Recommendations on Configuring the Filter Node for Separated Environments¶
You have already learned how Wallarm filtering nodes work in separate environments. For the nodes to work as described, learn recommendations on configuring nodes in separated environments from this article.
Initial Wallarm Protection Deployment Process¶
If you perform the initial rollout of Wallarm protection for environments, it is recommended you use the following approach (you are welcome to adjust it as needed):
-
Learn about available Wallarm node deployment options here.
-
If necessary, learn about available options to separately manage the filtering node configuration for your environments. You can find this information here.
-
Deploy Wallarm filtering nodes in your non-production environments with the filtration mode set to
monitoring. -
Learn about how to operate, scale, and monitor the Wallarm solution; confirm the stability of the new network component.
-
Deploy Wallarm filtering nodes in your production environment with the filtration mode set to
monitoring. -
Implement proper configuration management and monitoring processes for the new Wallarm component.
-
Keep the traffic flowing via the filtering nodes in all your environments, including testing and production, for 7-14 days to give the Wallarm cloud‑based backend some time to learn about your application.
-
Enable the
blockingfiltration mode in all your non-production environments and use automated or manual tests to confirm the protected application is working as expected. -
Enable the
blockingfiltration mode in the production environment. Using available methods, confirm that the application is working as expected.
Info
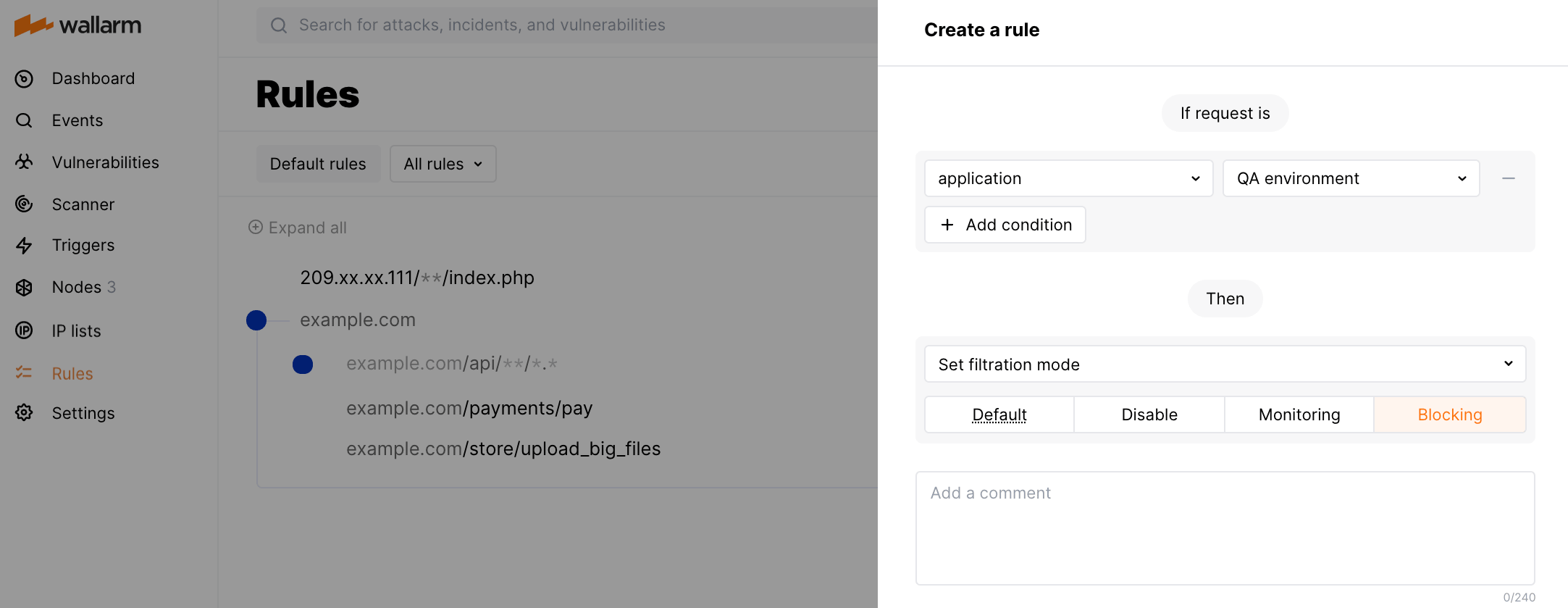
To set up the filtration mode, please use these instructions.
Gradual Rollout of New Wallarm Node Changes¶
From time to time changes might be needed in your existing Wallarm infrastructure. Depending on your organization's change management policy, you might be required to test all potentially risky changes in a non-production environment, and then apply the changes in your production environment.
The following approaches are recommended to test and gradually change the configuration of different Wallarm components and features:
Low-level Configuration of Wallarm Filtering Nodes in All Form-factors¶
Low-level configuration of filtering nodes is performed via Docker environment variables, provided NGINX configuration file, Kubernetes Ingress controller parameters, etc. The way of configuration depends on the deployment option.
Low-level configuration can easily be separately managed for different customer environments using your existing change management processes for infrastructure resources.
Configuration of Wallarm Node Rules¶
Since each rule record can be associated with a different set of application instance IDs or HOST request headers, the following options are recommended:
-
First apply a new configuration to a test or development environment, verify the functionality, and then apply the change for the production environment.
-
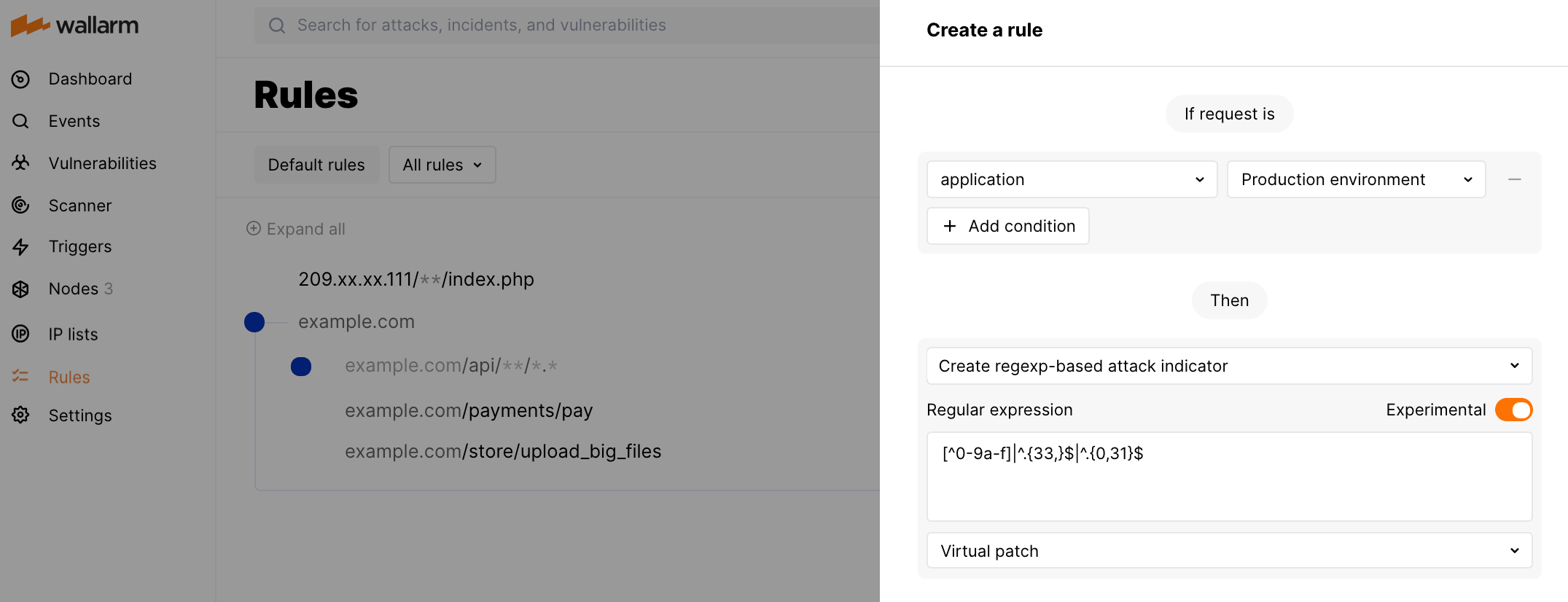
Use the
Create regexp-based attack indicatorrule in theExperimentalmode. This mode allows the rule to be deployed directly in the production environment without the risk of mistakenly blocking valid end user requests. -
Use the
Set filtration moderule to control the Wallarm filtration mode for specific environments and requests. This rule provides additional flexibility in the way Wallarm protection can be gradually rolled out to protect new end-points and other resources in different environments. By default, thewallarm_modevalue is used depending on thewallarm_mode_allow_overridesetting.