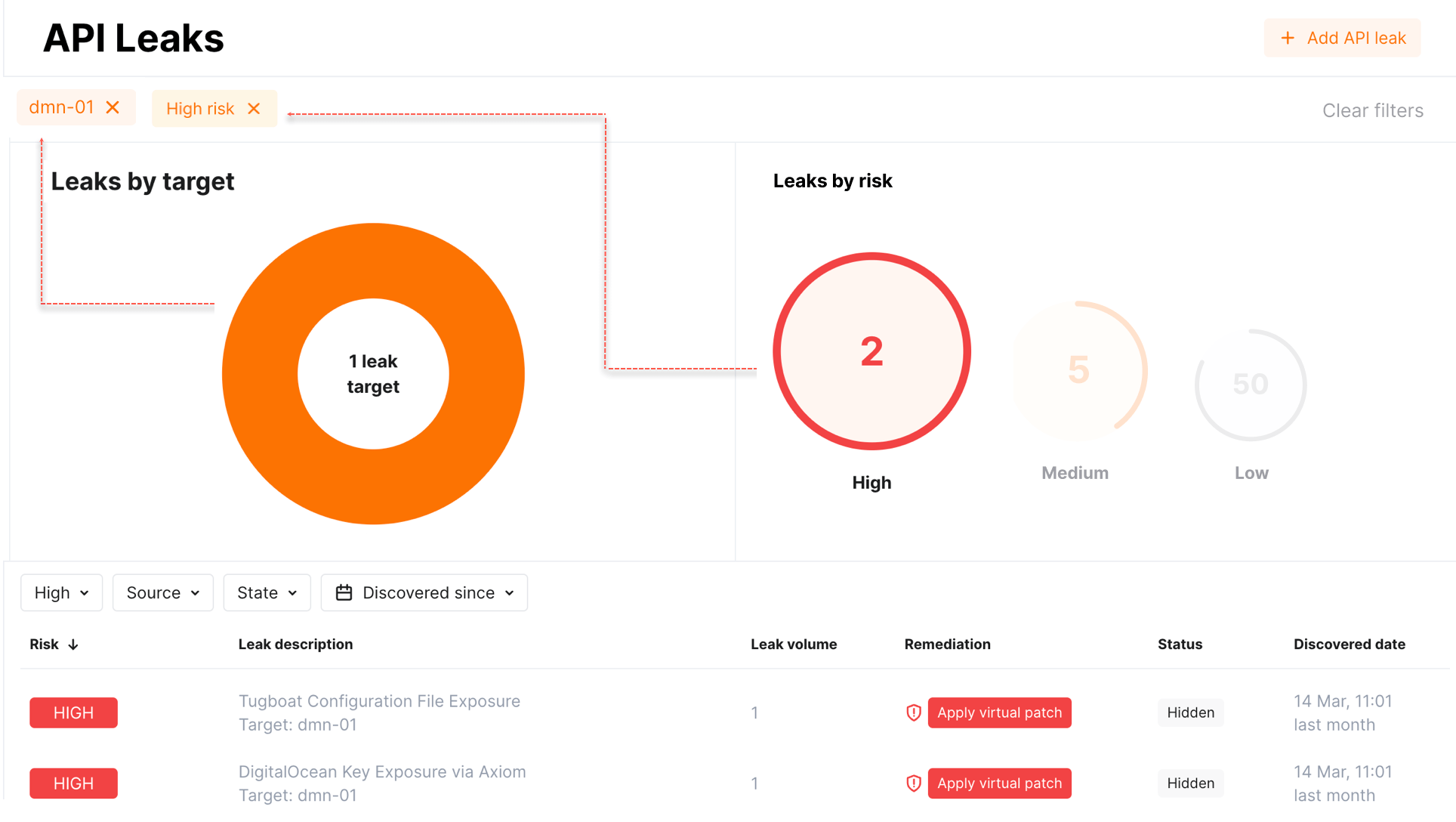
Interactive visualization¶
The API Leaks section provides rich visual representation for your current situation regarding found API leaks. Use the graphics to quickly analyze current situation with found leaks, click diagram elements to filter leaks by risk levels and sources.
Making decisions¶
Regardless of how the API leak was added - automatically or manually - the decision on what to do is always yours. You can manage these decisions as follows:
-
Apply virtual patch to block all attempts of using leaked tokens.
A virtual patch rule will be created.
-
Mark leak as false if you think it was added by mistake.
-
Close leaks to stop protection once all leaked tokens were regenerated or removed. This will remove the virtual patch rule.
-
Even if a leak is closed, it is not deleted. Reopen and then apply remediation to start protection again.
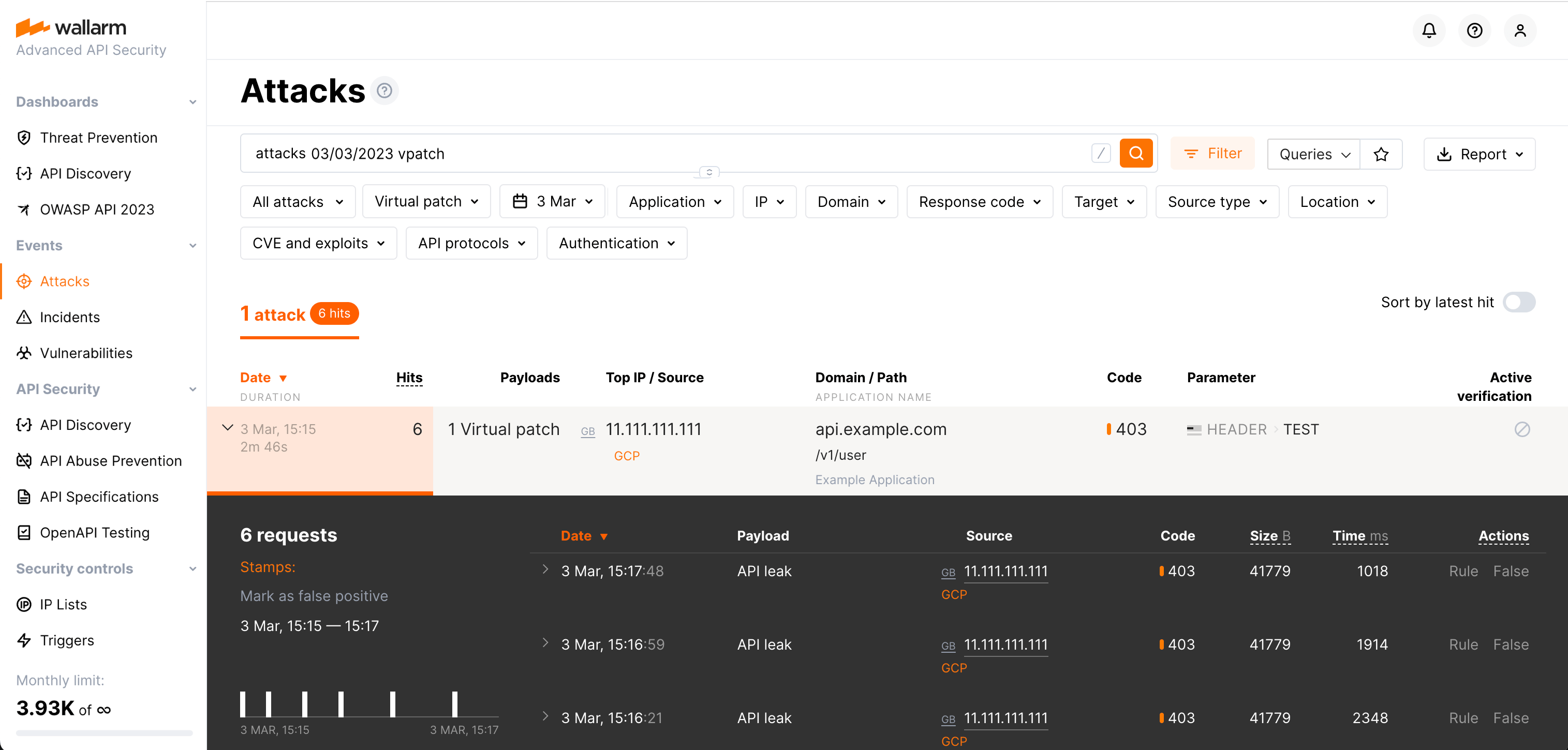
Attempts to use leaked tokens¶
In Wallarm Console → Attacks, set the Type filter to Virtual patch (vpatch) to see all attempts of leaked tokens usage.
For now, you can track the attempts of leaked tokens usage only if vpatch is applied.